审计一套webshell箱子
孤狼写的。
WEBSHELL箱子系统V1.0 纯asp写的。
本文 暗月原创 转载请注明暗月博客 www.moonsec.com
列表文件
inc/checkstr.asp 过滤文件
<% Public Function Checkstr(str) If IsNull(str) Then Checkstr = vbNullString Exit Function End If str = Replace(str, Chr(0), "") str = Replace(str, Chr(34), "") str = Replace(str, "%", "") str = Replace(str, "@", "") str = Replace(str, "!", "") str = Replace(str, "^", "") str = Replace(str, "=", "") str = Replace(str, "--", "") str = Replace(str, "$", "") str = Replace(str, "'", "") str = Replace(str, ";", "") str = Replace(str, "<", "") str = Replace(str, ">", "") str = Replace(str, "chr", "") Checkstr = Trim(str) End Function %>
接收文件
api.asp
<!--#Include File="conn.asp"--> <!--#Include File="inc/Getstr.asp"--> <!--#Include File="inc/checkstr.asp"--> <% On Error Resume Next Dim Rs,SQL,Config set Rs=server.createobject("adodb.recordset") SQL = "SELECT * FROM [YB_Config]" Rs.open SQL,YB_conn,1,3 Config = Rs("PassConfig") dim url,host,pass url = Checkstr(request.QueryString("url")) host = getBody(url,"http://","/",false,false) pass = request.QueryString("pass") if trim(host) = "" then host = "NoHost" end if if trim(pass) = "" then url = "" end if if trim(url) <> "" then set Rs=server.createobject("adodb.recordset") if request("id") = 1 then SQL="SELECT * FROM [YB_Phplist] where url='"& url & "'" else SQL="SELECT * FROM [YB_Asplist] where url='"& url & "'" end if Rs.open SQL,YB_conn,1,3 if Rs.eof then Rs.addnew Rs("url") = url Rs("host") = host Rs("pass") = pass Rs("time") = now() Rs("google") = "Null" Rs("baidu") = "Null" Rs.update else if Config = 1 then Rs("pass") = pass Rs("time") = now() Rs.update end if end if Rs.close set Rs=nothing set YB_conn=nothing else response.Write "提交参数错误" response.End() end if %>
pass可以xss的拉
这里过滤url = Checkstr(request.QueryString("url")) 后面的pass可以xss pass获取虽然有限制 用短网址就可以了

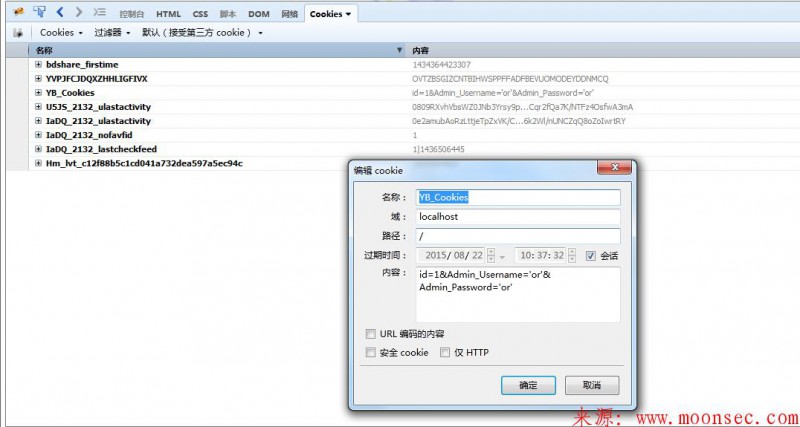
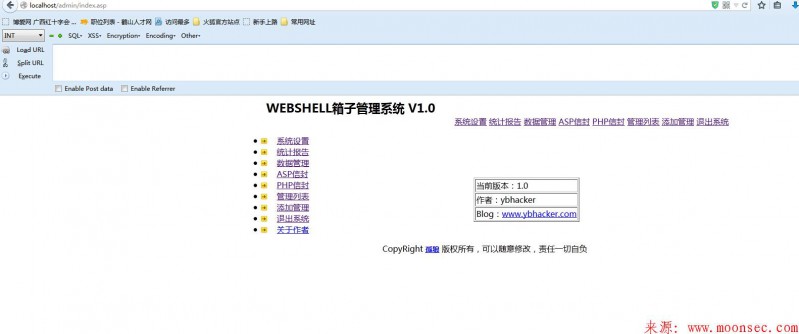
验证登录
check.asp
<!--#Include File="../conn.asp"--> <% If Trim(Request.Cookies("YB_Cookies")) = "" Then response.Redirect "login.asp" response.End() else dim Rs,SQL SQL = "SELECT * FROM [YB_Admin] where [Admin_Username] = '"&Request.Cookies("YB_Cookies")("Admin_Username")&"' and [Admin_Password] = '"&Request.Cookies("YB_Cookies")("Admin_Password")&"'" Set Rs = YB_Conn.Execute(SQL) if Rs.eof then response.Redirect "login.asp" end if end if %>
首先判断是否为空 不为空的情况下 伪造登录用户把。
成功绕过了。
广告:暗月webshell箱子近期已经发布,安全可靠,是你黑吃黑不二之选。
暗月webshell箱子视频演示
http://www.moonsec.com/post-509.html
有意购买箱子 联系QQ:40497992
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论