
OSCP 靶场

靶场介绍
|
uvalde |
easy |
ftp利用、web 渗透、漏洞挖掘、后台爆破、sudo提权、特殊文件提权 |
信息收集
主机发现
端口扫描
└─# nmap -sV -A -p- -T4 192.168.1.217
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-03 03:39 EST
Nmap scan report for 192.168.1.217
Host is up (0.00057s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.1.158
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1000 1000 5154 Jan 28 2023 output
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 3a:09:a4:da:d7:db:99:ee:a5:51:05:e9:af:e7:08:90 (RSA)
| 256 cb:42:6a:be:22:13:2c:f2:57:f9:80:d1:f7:fb:88:5c (ECDSA)
|_ 256 44:3c:b4:0f:aa:c3:94:fa:23:15:19:e3:e5:18:56:94 (ED25519)
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-title: Agency - Start Bootstrap Theme
|_http-server-header: Apache/2.4.54 (Debian)
MAC Address: 08:00:27:86:DA:4D (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.57 ms 192.168.1.217
这里有个ftp有个匿名访问,里面有个output 文件,记录一些登录后的操作,我们先放着。
目录扫描
gobuster dir -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.1.217 -x php,txt,html -e这里发现一个任意注册接口,发现存在一定的规律,创建成功后会以bash64的方式返回账号密码
http://192.168.1.217/success.php?dXNlcm5hbWU9dGVzdCZwYXNzd29yZD10ZXN0MjAyNEA4NDEx
http://192.168.1.217/success.php?dXNlcm5hbWU9dGVzdDEmcGFzc3dvcmQ9dGVzdDEyMDI0QDgwNjA=
http://192.168.1.217/success.php?dXNlcm5hbWU9dGVzdDImcGFzc3dvcmQ9dGVzdDIyMDI0QDMwMDk=解码后,发现密码的规律是用户名+2024@四位随机数
本来想尝试能不能进行密码覆盖,发现还有一个用户名遍历漏洞
使用普通账号登录后没有任何功能
爆破admin、matthew账号
两个账号登录后同样没有任何功能
权限获取
使用网站后台爆破的账号密码成功登录到ssh matthew 账号
权限提升
这里有个勒索程序
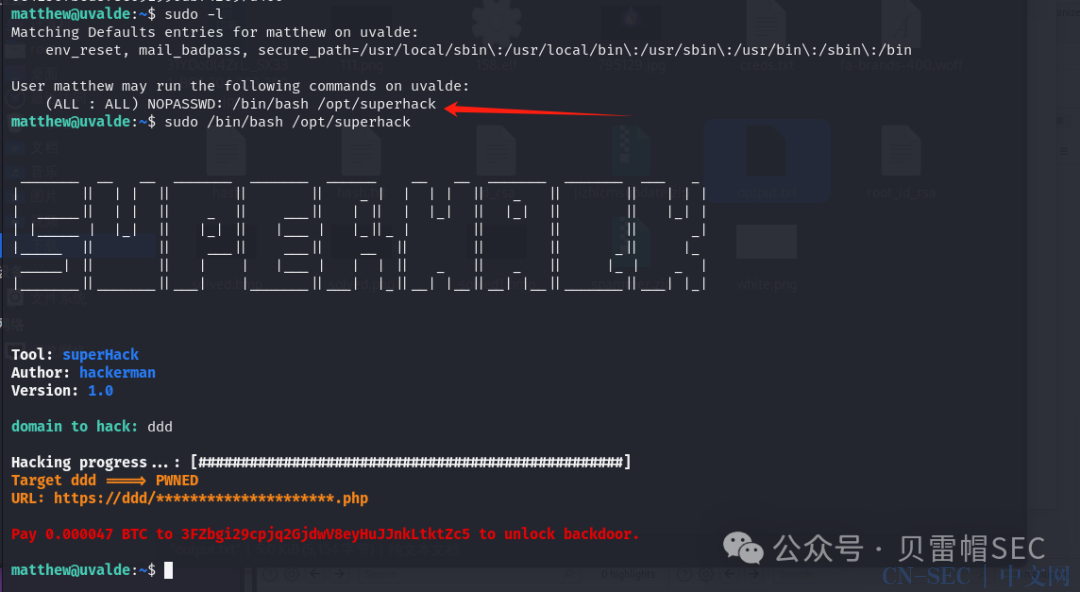
不过这里写什么并不重要,重要的是我们可以修改该文件。
#! /bin/bash
clear -x
GRAS=$(tput bold)
JAUNE=$(tput setaf 3)$GRAS
BLANC=$(tput setaf 7)$GRAS
BLEU=$(tput setaf 4)$GRAS
VERT=$(tput setaf 2)$GRAS
ROUGE=$(tput setaf 1)$GRAS
RESET=$(tput sgr0)
cat << EOL
_______ __ __ _______ _______ ______ __ __ _______ _______ ___ _
| || | | || || || _ | | | | || _ || || | | |
| _____|| | | || _ || ___|| | || | |_| || |_| || || |_| |
| |_____ | |_| || |_| || |___ | |_||_ | || || || _|
|_____ || || ___|| ___|| __ || || || _|| |_
_____| || || | | |___ | | | || _ || _ || |_ | _ |
|_______||_______||___| |_______||___| |_||__| |__||__| |__||_______||___| |_|
EOL
printf "${BLANC}Tool:${RESET} ${BLEU}superHack${RESET}n"
printf "${BLANC}Author:${RESET} ${BLEU}hackerman${RESET}n"
printf "${BLANC}Version:${RESET} ${BLEU}1.0${RESET}n"
printf "n"
[[ $# -ne 0 ]] && echo -e "${BLEU}Usage:${RESET} $0 domain" && exit
while [ -z "$domain" ]; do
read -p "${VERT}domain to hack:${RESET} " domain
done
printf "n"
n=50
string=""
for ((i=0; i<$n; i++))
do
string+="."
done
for ((i=0; i<$n; i++))
do
string="${string/./#}"
printf "${BLANC}Hacking progress...:${RESET} ${BLANC}[$string]${RESET}r"
sleep .09
done
printf "n"
printf "${JAUNE}Target $domain ====> PWNED${RESET}n"
printf "${JAUNE}URL: https://$domain/*********************.php${RESET}n"
echo -e "n${ROUGE}Pay 0.000047 BTC to 3FZbgi29cpjq2GjdwV8eyHuJJnkLtktZc5 to unlock backdoor.${RESET}n"
我们将superhack 文件重命名为superhack.back,然后重新创建一个superhack 文件,里面写入bash,然后使用sudo 执行,成功获取root 权限。
End
“点赞、在看与分享都是莫大的支持”
原文始发于微信公众号(贝雷帽SEC):【OSCP】uvalde
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



















评论