作者:Blck![DuomiCms多处SQL注入]()
全局都使用dede的防注入函数,这个就留给大家去想办法了。。
我们跟踪到
duomi/member/member.php
}elseif($action=='chgpwdsubmit') { if(trim($newpwd)<>trim($newpwd2)) { ShowMsg('两次输入密码不一致','-1'); exit(); } if(!empty($newpwd)||!empty($email)) { $pwd = empty($newpwd)?substr(md5($oldpwd),5,20):substr(md5($newpwd),5,20); $dsql->ExecuteNoneQuery("update `duomi_member` set password = '$pwd' ".(empty($email)?'':",email = '$email'")." where id= '$uid'"); ShowMsg('密码修改成功','-1'); exit(); }
更改密码处可以看到都被单引号了。
但是下面的全部没有进行单引号。
[PHP]
纯文本查看复制代码
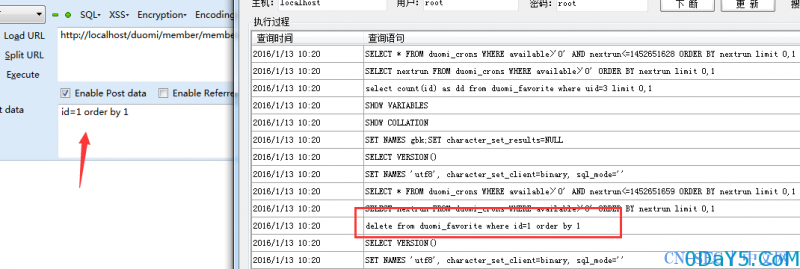
elseif($action=='cancelfav') { $dsql->executeNoneQuery("delete from duomi_favorite where id=".$id);//一处 echo "<script>location.href='?action=favorite'</script>"; exit(); }elseif($action=='cancelfavs') { if(empty($fid)) { showMsg("请选择要取消收藏的视频","-1"); exit(); } foreach($fid as $id) { $dsql->executeNoneQuery("delete from duomi_favorite where id=".$id);//二处 } echo "<script>location.href='?action=favorite'</script>"; exit(); }elseif($action=='favorite') { $pcount = 1; $row=$dsql->getOne("select count(id) as dd from duomi_favorite where uid=".$uid);//三处 $rcount=$row['dd']; if($rcount==0) { echo "<table width=/"100%/" border=/"0/" cellspacing=/"0/" cellpadding=/"0/" ><tr><td align=/"center/">没有收藏的视频</td></tr></table>"; exit(); } $dsql->setQuery("select * from duomi_favorite where uid=".$uid." limit ".($pg-1)*$pcount.",$pcount"); $dsql->Execute('favlist'); ?>
三处都可控,也没有单引号引入,看看SQL执行。
post:
http://localhost/member/member.php?action=cancelfav
id=1 SQL
看看防注入函数:
duomi/duomiphp/sql.class.php
[PHP]
纯文本查看复制代码
function CheckSql($db_string,$querytype='select') { global $cfg_cookie_encode; $clean = ''; $error=''; $old_pos = 0; $pos = -1; $log_file = duomi_INC.'/../data/'.md5($cfg_cookie_encode).'_safe.txt'; $userIP = GetIP(); $getUrl = GetCurUrl(); //如果是普通查询语句,直接过滤一些特殊语法 if($querytype=='select') { $notallow1 = "[^0-9a-z@/._-]{1,}(union|sleep|benchmark|load_file|outfile)[^0-9a-z@/.-]{1,}"; //$notallow2 = "--|//*"; if(m_eregi($notallow1,$db_string)) { fputs(fopen($log_file,'a+'),"$userIP||$getUrl||$db_string||SelectBreak/r/n"); exit("<font size='5' color='red'>Safe Alert: Request Error step 1 !</font>"); } } while (true) { $pos = strpos($db_string, '/'', $pos + 1); if ($pos === false) { break; } $clean .= substr($db_string, $old_pos, $pos - $old_pos); while (true) { $pos1 = strpos($db_string, '/'', $pos + 1); $pos2 = strpos($db_string, '//', $pos + 1); if ($pos1 === false) { break; } elseif ($pos2 == false || $pos2 > $pos1) { $pos = $pos1; break; } $pos = $pos2 + 1; } $clean .= '$s$'; $old_pos = $pos + 1; } $clean .= substr($db_string, $old_pos); $clean = trim(strtolower(preg_replace(array('~/s+~s' ), array(' '), $clean))); if (strpos($clean, 'union') !== false && preg_match('~(^|[^a-z])union($|[^[a-z])~s', $clean) != 0) { $fail = true; $error="union detect"; } elseif (strpos($clean, '/*') > 2 || strpos($clean, '--') !== false || strpos($clean, '#') !== false) { $fail = true; $error="comment detect"; } elseif (strpos($clean, 'sleep') !== false && preg_match('~(^|[^a-z])sleep($|[^[a-z])~s', $clean) != 0) { $fail = true; $error="slown down detect"; } elseif (strpos($clean, 'benchmark') !== false && preg_match('~(^|[^a-z])benchmark($|[^[a-z])~s', $clean) != 0) { $fail = true; $error="slown down detect"; } elseif (strpos($clean, 'load_file') !== false && preg_match('~(^|[^a-z])load_file($|[^[a-z])~s', $clean) != 0) { $fail = true; $error="file fun detect"; } elseif (strpos($clean, 'into outfile') !== false && preg_match('~(^|[^a-z])into/s+outfile($|[^[a-z])~s', $clean) != 0) { $fail = true; $error="file fun detect"; } elseif (preg_match('~/([^)]*?select~s', $clean) != 0) { $fail = true; $error="sub select detect"; } if (!empty($fail)) { fputs(fopen($log_file,'a+'),"$userIP||$getUrl||$db_string||$error/r/n"); exit("<font size='5' color='red'>Safe Alert: Request Error step 2!</font>"); } else { return $db_string; } }
看看兄弟们的姿势吧
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-





评论